Data interaction method based on block chain on-chain and off-chain collaboration
A data interaction and blockchain technology, applied in the field of data interaction based on blockchain chain-off-chain collaboration, can solve problems such as unsuitable storage of large data, network congestion, slow data storage, etc., to ensure data security and completeness, interactive fast effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0034] The data interaction method based on blockchain on-chain and off-chain collaboration of the present invention includes the following steps:
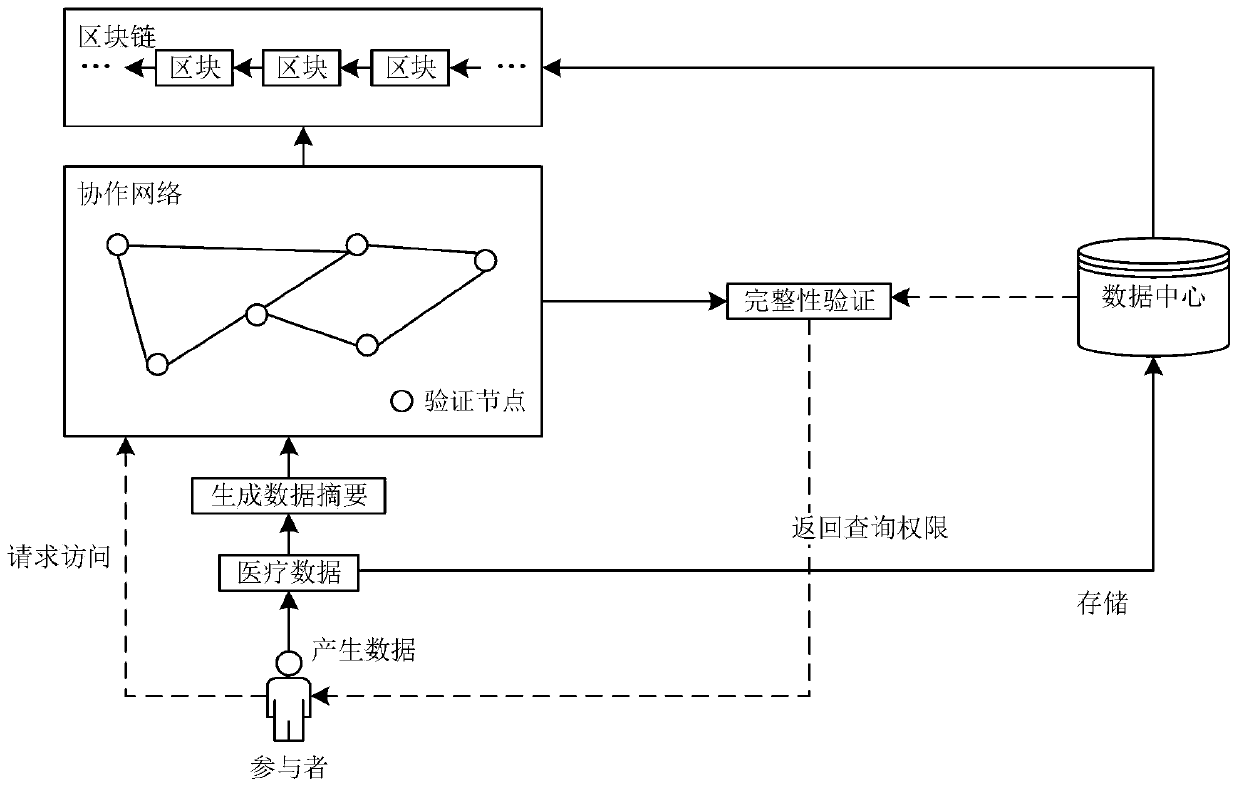
[0035] Step 1: Build as figure 1The blockchain chain-off-chain collaborative interaction framework shown includes the blockchain, the data center under the chain, and the verification network, and the verification network includes a verification node set S VN ={VN 1 ,VN 2 ,...,VN p ,...,VN P}, VN p is the pth verification node, P is the total number of verification nodes;
[0036] Step 2: When the user requests to write data, execute step 3; when the user requests to query data, execute step 4; when the user requests to update data, execute step 5;
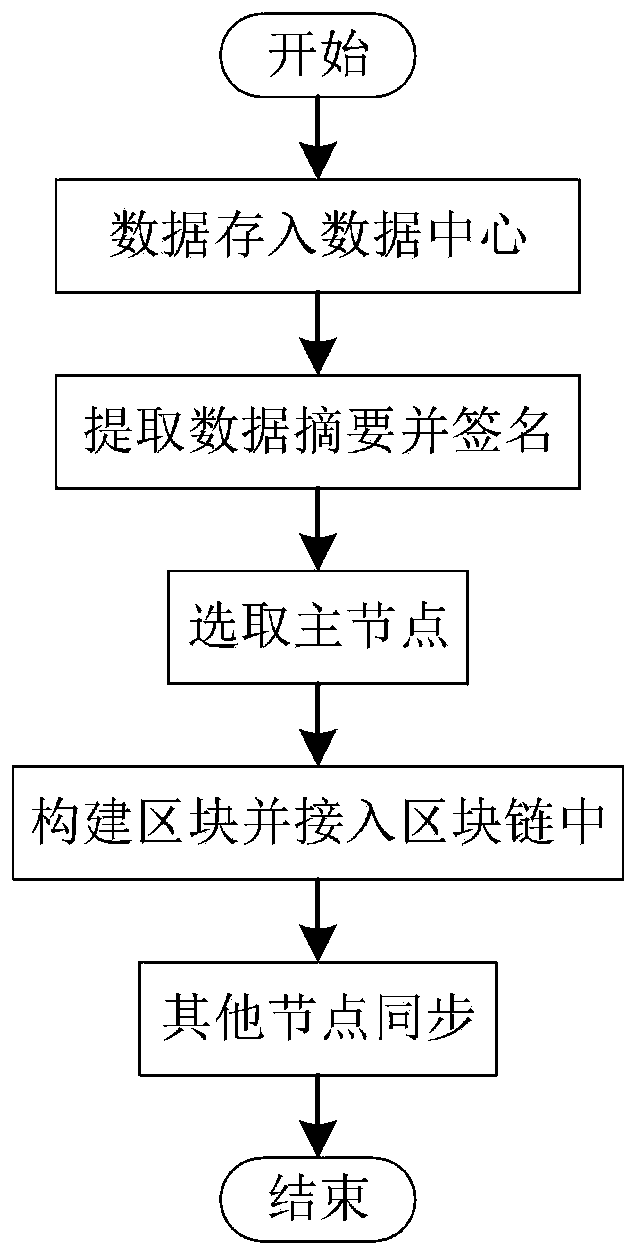
[0037] Step 3: If figure 2 As shown, write on-chain-off-chain data:
[0038] Step 3.1: When user S U ={U 1 ,U 2 ,...,U i ,...,U I} Request to write raw data S data ={data 1 , data 2 ,...,data j ,...,data J}, the original data S data Write to the data center under t...
Embodiment 2
[0056] The difference between the second embodiment and the first embodiment above is that:
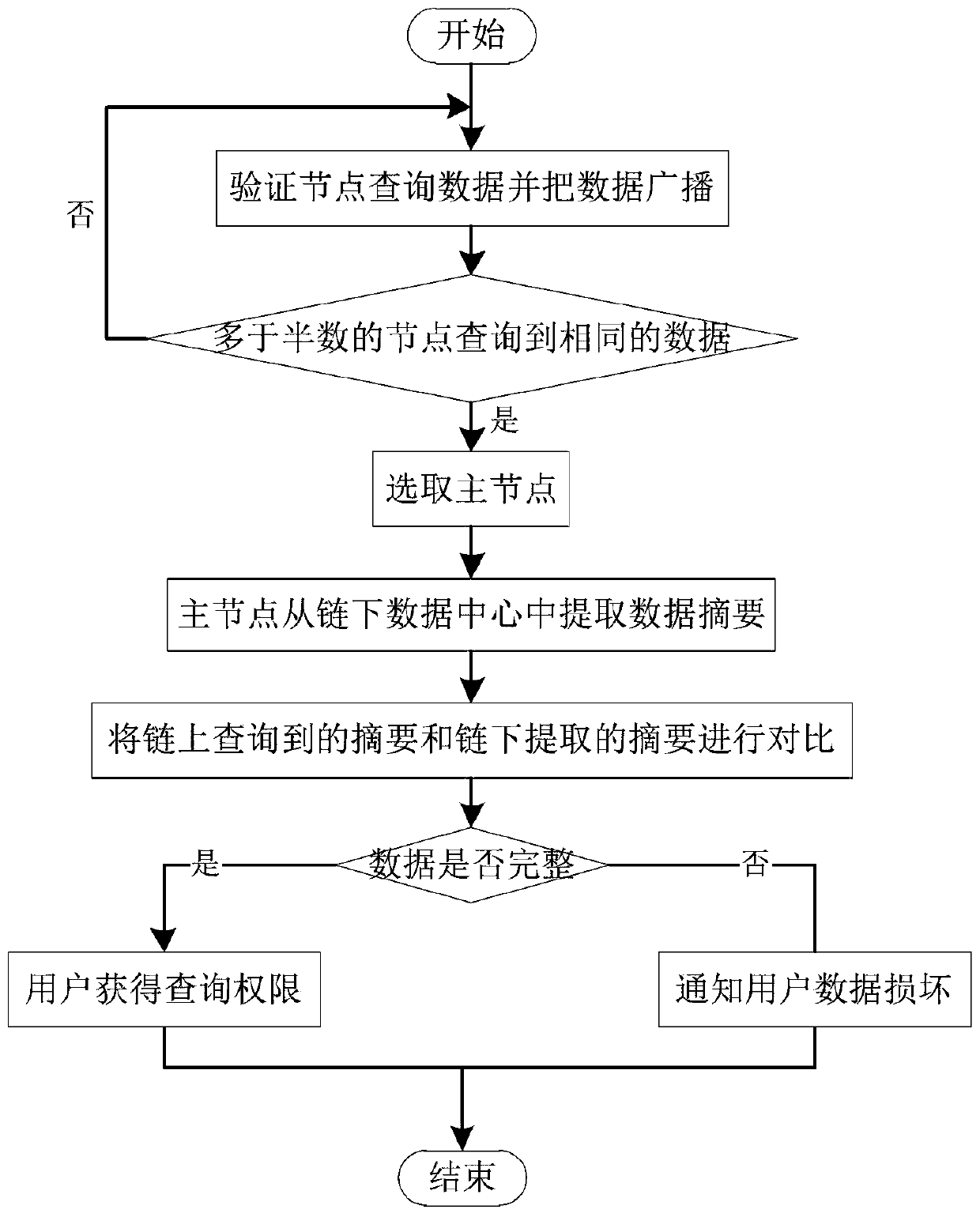
[0057] In the second embodiment, the user U 1 Request query data, will sign sig 1 Sent to the validator set S VN Each validator node in . Verification node set S VN Each verification node in starts from the end of the blockchain to query the data on the blockchain from the blockchain head. Each verification node queries the signature as sig 1 The data on the chain are all broadcast messages, when more than 15 / 2 verification nodes query the same data digest on the chain on When, from query to on-chain data digest on The validator node {...,VN 3 ,VN 4 ,VN 5 ,…} Randomly select a verification node as the master node, VN 3 Selected, the master node VN 3 The third message is broadcast, and other verification nodes stop the data query operation after receiving the third message. Master node VN 3 Query user U from the off-chain data center 1 The raw data, and then extract the d...
Embodiment 3
[0059] The difference between the third embodiment and the first embodiment above is that:
[0060] In the third embodiment, user S U ={U 1 ,U 2 ,...,U i ,...,U 10}Request to modify part of the data as S mdata ={mdata 1 ,mdata 2 ,...,mdata k ,...,mdata 5000}, after modifying the original data on the off-chain data center, notify the verification node set S VN Each validator node in . Verification node set S VN Each verification node in the data S from the data S through the hash function mdata Extract data summary from S mdig ={mdig 1 ,mdig 2 ,...,mdig k ,...,mdig 5000}, and use user U i signature sig i ∈ S sig ={sig 1 ,sig 2 ,...,sig i ,...,sig 10} to user U i Signature of the data digest. From the verification node {VN that first completes the data digest extraction operation 1 ,VN 5 ,VN 7} randomly selects a verification node as the master node, VN 5 Be selected, have the right to record the block, broadcast the fourth message, and other verific...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com