User behavior detection method and system based on remote desktop encryption network traffic mode difference
A network traffic and remote desktop technology, applied in the field of user behavior detection, can solve the problems of lack of universality, coarse granularity, lack of experimental demonstration of behavior recognition effect, etc., and achieve the effect of strong scalability and high accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further elaborated below through specific embodiments and accompanying drawings. It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
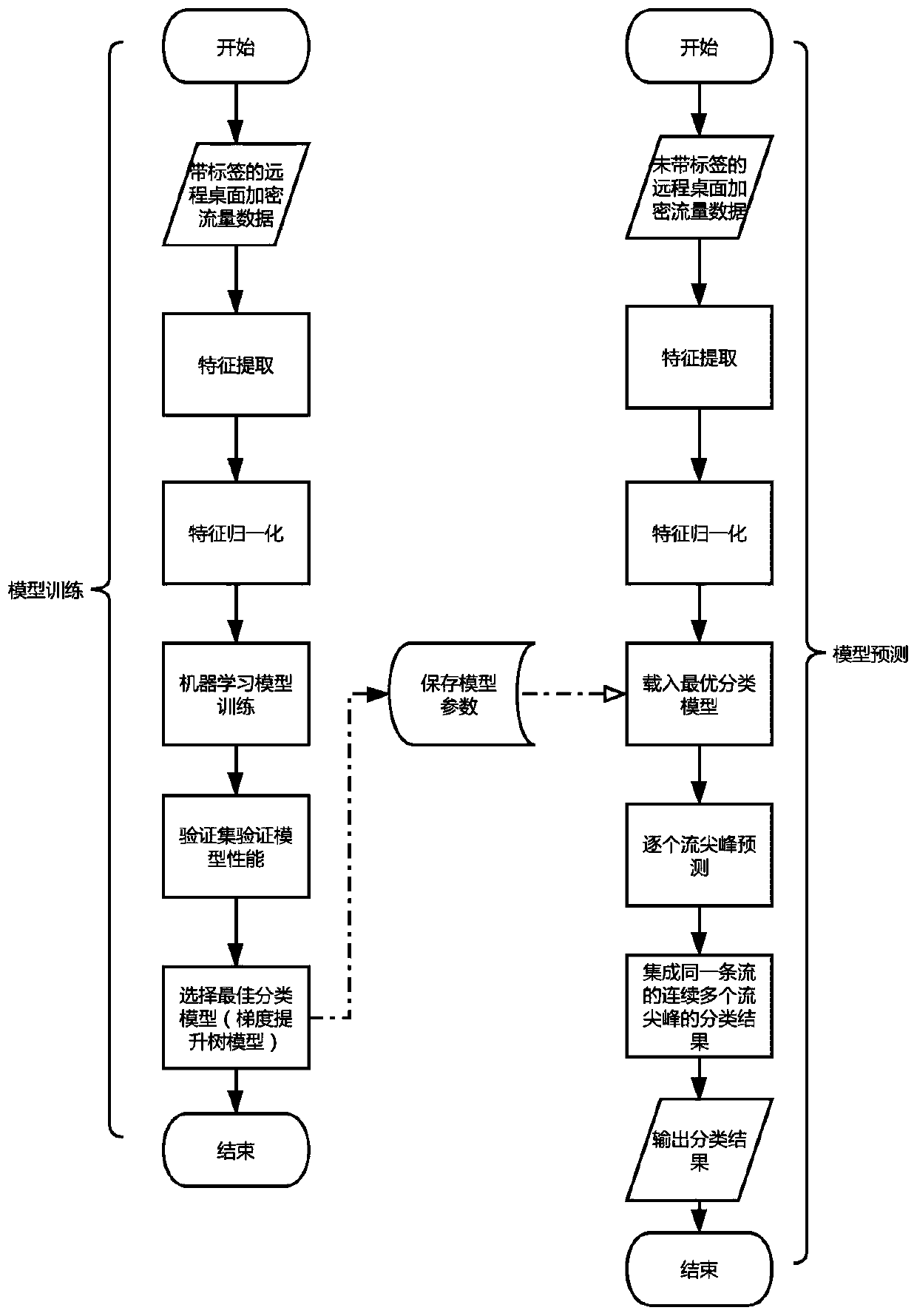
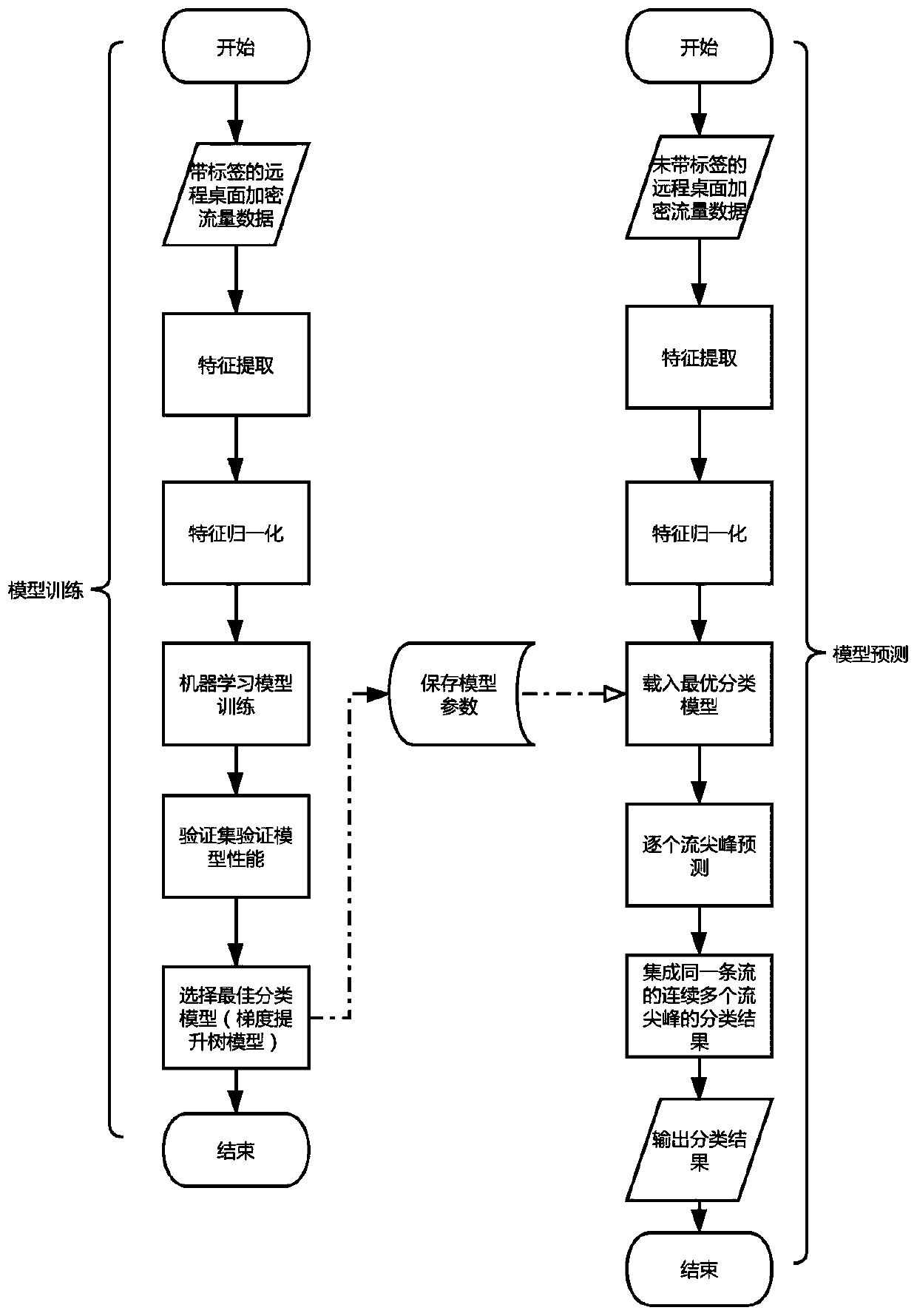
[0034] The present invention discloses a user behavior detection method based on the differences in remote desktop encrypted network traffic patterns. The basic block diagram of the user behavior detection is as follows: figure 1 shown.
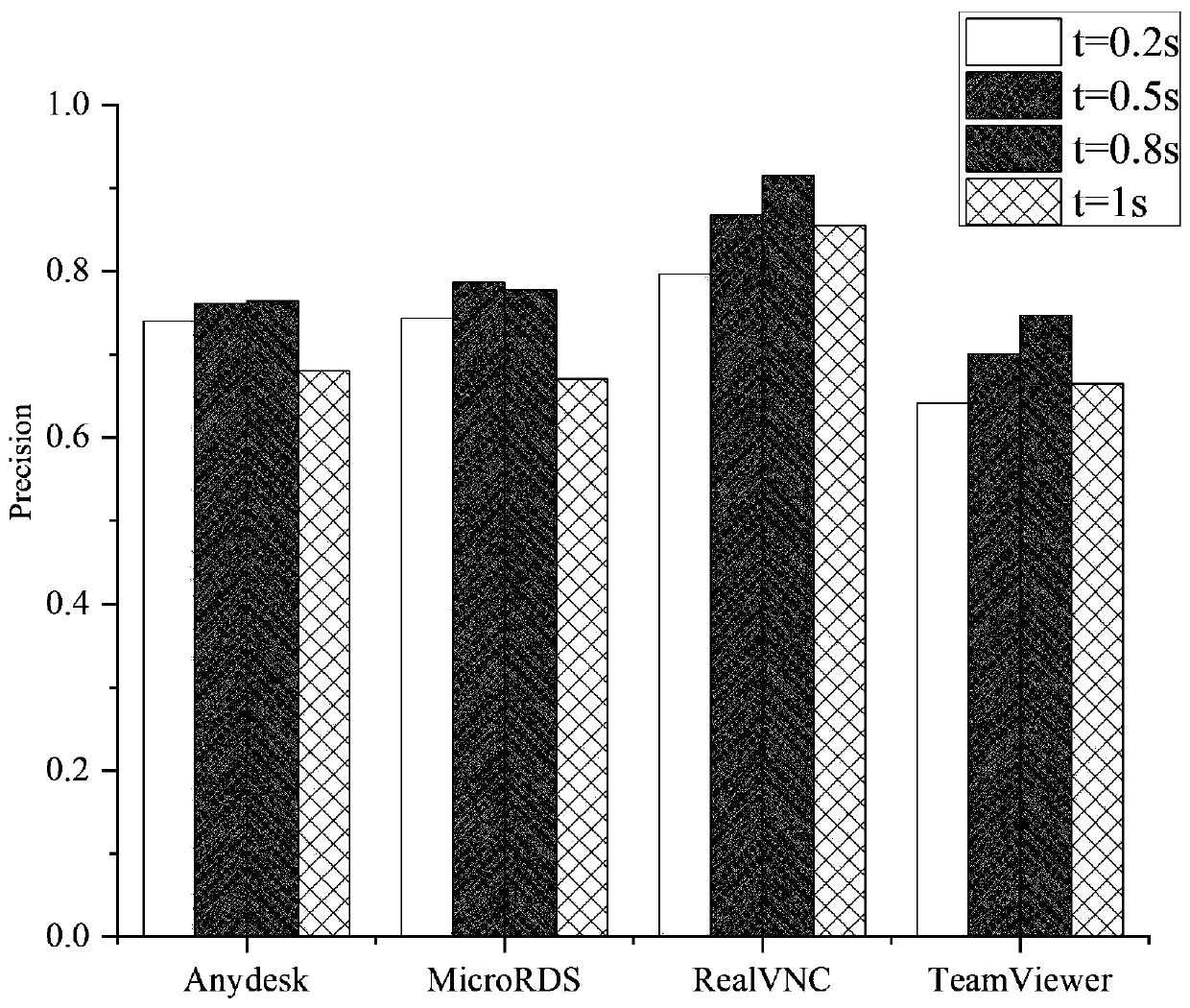
[0035] To collect encrypted remote desktop video traffic of different users under different operating behaviors, we use several local computers with Windows 10 and 7 installed, and several cloud virtual private servers (Virtual Private Server, VPS) with Windows Server 2012 and Windows Server 2016 installed, A router, a variety of common remote desktop software to build an experi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com