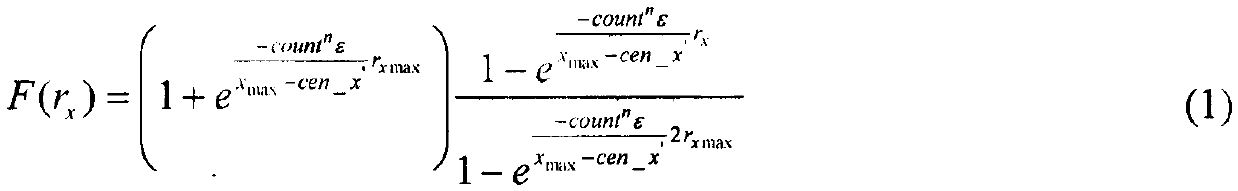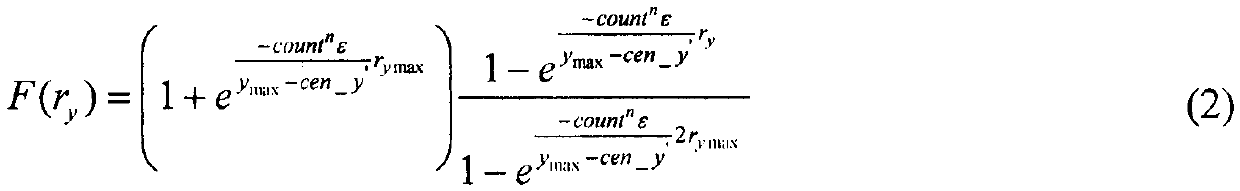Differential privacy trajectory data protection method based on clustering
A technology of trajectory data and differential privacy, which is applied in the intersection of engineering applications and information science, can solve the problems of poor data availability, less research, and immaturity, and achieve good clustering performance, size reduction, and enhanced protection.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] Below in conjunction with accompanying drawing, the present invention will be further described.
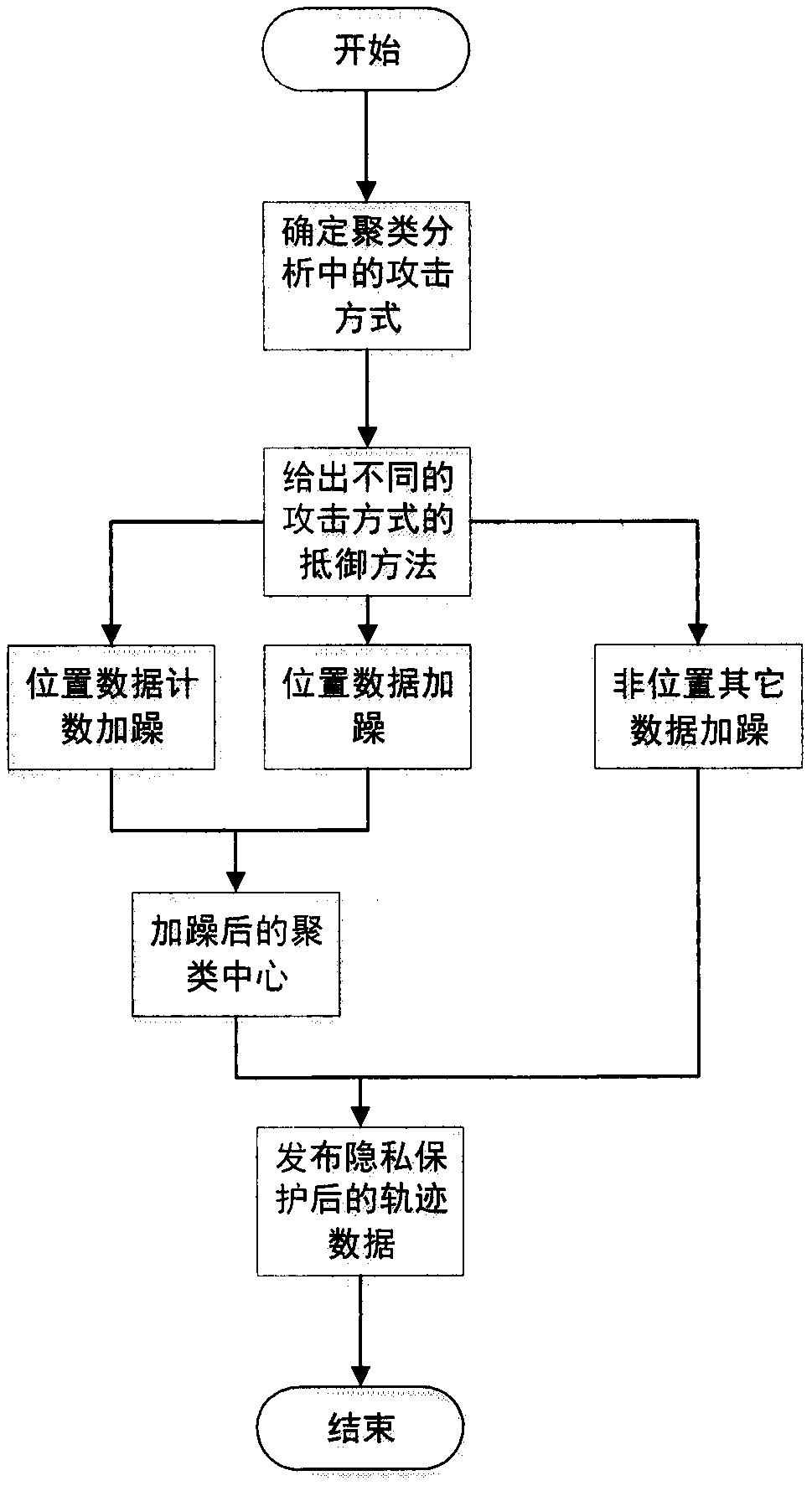
[0023] The invention proposes a clustering-based differential privacy trajectory data protection method. This method applies differential privacy technology to trajectory clustering, and resists attacks by adding Laplacian noise to trajectory positions, cluster centers and position counts in each cluster. Since it is impossible to determine whether there is a correlation between different dimensions of trajectory data, we express the final noise result through the linear combination of the results of adding noise in each dimension and the result of adding noise in two-dimensional space, and limit the size of the noise. At the same time, considering that the trajectory may contain other information that may lead to the leakage of user privacy, in order to protect the privacy of user trajectory, this paper also adds noise to these data. The specific implementation steps are...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com