A puf-based lightweight RFID tag ownership transfer communication authentication method
An RFID tag and authentication method technology, applied in the field of lightweight RFID tag ownership transfer communication authentication, can solve the problems of unpredictable response, security and privacy threats, randomness, etc., to reduce hardware overhead, reduce computational overhead, and ensure privacy. sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
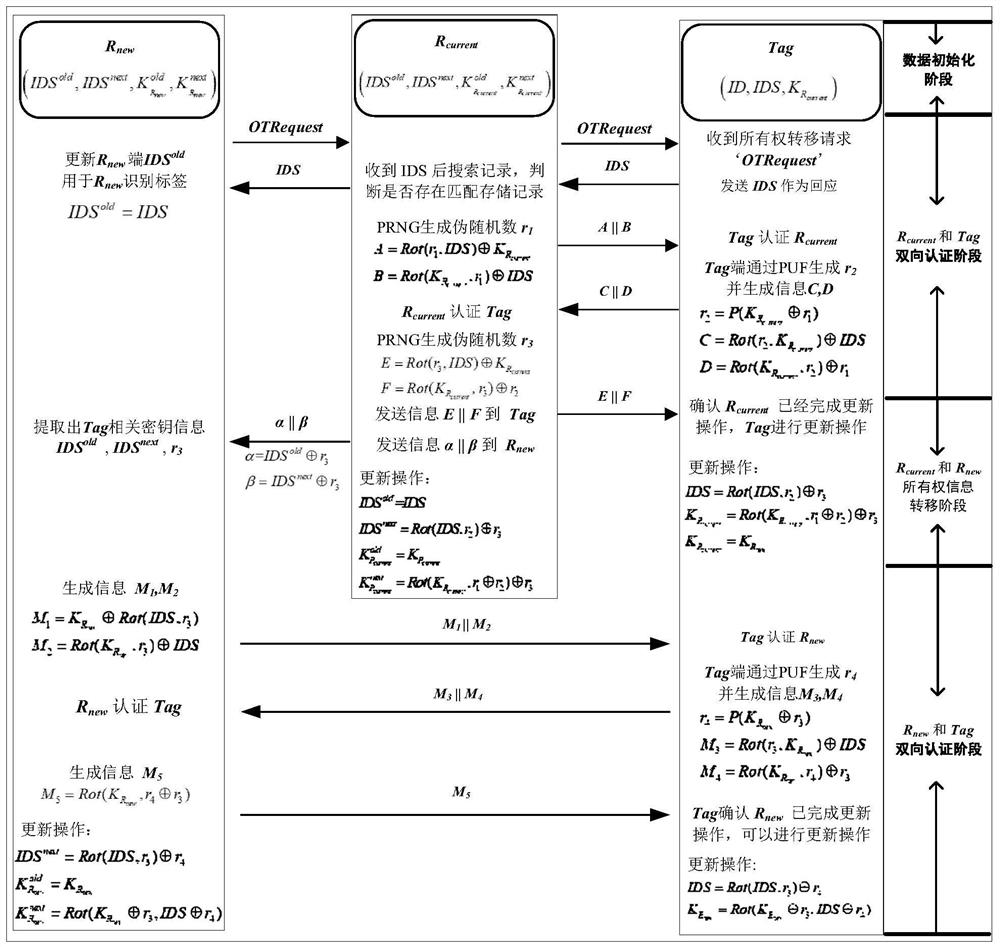
[0070] In order to describe the solution and advantages of the method of the present invention more clearly, the method of the present invention will be further described in detail below in conjunction with the above-mentioned drawings.
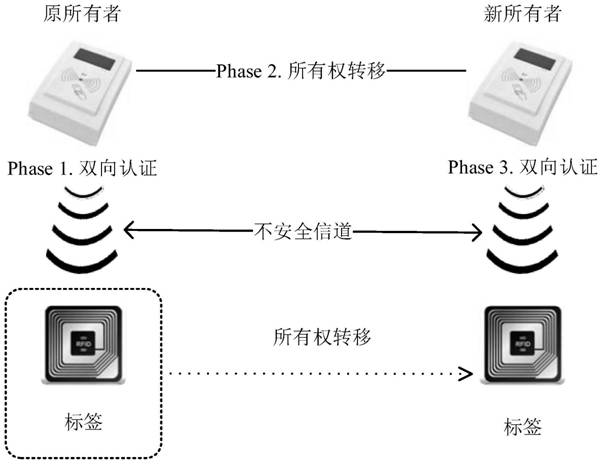
[0071] like figure 1 It is a communication relationship diagram between the tag, the original owner of the tag, and the new owner of the tag in the PUF-based lightweight RFID tag ownership transfer communication authentication method of the present invention;
[0072] figure 1 It shows that an RFID system mainly includes three components: RFID tag (Tag), RFID reader (Reader) and back-end database (Database);
[0073] figure 1 The main communication authentication relationship of the PUF-based lightweight RFID tag ownership transfer communication authentication method of the present invention is shown in the present invention, that is, the two-way authentication between the original tag owner and the tag, the original tag owner and the new t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com