Intelligent contract security vulnerability detection method based on machine learning
A technology for smart contracts and vulnerability detection, applied in computer security devices, instruments, data processing applications, etc., and can solve problems such as security vulnerabilities and smart contract community damage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
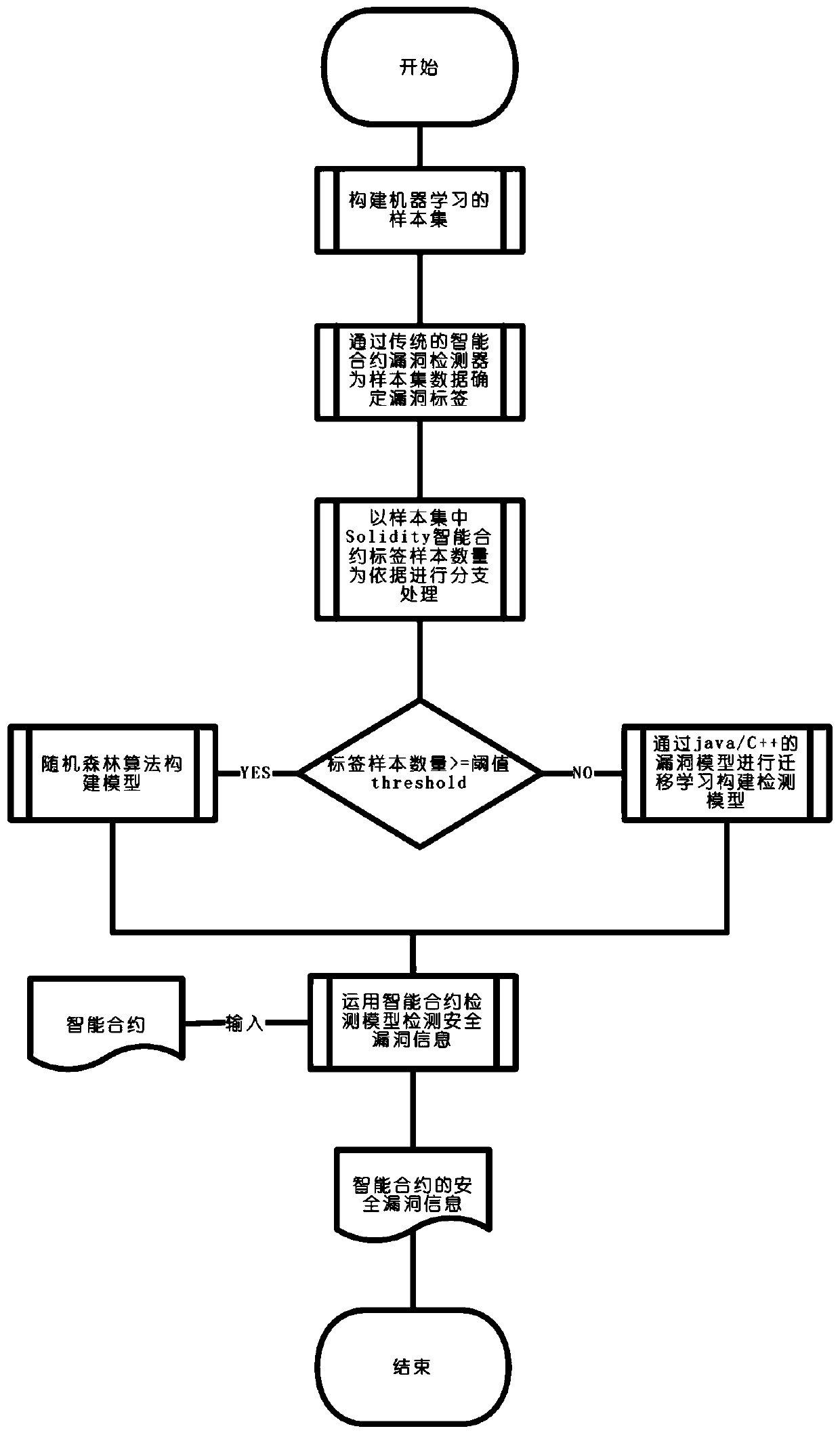
[0039] This embodiment discloses a machine learning-based smart contract security vulnerability detection method, such as figure 1 As shown, the detection method includes the following steps:
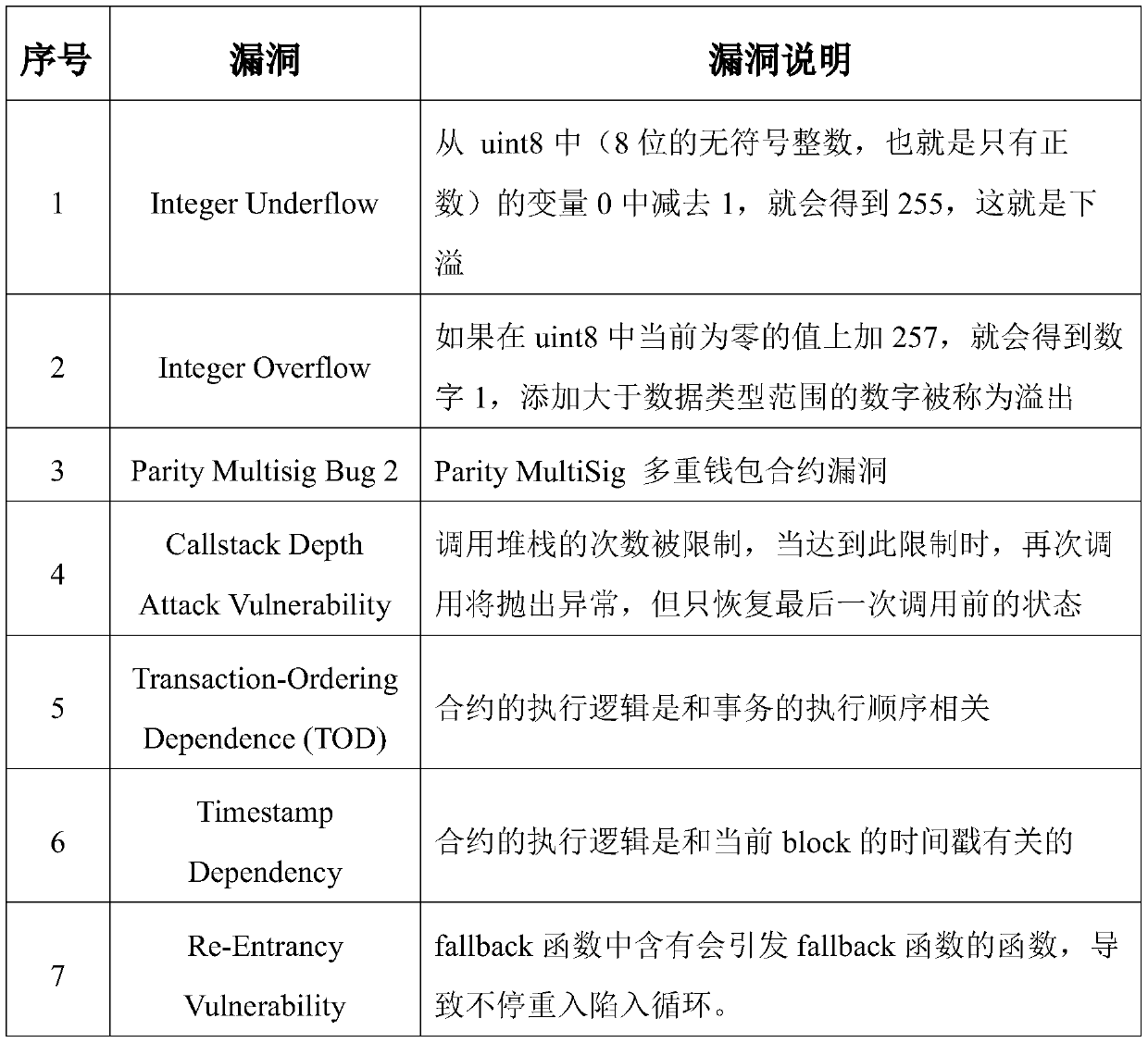
[0040]S1. Collect a large amount of Solidity smart contract codes and Java / C++ codes on the Internet to form the basic data set for machine learning. Select contracts whose Solidity compilation version is higher than the specified version number and whose code content repetition rate is lower than the repetition threshold in the basic data set as the machine learning sample set;
[0041] Specifically in this embodiment, the process of step S1 is as follows:
[0042] S11. Use crawler scripts to collect Solidity smart contract codes from the Ethereum smart contract platform, and collect Java / C++ codes from the open source community;
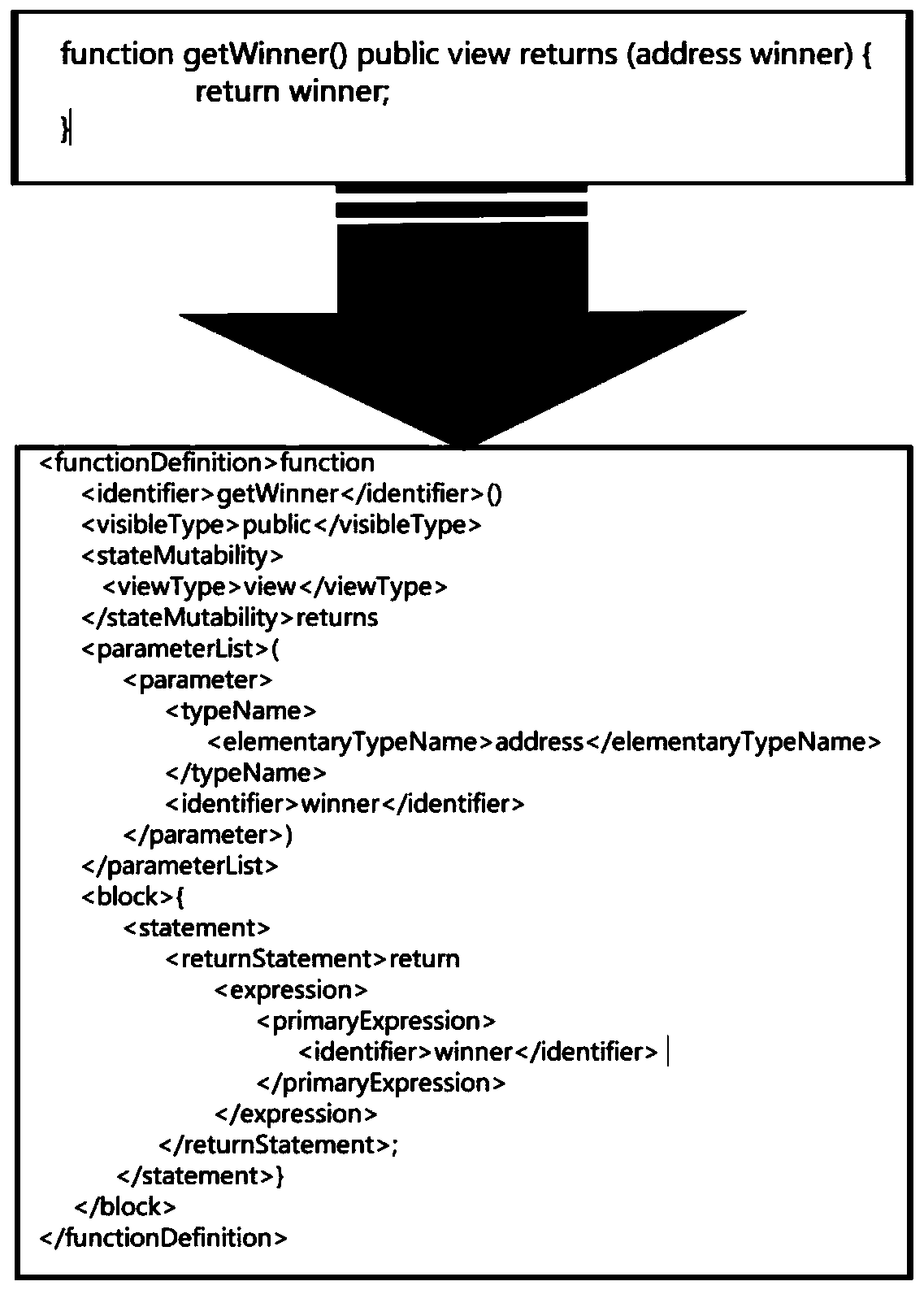
[0043] S12. Convert the Solidity smart contract code into structured XML text, directly obtain the compiled version of Solidity, and then compare the conv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com