System, method and device for testing heterogeneity of mimic system based on network packet capture
A technology of imitation system and test system, applied in transmission system, digital transmission system, data exchange network, etc., can solve the problem of limited types of test methods, and achieve the effect of high efficiency, convenience and comprehensive stability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
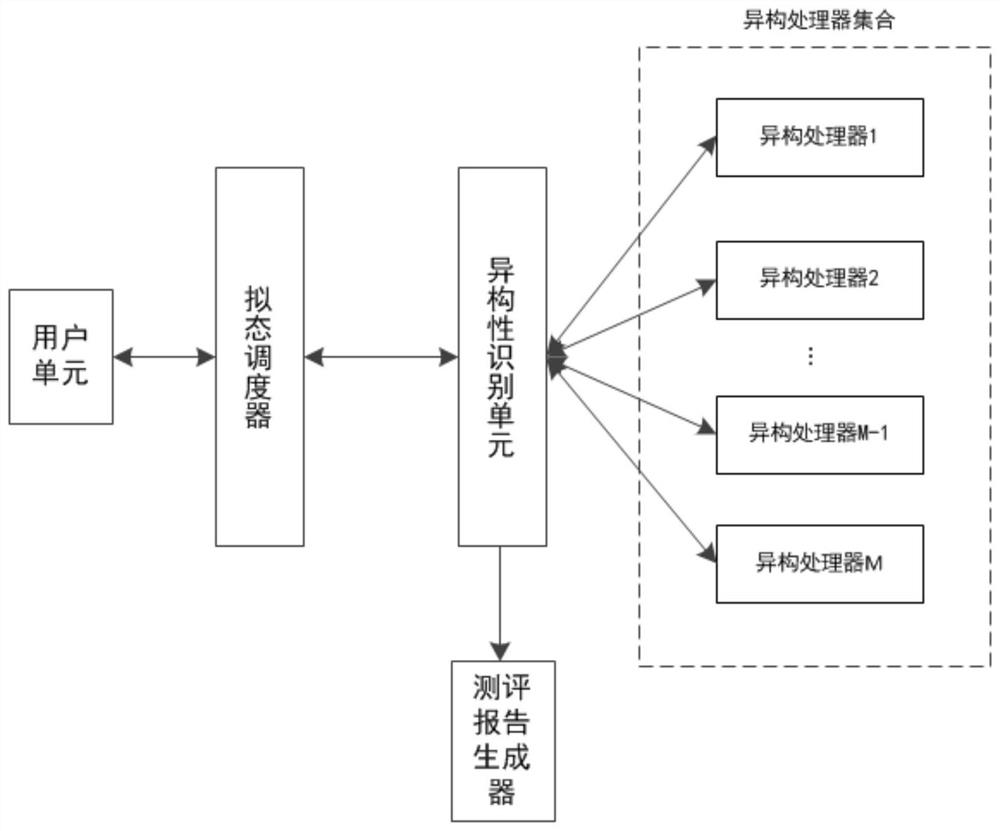
[0114] see figure 1, a device for testing the heterogeneity of a mimic system based on network packet capture, comprising a user unit, a mimic scheduler, a heterogeneous processor set, a heterogeneity identification unit, and an evaluation report generator;
[0115] The mimetic scheduler distributes the external data from the user unit to multiple heterogeneous processors through the reverse proxy server of the data transfer module, so that M heterogeneous processors perform operations on the data respectively; according to multiple heterogeneous processors The output calculation results are subjected to mimicry judgment, and the isomer numbering sequence that is consistent with the calculation results is output to the heterogeneity recognition unit, and the inconsistent heterogeneity processor is cleaned;
[0116] A set of M heterogeneous processors, including M heterogeneous processors that are dynamically executed online. The M heterogeneous processors are mutually heteroge...
Embodiment 2
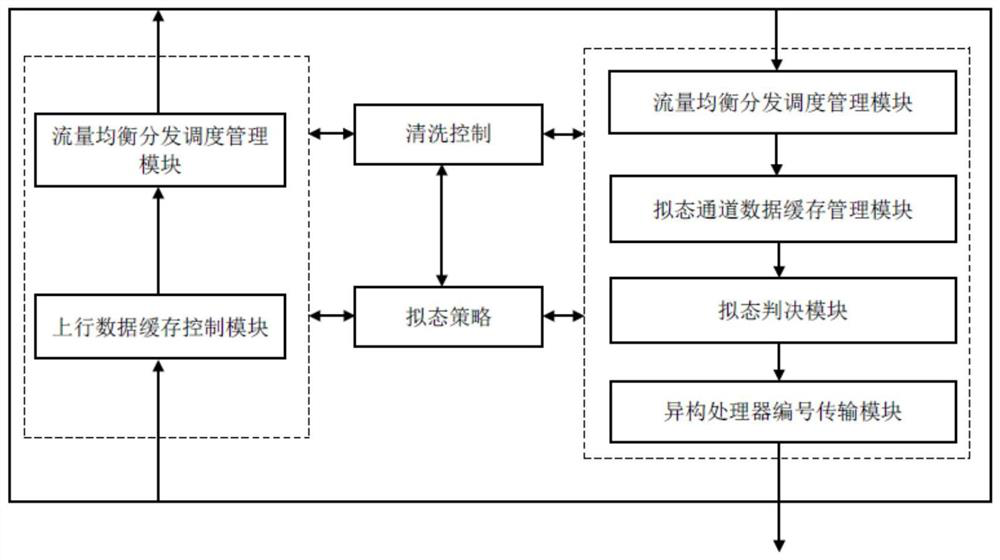
[0120] see figure 2 , the specific workflow of the mimic scheduler is as follows:
[0121] Step 201, distributing the external data from the user unit to multiple heterogeneous processors through the reverse proxy server of the data transfer module;
[0122] Step 202: Receive the calculation results returned by the M heterogeneous processors according to the preset transmission rate, and perform a mimicry judgment on the calculation results returned by the M heterogeneous processors according to the current working mode;
[0123] Step 203 , output the isomer numbering sequences whose independent calculation results of the heterogeneous processors are consistent to the heterogeneity identification unit at a certain frequency, and at the same time perform cleaning operation on the inconsistent heterogeneous processors, and store the calculation results.
[0124] see image 3 , the specific workflow of the heterogeneity recognition unit is as follows:
[0125] Step 301: The d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com