Bidirectional user authentication and secret information quantum communication transmission method
A secret information and quantum communication technology, applied in the field of two-way user authentication and secret information quantum communication transmission, can solve the problems of cumbersome process, potential security risks, complicated operation, etc., to simplify the information transmission process, reduce deployment costs, and improve security performance Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
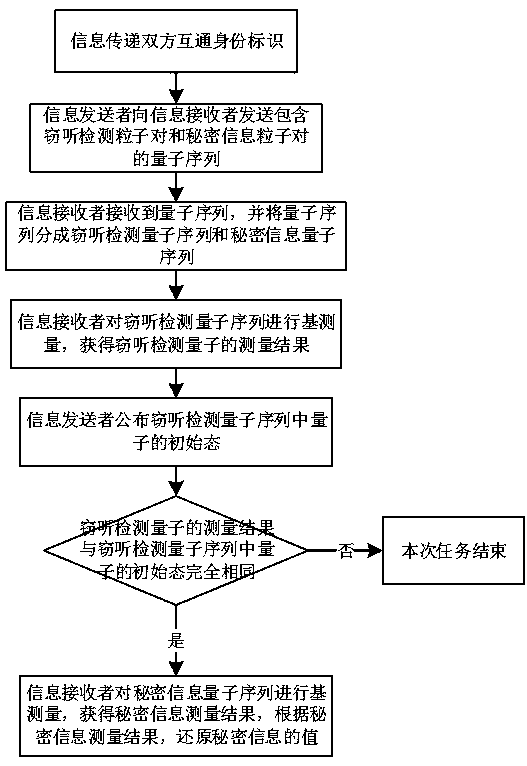
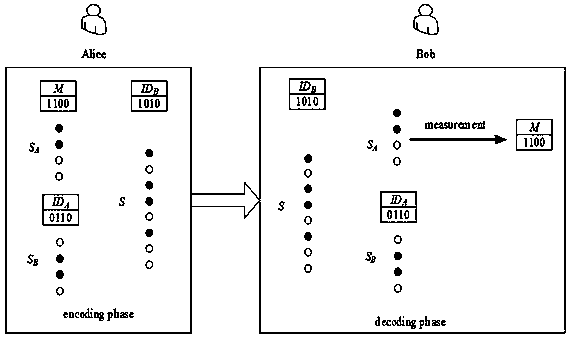
[0039] Please refer to figure 1 This embodiment provides a two-way user authentication and secret information quantum communication transfer method. Assuming that Alice is the message sender and Bob is the message receiver, Alice will transmit the secret information M=1100 to Bob, and Alice’s identity ID A = 0110, Bob’s identification ID B = 1010, identification ID B , Identity ID A And the secret information M is a 4-digit machine code. For the security of secret information transmission, the identity must be completely kept secret. Before the transmission, Alice and Bob each save their own identities. In this embodiment, the Z base used for base measurement is |0> And|1> , There are four Bell bases used for base measurement, namely , , with ,among them, , , , .
[0040] The process of Alice passing the secret message M=1100 to Bob is as follows:
[0041] S1. In order to ensure that Alice and Bob can confirm each other’s identities during the transmission of secret informat...
Embodiment 2
[0084] Compared with Embodiment 1, after the value of the secret information is restored in step S7, Alice and Bob reconfirm whether the secret information is correct by publishing part of the secret information, and then further improve the security of the method of the present invention.
[0085] In addition to the above-mentioned implementation exceptions, comparison information can also be added to the secret information to ensure that the secret information sent is exactly the same as the secret information received.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com