Sensor network authentication key establishment method based on light certificate and implementation device thereof
A sensor network and authentication key technology, applied in the field of authentication key establishment, can solve the problem of negotiating packet loss without considering the solution, reducing security, not considering and other problems, achieving high security, low reliability, and improving reliability Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The technical solutions of the present invention will be further specifically described below through the embodiments and in conjunction with the accompanying drawings.
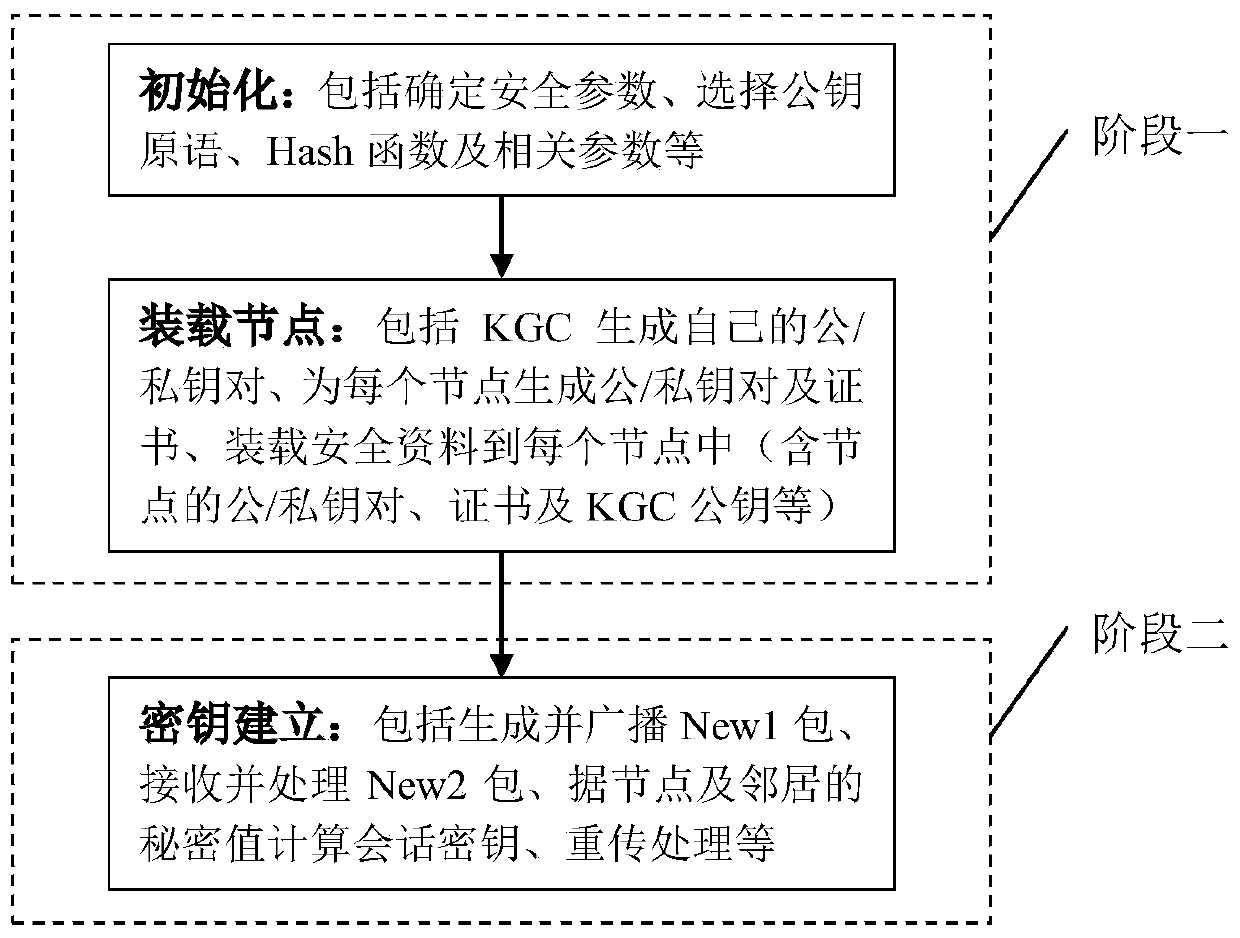
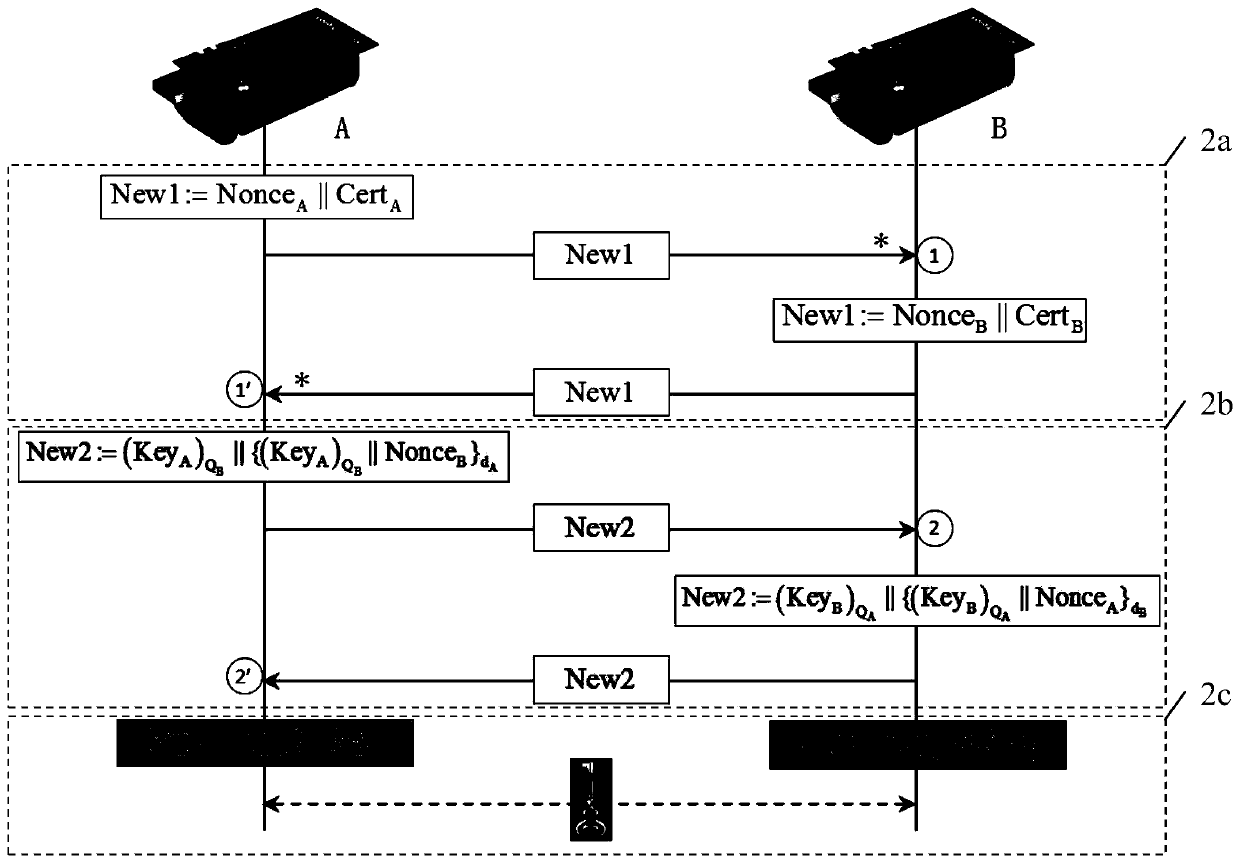
[0037] The authentication key establishment method provided by the present invention includes the following two stages:
[0038] Phase 1: Key pre-distribution
[0039] This stage is divided into two steps:
[0040] Step 1, initialization.
[0041] Assuming that the security requirement of the application scenario of this method is 80-bit level, if we choose the public key primitive used as ECC, then the security parameter λ=160 can be selected.
[0042] Take the curve as E:y 2 =x 3 +ax+b(a, b is a constant, 4a 3 +27b 2≠0), select a large prime number p of λ bits, based on E / F p Construct a cyclic Abelian group G with order q (q is also a sufficiently large λ-bit prime number), from which a generator P can be determined.
[0043] Choose a suitable hash function: Because the hash function in th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com