Automatic reinforcing method for security configuration of information system
A technology for security configuration and information system, applied in the field of automatic reinforcement of information system security configuration, it can solve the problems of heavy workload, manpower, and high requirements for inspectors' skills and experience, and achieve the goal of improving efficiency, reducing rectification costs, and improving operation level. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
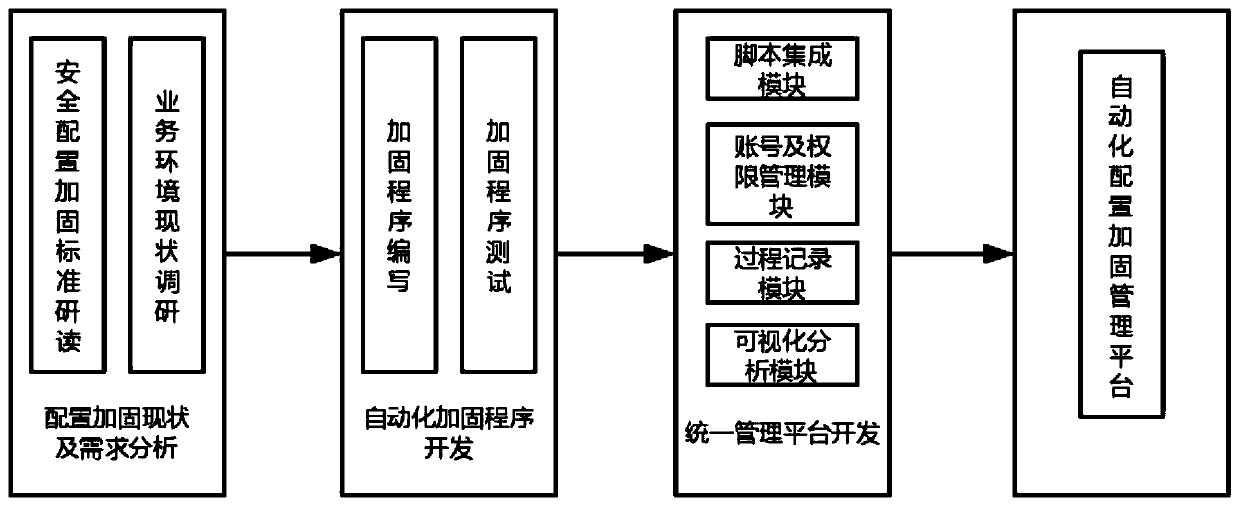
[0024] An information system security configuration automatic reinforcement method, including developing an automatic reinforcement script program for security configuration items of various operating systems, databases, and middleware, and then integrating the complete reinforcement script and rollback script into a unified WEB management system , complete the hardening by connecting the target system through the system, and manage and record the whole process of hardening;
[0025] It specifically includes the following steps:
[0026] S1. Develop automated reinforcement scripts for various components:
[0027] S1-1. Fully study the information system configuration inspection requirements based on hierarchical protection, compare the default configurations of various systems, and confirm the main non-compliant configuration inspection items;
[0028] S1-2. Investigate the current business environment, eliminate configuration items that affect business or cannot be reinforce...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com