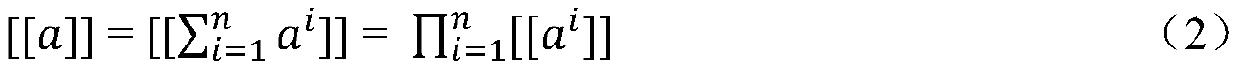Safety SVM training method based on block chain
A training method, blockchain technology, applied in the field of artificial intelligence machine learning, to achieve the effect of ensuring high efficiency and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
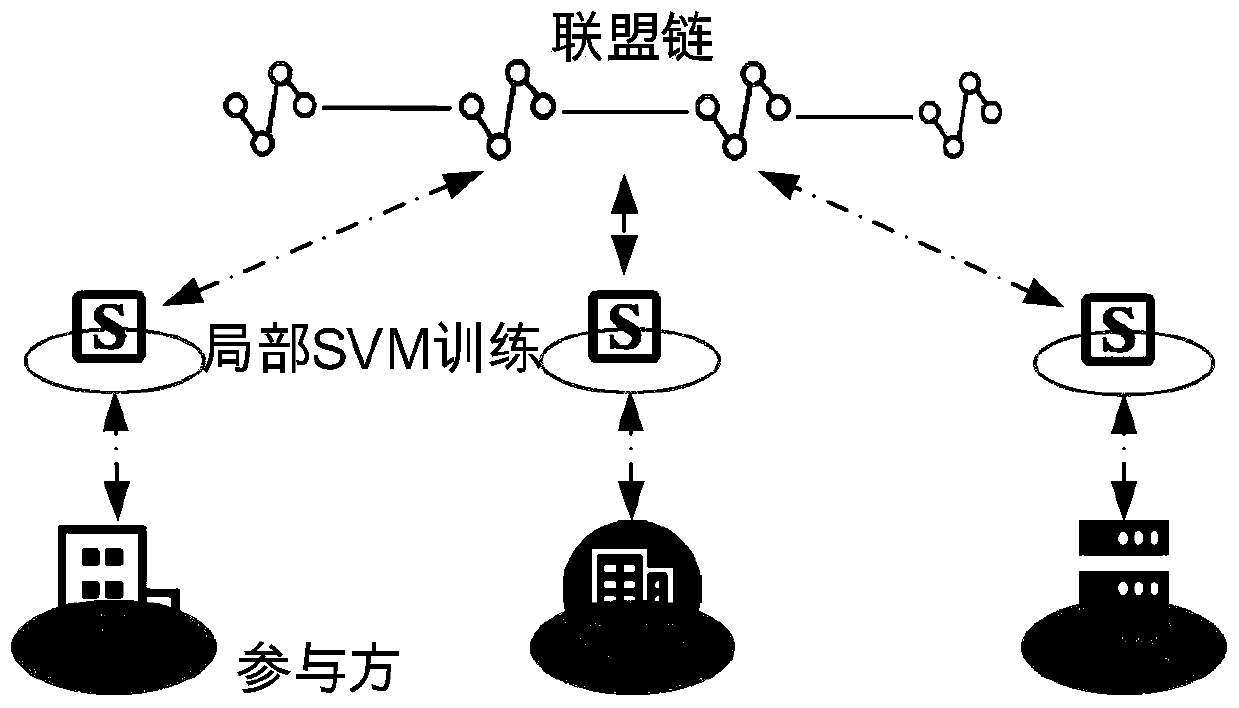
[0056] A blockchain-based secure SVM training method, such as figure 1 shown. figure 1 A safe SVM co-training scenario is described. There are 3 data providers participating in the training, namely |N|=3. Data providers are responsible for collecting, processing and building their own data sets. There are differences in the attributes contained in the datasets between different data providers, so after the three data providers share the data, a dataset with comprehensive attributes can be formed. The three data providers are also the trainers of the model. Under the condition that the original training data and intermediate calculation results are not leaked, they collaborate to complete the training of the SVM model based on the data sets with different attributes. During the training process, the blockchain-based data platform connects various data providers to provide a decentralized collaborative training environment.
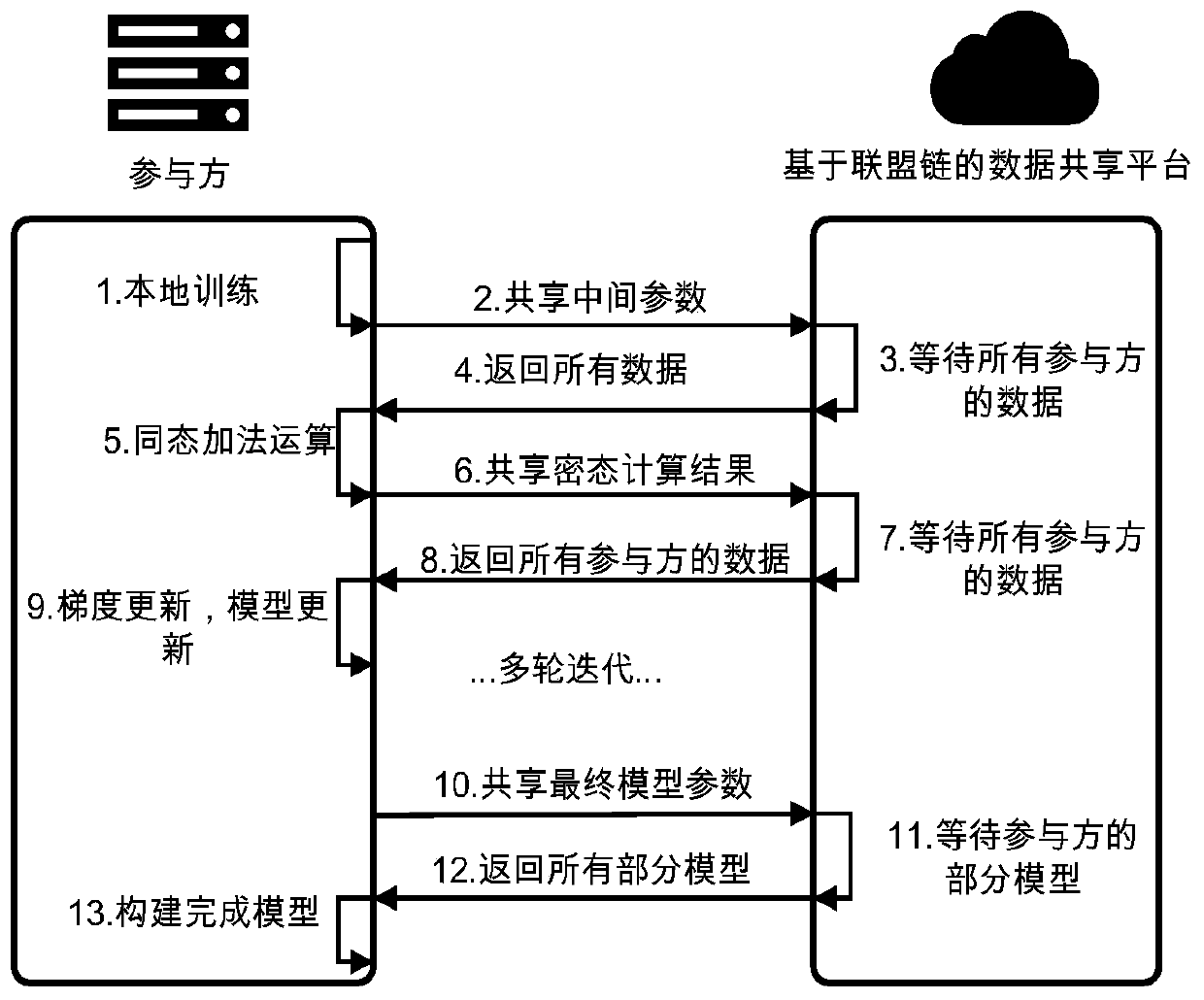
[0057] During the model training process, the dat...
Embodiment 2
[0069] This embodiment is to compare the results of the scene after the number of data providers of the present invention is expanded from 3, to verify the change of the accuracy rate of the method adopted in the invention when the number of data providers is different. At the same time, increase the model training under the dataset Australian Credit Approval Data (ACAD). Assume that the numbers of data providers are 3, 4, and 5 respectively. That is, the data set is vertically cut into 3, 4, and 5 parts according to the attributes. Follow steps 1 to 4 to train the model, and count the classification accuracy of the model. Table 1 shows the statistical results of running time when the number of data providers is 3, and the accuracy of the model is shown in Table 2; when the number of data providers expands, the accuracy of the model is shown in Table 3.
[0070] Table 1 Running time statistics table
[0071]
[0072]
[0073] Table 2 Accuracy comparison result table ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com