Real-time network flow anomaly detection method based on big data
A real-time network and traffic anomaly technology, applied in the direction of data exchange network, digital transmission system, electrical components, etc., can solve the problems of reducing the success rate of network attacks, loss, large-time computing power, etc., to achieve accurate detection of network traffic anomalies, reduce The effect of false positive rate and improvement of computing power
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] Specific embodiments of the present invention will be further described below in conjunction with the accompanying drawings.
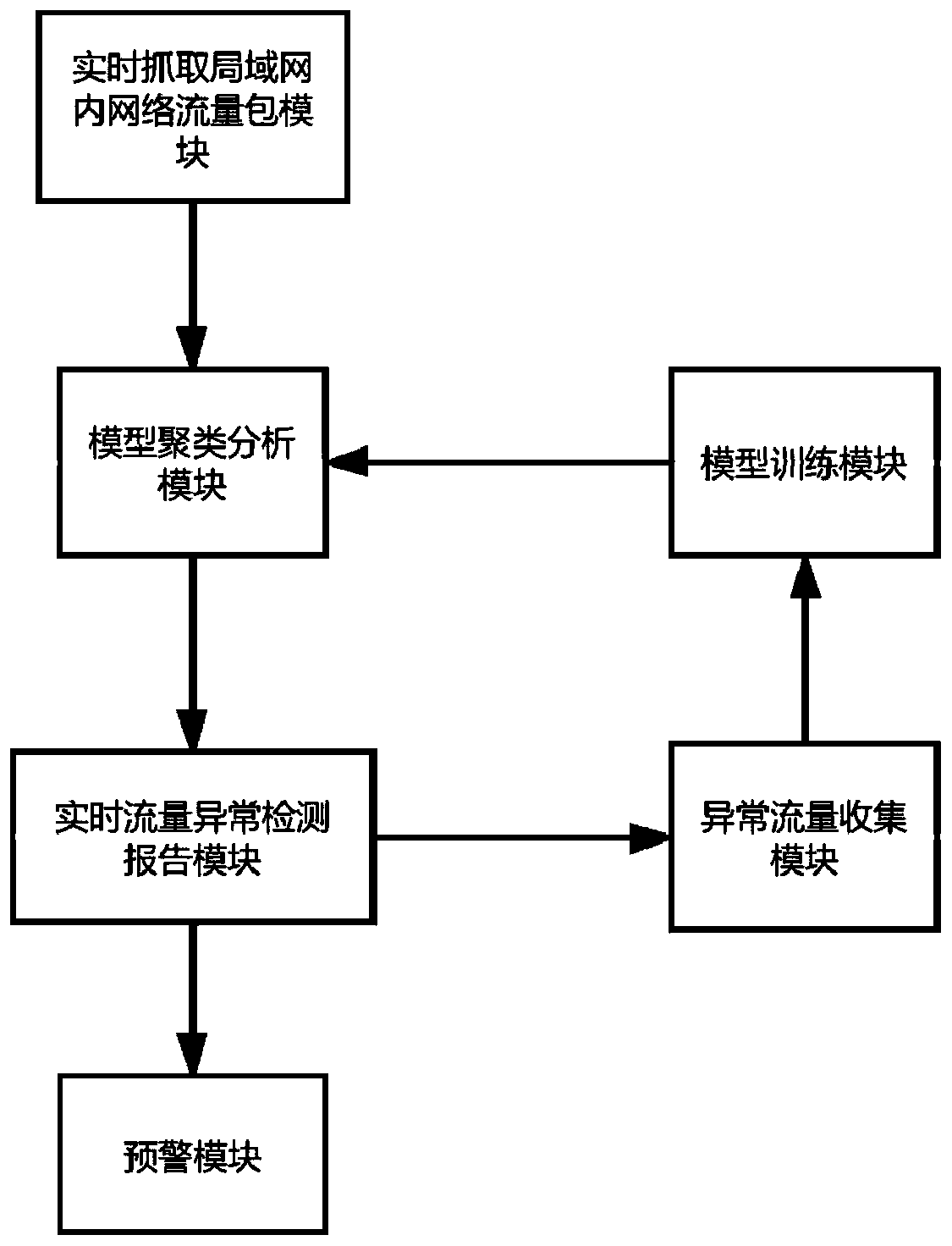
[0035] The present invention provides a real-time network traffic anomaly detection method based on big data, which can process and analyze network traffic through big data analysis technology, predict the time and attack type of network attacks, and then take effective preventive measures to prevent them.
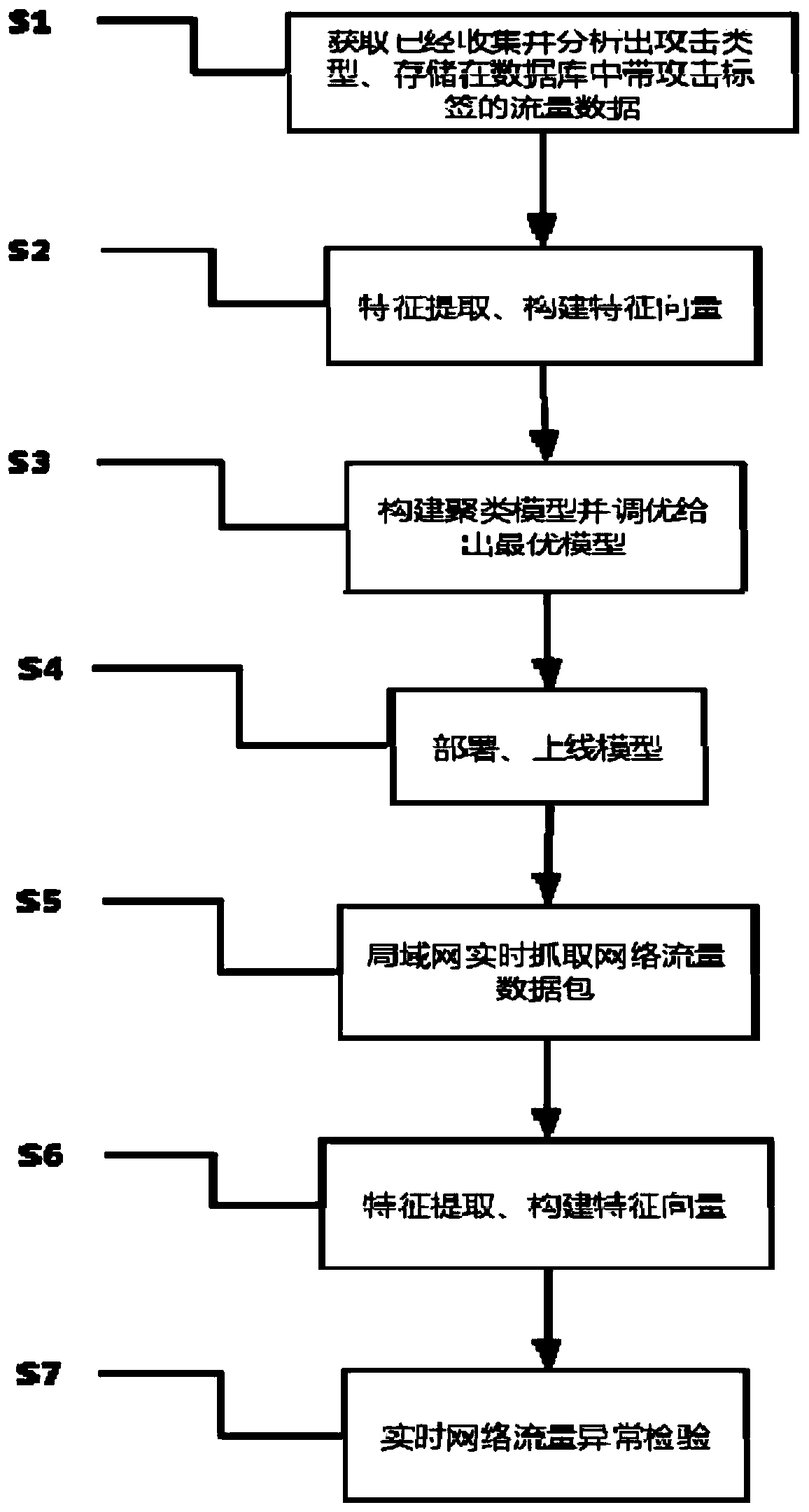
[0036] Such as figure 1 As shown, the embodiment of the present invention provides, including the following steps:
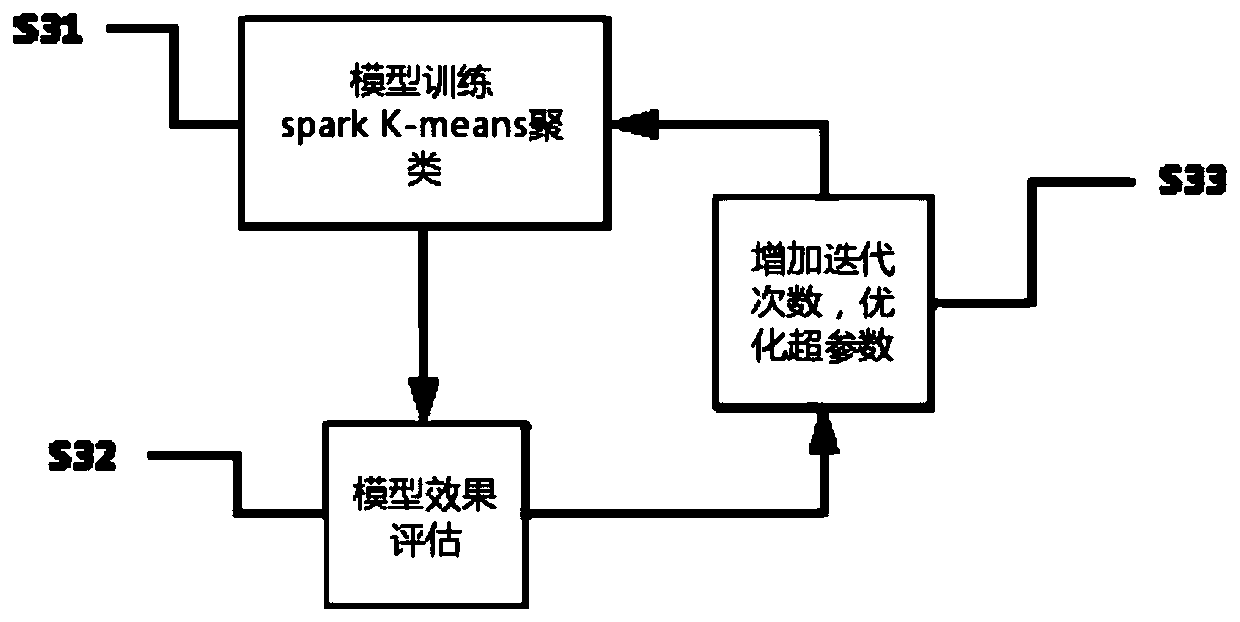
[0037] (1) Step S1. Read the collected and analyzed attack type traffic data stored in the database with attack tags, and remove the tag attack type from the data. Removing the label attack category here does not mean that such labels will not be used, but because the unsupervised clustering algorithm is used, so the label category is not used, but it will be used in the model evaluation in step S3, which can be passed throug...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com