Unified identity authentication interface and method based on Token
An identity authentication and interface technology, applied in the Internet field, can solve problems such as heavy load on the server side and inability to meet the requirements of multiple platforms
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
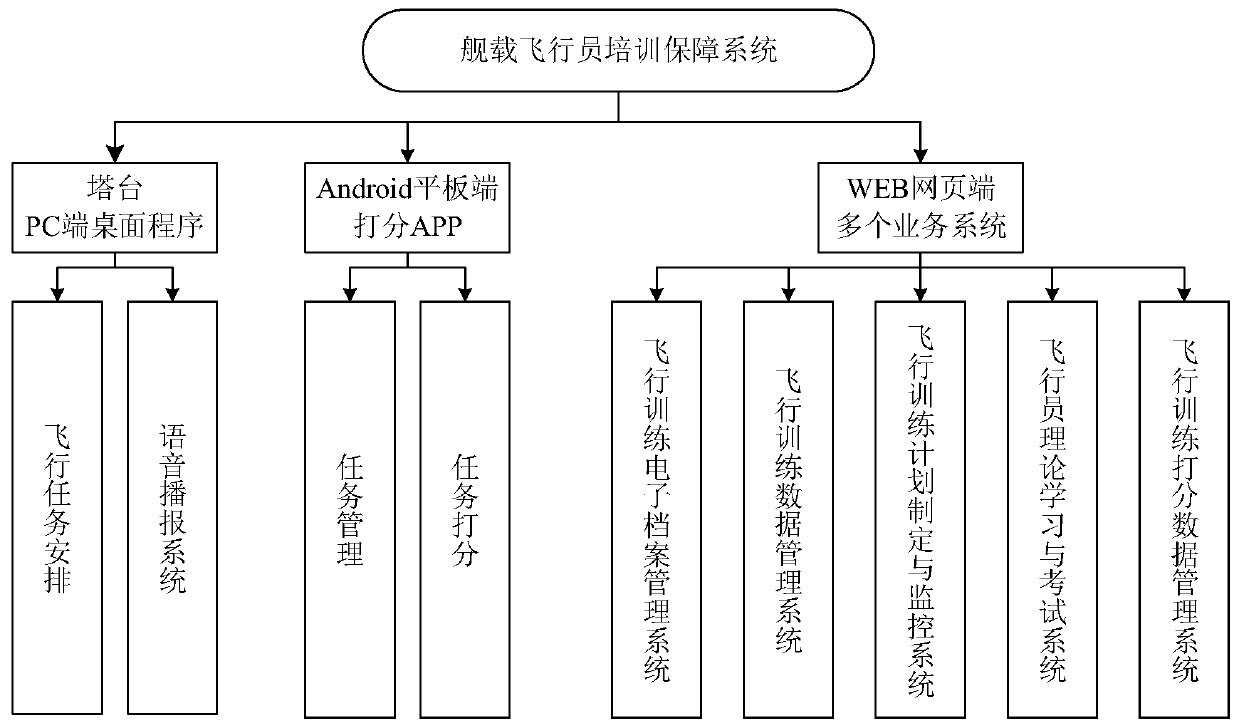
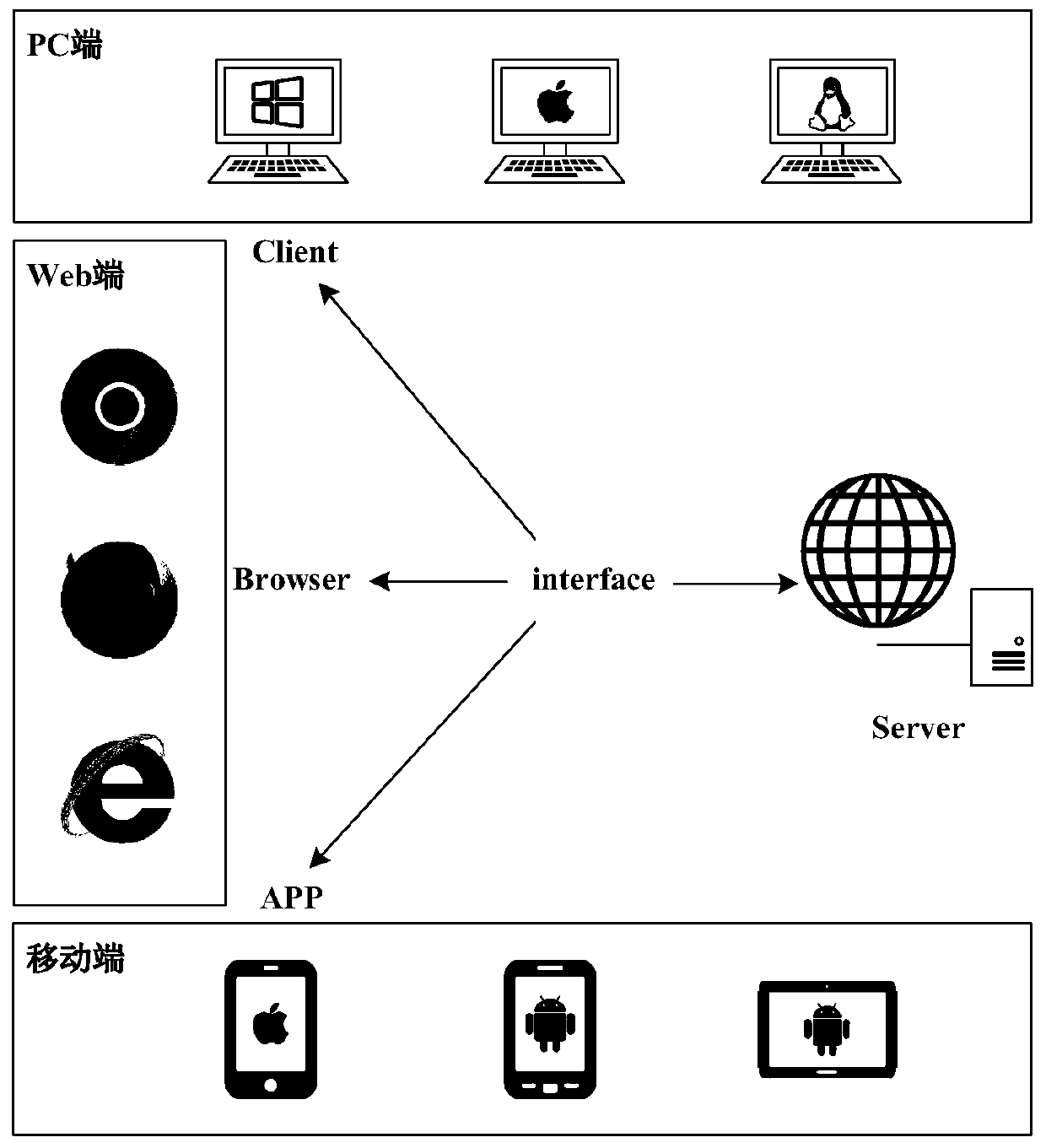
[0025] This embodiment takes the multi-platform landing of the carrier-based aircraft pilot training support system as an application scenario, but is not limited thereto. The system structure diagram of the security system is roughly as follows figure 1 As shown, it contains multiple cross-platform systems, covering multiple web application systems and Android tablet APP. Because multiple system databases are not related to each other but the user group is fixed, unified identity authentication is required. The so-called identity authentication is the process of judging whether a user is a legitimate user.
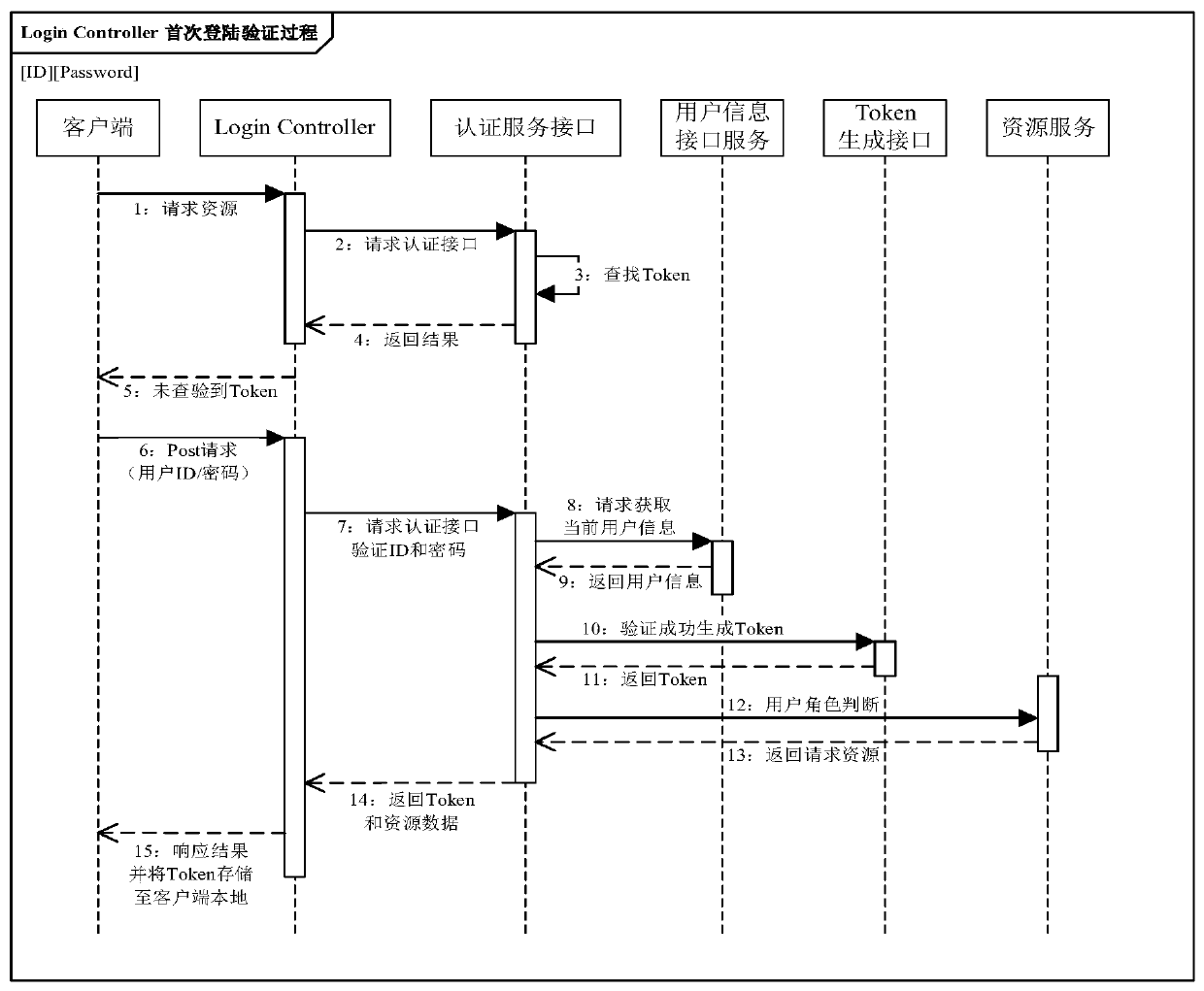
[0026] Token-based identity authentication, obviously how to design Token (token) is the most important link in the entire identity authentication system, and the specific token composition includes multiple parts:
[0027] The first part is the pilot number (user name), login client type, and pilot type (user category). These user basic information are stored in JSON ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com