Protocol agent processing method and system based on mimicry defense
A processing method and protocol technology, applied in transmission systems, electrical components, etc., can solve the problems of complex protocol packet duplication in protocol packet processing, and achieve the effect of highlighting substantive features, simplifying processing steps, and reducing duplication.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
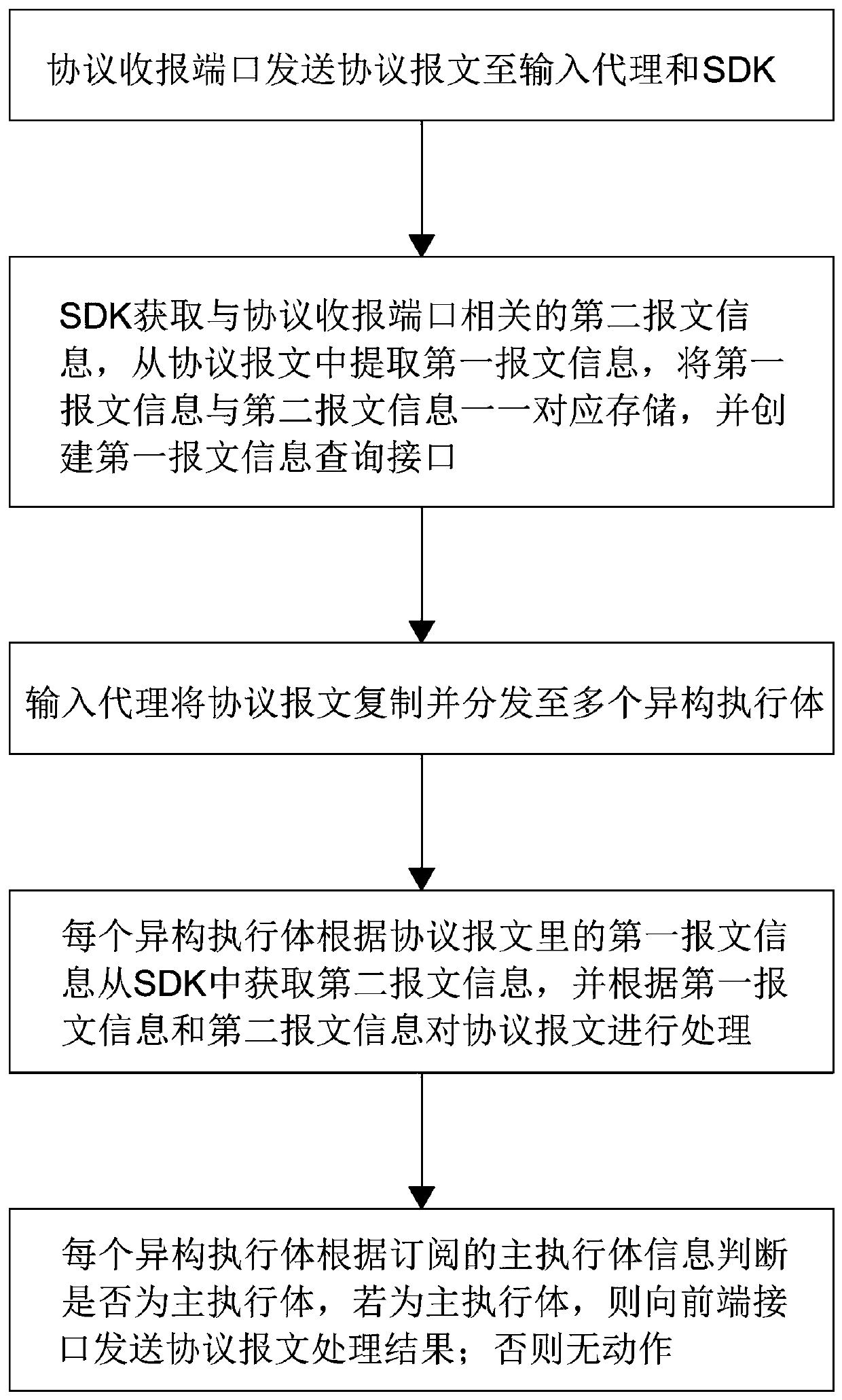
[0027] Such as figure 1 As shown, the first aspect of the present invention proposes a protocol message processing method based on mimic defense, including:
[0028] The protocol receiving port sends the protocol message to the input agent and SDK, and the protocol message includes the first message information; in specific applications, the designated protocol receiving port can be selected according to the type of the protocol message to perform the protocol message processing Send and receive
[0029] The SDK obtains the second message information related to the protocol receiving port, extracts the first message information from the protocol message, stores the first message information and the second message information in a one-to-one correspondence, and creates the first message Message information query interface; specifically, a table similar to the mac table can be created in the SDK to store the first message information and the second message information;
[0030] The in...
Embodiment 2
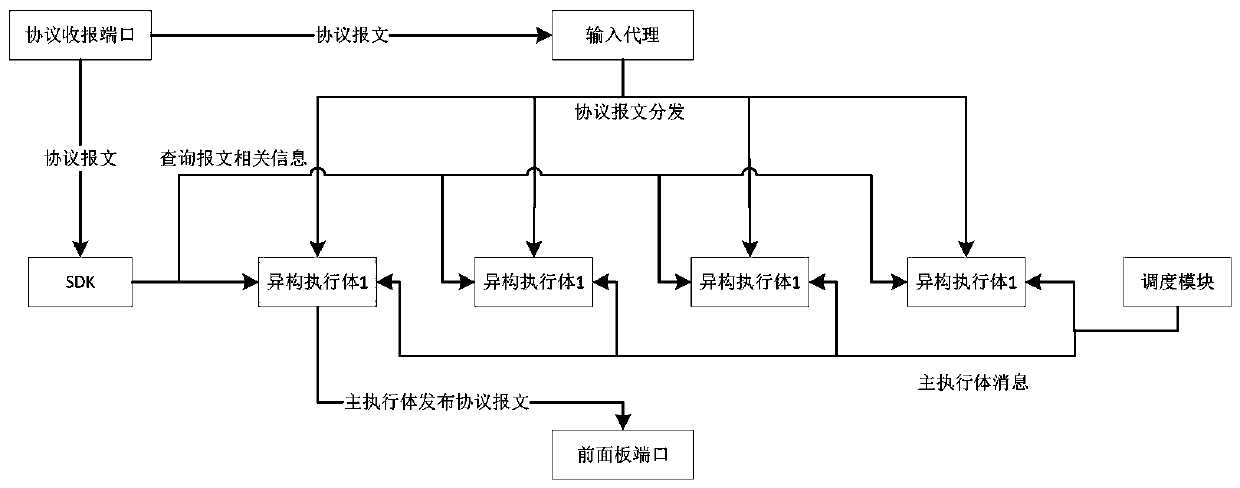
[0045] Such as figure 2 As shown, the present invention also provides a protocol message processing system based on mimic defense, including:
[0046] The protocol receiving port is used to receive and forward the protocol message, the protocol message including the first message information;
[0047] The SDK includes a message information acquisition module, a storage module, and a first message query interface. The message acquisition module is connected to the protocol receiving port for extracting first message information in the received protocol message, and Acquire the second message information related to the protocol receiving port; the storage module is used to store the first message information and the second message information correspondingly; the first message query interface is connected to the storage module , For querying whether the storage module has first message information according to the received first message query request, and returning corresponding se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com