Web injection code execution vulnerability detection method and system for Android application program
An Android application program and code execution technology, applied in the direction of creating/generating source code, software engineering design, computer security device, etc., can solve problems such as complex operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
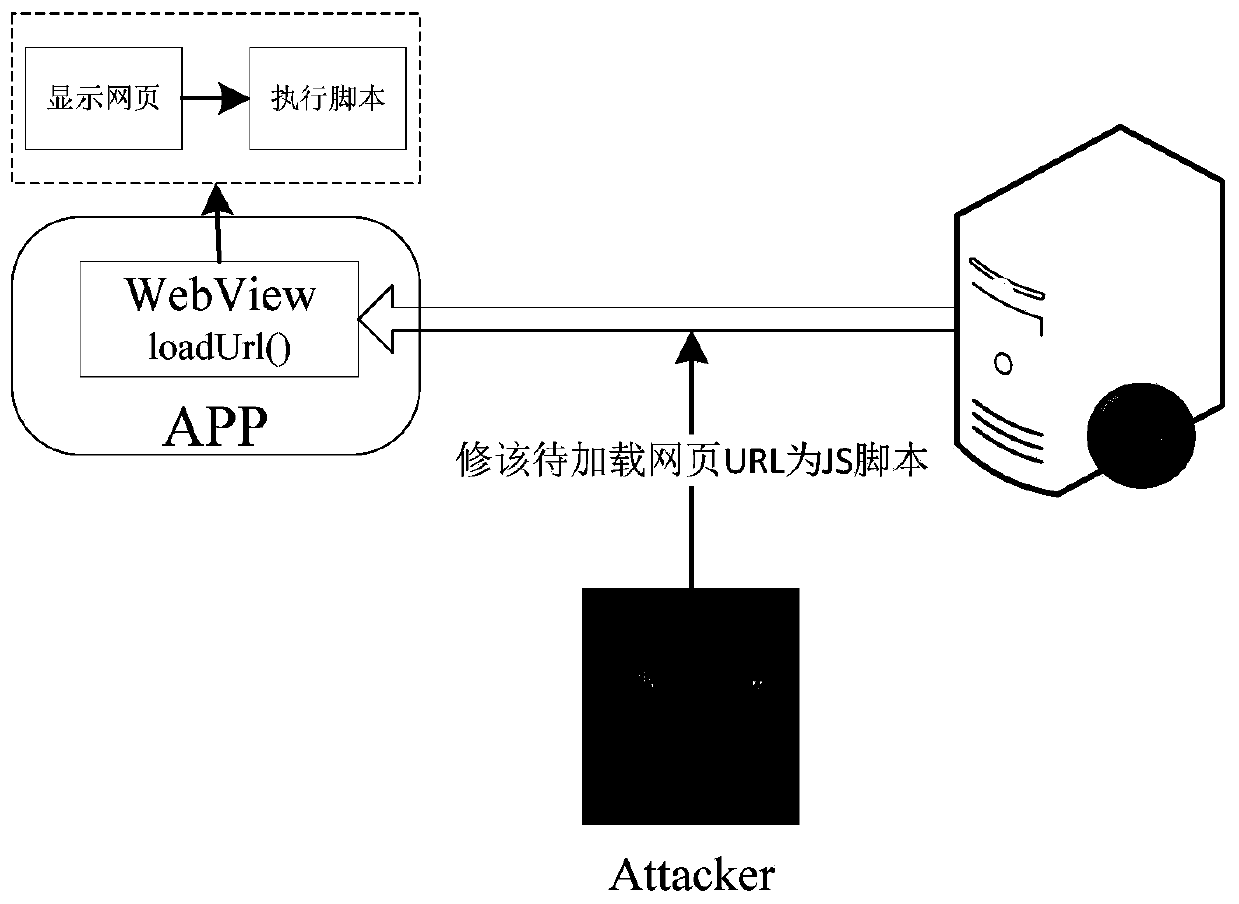
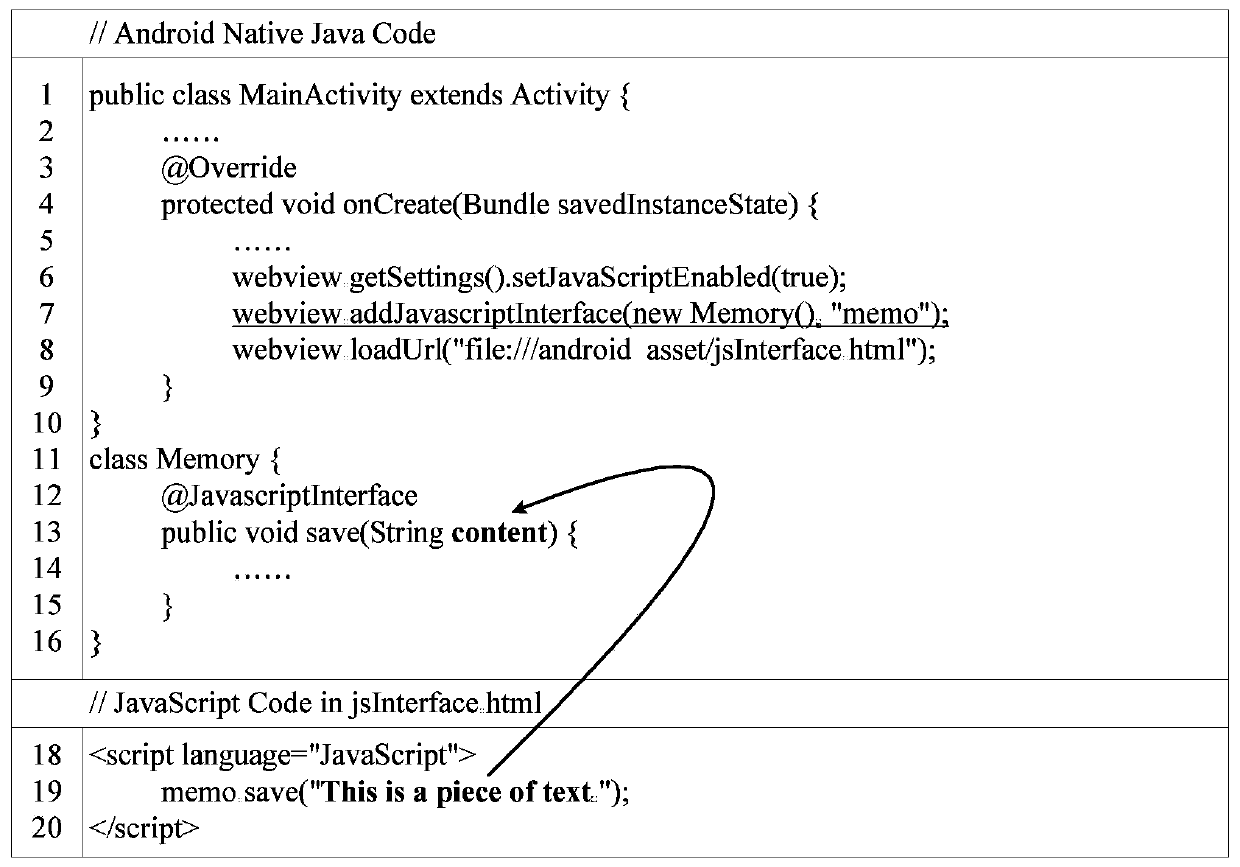
[0044] figure 1 This is an attack scenario diagram of exploiting Web injection code execution vulnerabilities, and summarizes the attack scenarios in which attackers exploit the vulnerabilities to implement injection script execution: Because different forms of method parameters make loadUrl() implement different functions, so when developers pass Web-Native across When the language communication interface passes the URL to loadUrl() to display the webpage, and the data loaded by loadUrl() is not verified in the application, the attacker can modify the URL of the webpage to be loaded to a JS (JavaScript) script through a middleman, making the application In the end, the page content is not displayed, but the JavaScript code is executed; for this kind of vulnerability exploitation, the existing research has not proposed a corresponding vulnerability detection method;
[0045] For this reason, the embodiment of the present invention proposes a method for detecting Web injection...
Embodiment 2
[0084] The present embodiment provides a web injection code execution vulnerability detection system for Android applications, including the following modules:
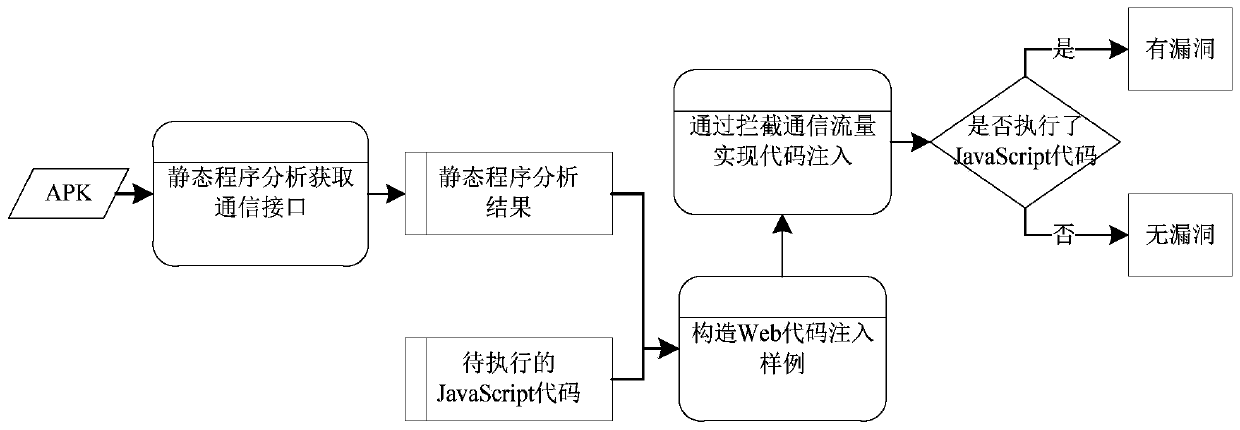
[0085] The static program analysis module is used to perform static program analysis on a given Android application, and obtain the Web-Native cross-language communication interface information that may cause Web injection code execution in the application;
[0086] The Web injection code sample construction module is used to select a string data as the Web data introduced by the Web-Native cross-language communication interface, based on the specific interface information and the selected string data in the static program analysis results, respectively for different The Web-Native cross-language communication mechanism completes the construction of Web injection code samples;
[0087] The Web injection code execution vulnerability detection module is used to intercept the communication flow between the application pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com