ELK-based log burying point service analysis alarm system and method
A business analysis and alarm system technology, applied in the field of data processing, can solve problems such as poor scalability of applications
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
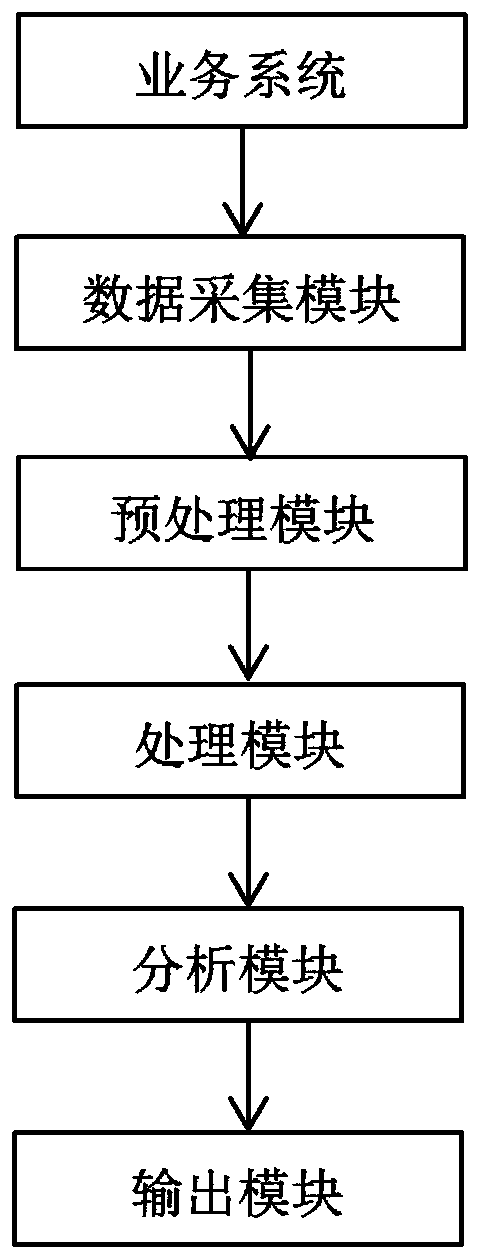
[0040] Such as figure 1 As shown, a business analysis and alarm system based on ELK-based log embedding includes a business system for performing business operations and saving business data, and generating original business log information; it also includes a data acquisition module, a preprocessing module, and a processing module , analysis module and output module, where:
[0041] The data collection module is used to collect the original log information of the business system;
[0042] The preprocessing module is used to receive the original log information and serialize the format of the original log information, read the application name, business indicators, application operating environment information, operating server and business occurrence time stamp of the original log information in the business system, and generate standard log information;
[0043] The processing module is used to collect standard log information through Logstash and push it to Elasticsearch,...
Embodiment 2
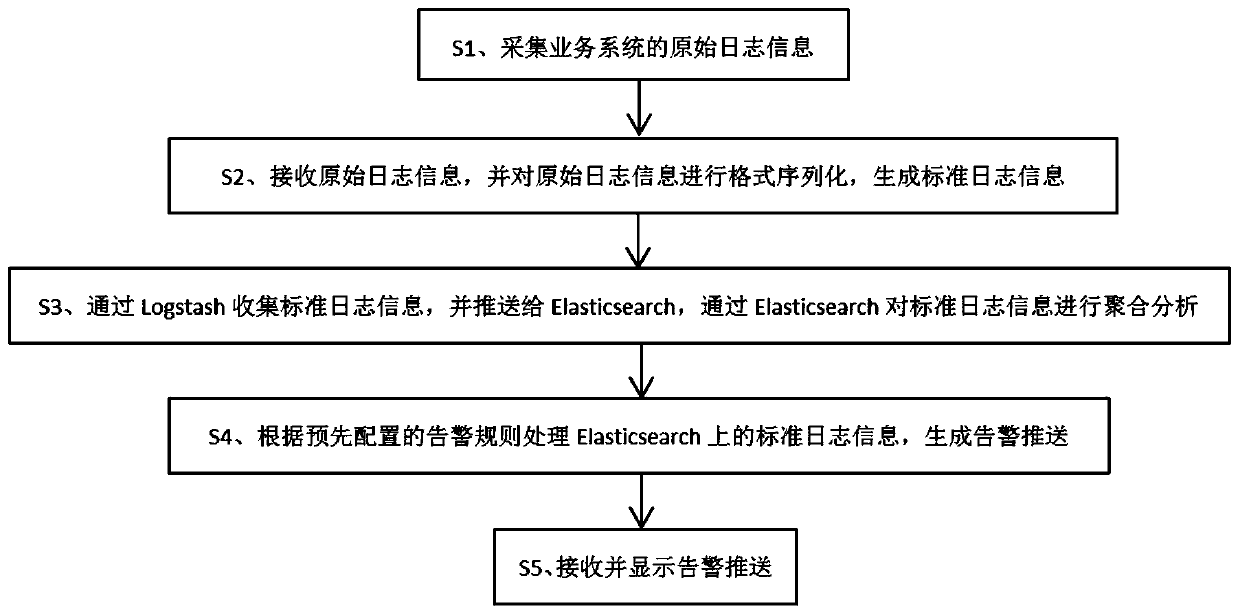
[0054] Compared with Embodiment 1, the only difference is that the preprocessing module in the business analysis alarm system is also used to determine whether the standard log information is qualified after the original log information is formatted and serialized to generate standard log information; If it is qualified, the standard log information will be output to Logstash for collection; if it is unqualified, the standard log information will be temporarily stored in the database, and the original log information will be extracted again to perform format serialization to determine whether the results of the two format serializations are consistent , if the content is the same, an alarm prompt will be generated; if it is different, the standard log information will be forwarded to Logstash;
[0055] Correspondingly, based on this system, the following steps are specifically included after step S2 in this embodiment: S21, judge whether the standard log information generated a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com