Speaker verification system and replay attack detection method thereof
A technology of speaker verification and replay attack, applied in the field of voiceprint recognition, it can solve the problem that the discrimination effect is not optimal, and achieve the effect of improving the accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
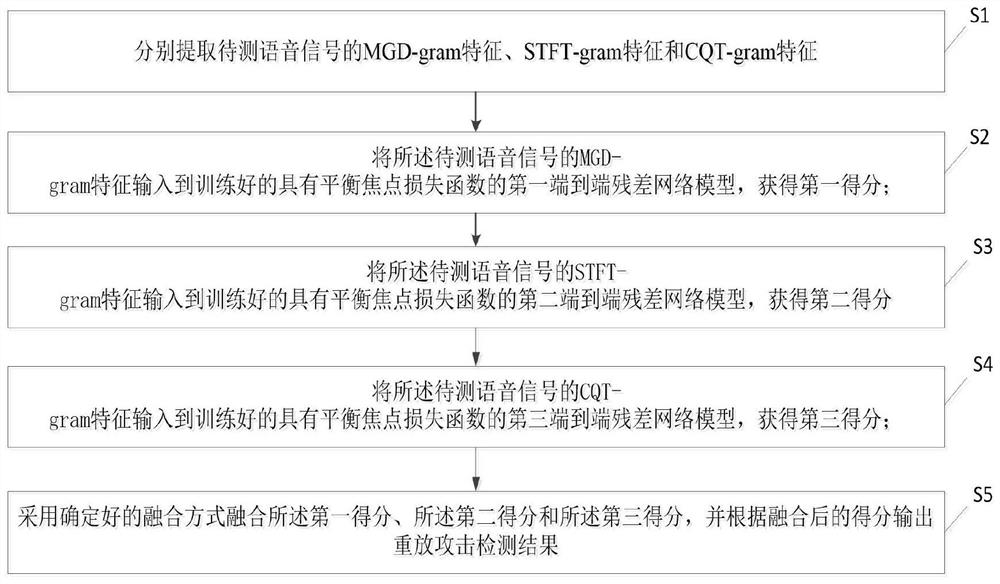
[0086] See figure 1 , Embodiment 1 of the present invention provides a replay attack detection method for a speaker verification system, including S1-S5;
[0087] S1: Extract the MGD-gram feature (Modified group delay, modified group delay), STFT-gram feature (STFT, short-time Fourier transform, short-time Fourier transform) and CQT-gram feature ( Constant Q transform, constant Q transform);
[0088] S2. Input the MGD-gram feature of the speech signal to be tested into a trained first end-to-end residual network model with a balanced focus loss function;
[0089] S3. Input the STFT-gram feature of the speech signal to be tested into a trained second end-to-end residual network model with a balanced focus loss function;
[0090] S4. Input the CQT-gram feature of the speech signal to be tested into a trained third end-to-end residual network model with a balanced focus loss function;
[0091] S5. Fuse the first score, the second score, and the third score in a determined fusi...
Embodiment 2
[0126] This embodiment also provides a speaker verification system, including:
[0127] In the second aspect, an embodiment of the present invention provides a replay attack detection system of a speaker verification system, including:
[0128] An extraction module is used to extract the MGD-gram feature, STFT-gram feature and CQT-gram feature of the speech signal to be tested respectively;
[0129] The first input module is used to input the MGD-gram feature of the speech signal to be tested to the trained first end-to-end residual network model with a balanced focus loss function to obtain the first score;
[0130] The second input module is used to input the STFT-gram feature of the speech signal to be tested into a trained second end-to-end residual network model with a balanced focus loss function to obtain a second score
[0131] The 3rd input module is used for inputting the CQT-gram feature of described speech signal to be tested to the 3rd end-to-end residual network...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com