Practical Byzantine fault-tolerant node setting method
A Byzantine and practical technology, applied in the field of communication, it can solve the problems of slow machine speed, waste of computing resources, robustness impact, etc., and achieve the effect of reducing the number of view changes, saving computing resources, and ensuring safe and reliable operation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
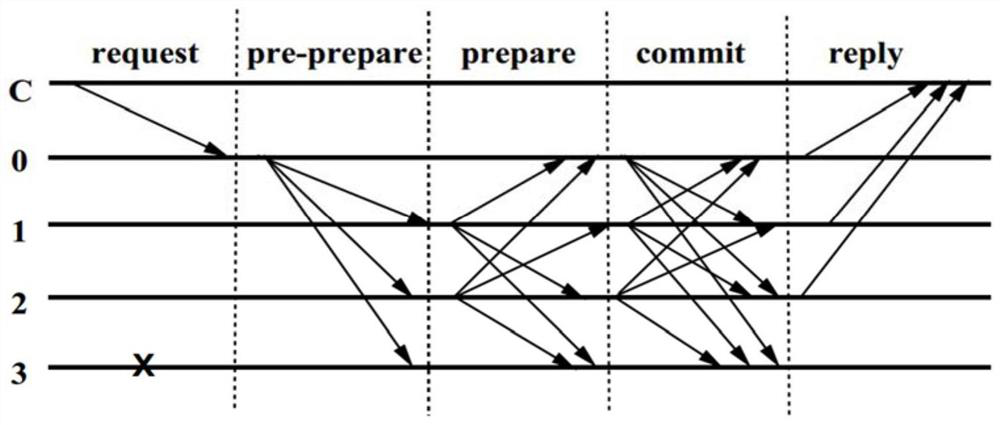
[0041] The following steps are taken as an example, all of which occur after a consensus process is completed, assuming that there are a total of N consensus nodes as the set of consensus nodes for this view. The implementation process of this embodiment refers to the attached image 3 .
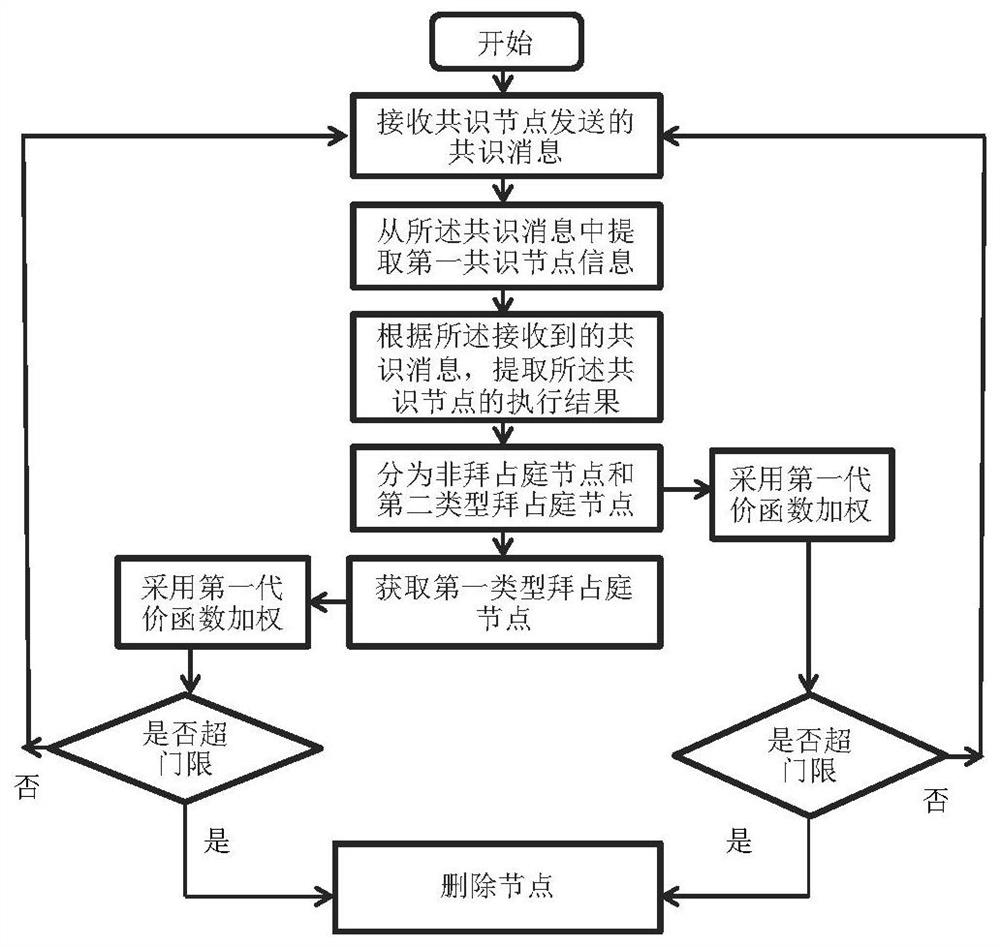
[0042] Step S102, receiving a consensus message sent by a consensus node, and extracting first consensus node information from the consensus message, where the first consensus node is a set of consensus nodes that send the consensus message.
[0043] Client C receives consensus messages sent by each consensus node. Among them, at least 2f+1 consensus nodes have replied to the client with a consistent consensus message, assuming that the number of consensus nodes reached is N0, and the remaining consensus nodes either did not reply to the message, or the reply message was consistent with that of N0 consensus nodes Replied messages are inconsistent. Client C extracts the information of the ...
Embodiment 2
[0063] In this embodiment, the relevant steps or functions implemented on the client C can be moved to the main consensus node P for processing.
[0064] Step S202, after the client receives the consensus message, it sends the consensus message to the main consensus node for processing
[0065] After each consensus node replies, the consensus result of the reply is collected and sent to the main consensus node, which should contain at least 2f+1 consistent consensus messages.
[0066] After the main consensus node P receives the consensus message from the client C, it extracts the consensus node information that sent the consensus message. The consensus node information can use information such as digital ID, machine name, IP address, MAC address, etc. The structure of the consensus information is , among them, the digital identification i of the consensus node is a regular parameter, and can also be replaced by other identification methods. In addition, r is the execution resu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com