Block chain storage encryption method based on attribute encryption
A technology of attribute encryption and encryption method, which is applied in special data processing applications, instruments, electrical digital data processing, etc., can solve the problems of user cost system energy consumption increase, system does not support user transactions, and the number of fault-tolerant nodes is small, etc., to achieve detailed Granular access control, secure sharing, and high throughput effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
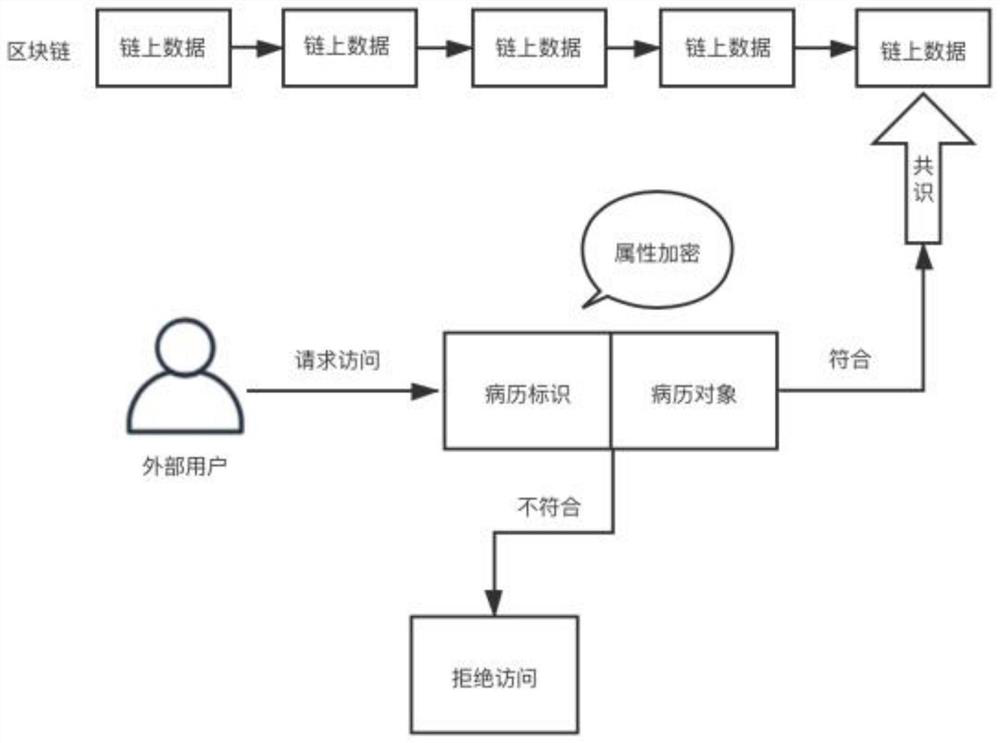
[0051] The present invention provides a storage encryption method on the block chain based on attribute encryption, specifically as figure 1 shown, including the following steps:
[0052] Step 1. External users request access to data on the chain;
[0053] Step 2. Check whether the external user meets the access conditions through the medical record identifier and medical record object set by the attribute encryption algorithm;
[0054] Step 3. If it does not match, deny access; if it does, use the consensus algorithm SCA to achieve the purpose of accessing the data on the chain.
[0055] Further, as figure 2 As shown, in step 3, the process of executing the consensus algorithm SCA is:
[0056] Step 3.1. Determine whether a consensus is reached; if so, return to the master node and wait for user requests; otherwise, execute step 3.2;
[0057] Step 3.2, execute the practical Byzantine fault tolerance algorithm;
[0058] Step 3.3. Continue to judge whether a consensus is r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com