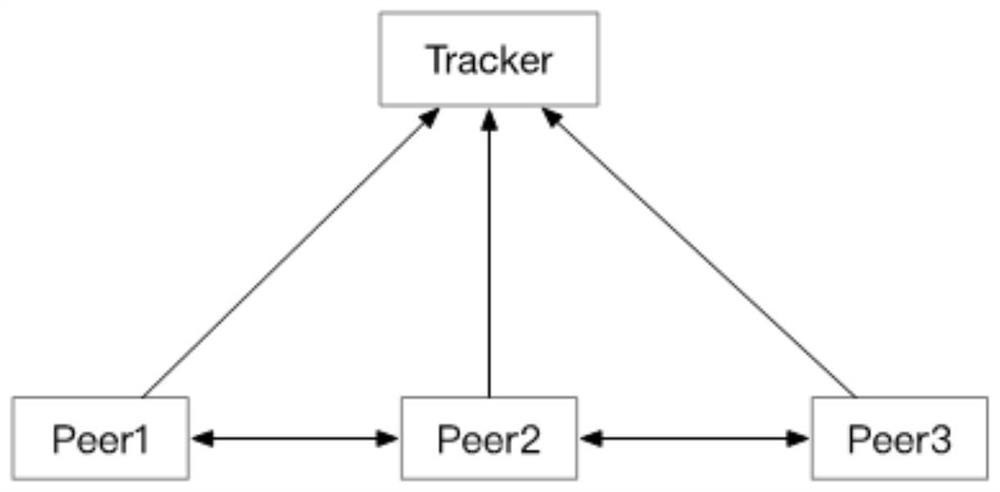
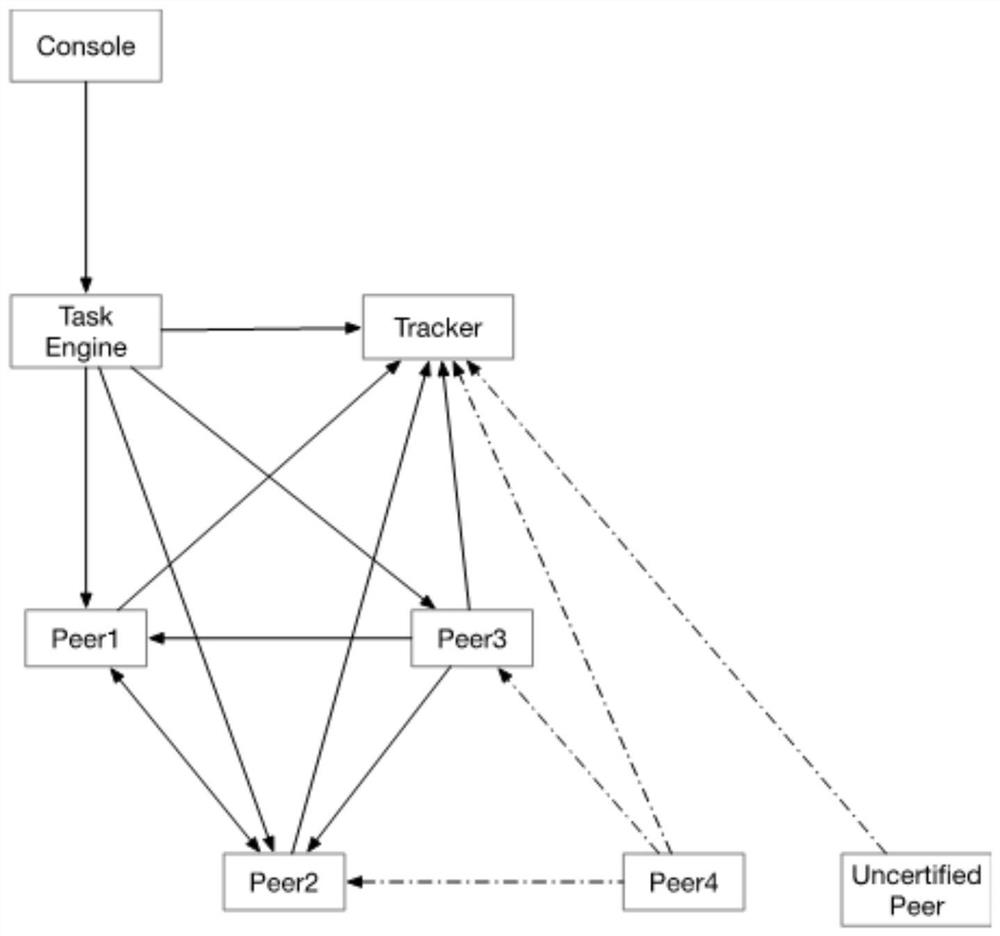
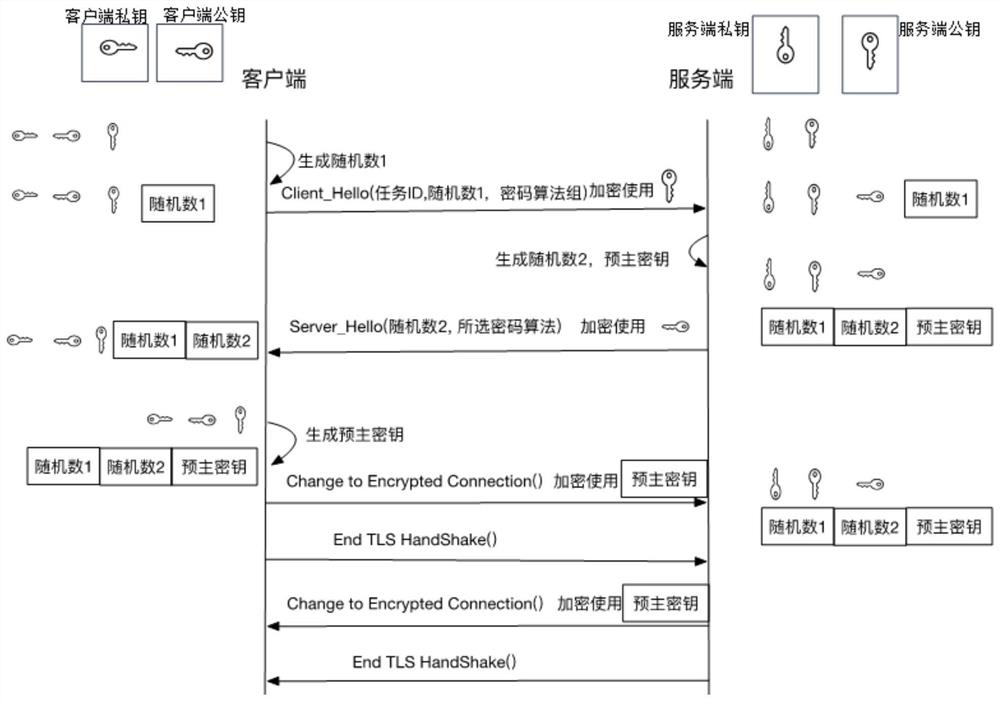
Efficient trusted transmission method based on P2P
A transmission method and credible technology, applied in the field of communication, can solve the problems of lack of trusted network node management function, difficulty in meeting information security transmission, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] Common methods of using asymmetric encryption algorithms are as follows: Generate a set of key pairs through the algorithm, the private key of which is kept secretly by the owner (A), the public key can be sent to anyone, and B encrypts the information with the public key and sends it to A. Even if it is obtained by C during the transmission process, the data cannot be decrypted. Only A can decrypt the data through the private key. As long as the private key is not leaked, the data is safe.
[0025] BitTorrent Protocol: BT protocol for short, the BitTorrent protocol is a P2P file transfer communication protocol based on the TCP / IP protocol, and is at the application layer of the TCP / IP structure. The BitTorrent agreement itself also includes many specific content agreements and extension agreements, and is constantly expanding.
[0026] TLS: Transport Layer Security (English: Transport Layer Security, abbreviated as TLS), and its predecessor Secure Sockets Layer (Secure...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com