Malicious certificate detection method
A detection method and certificate technology, which is applied in the field of malicious certificate detection, can solve the problems of limited scope and low accuracy of malicious certificates, and achieve the effect of wide coverage and high accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
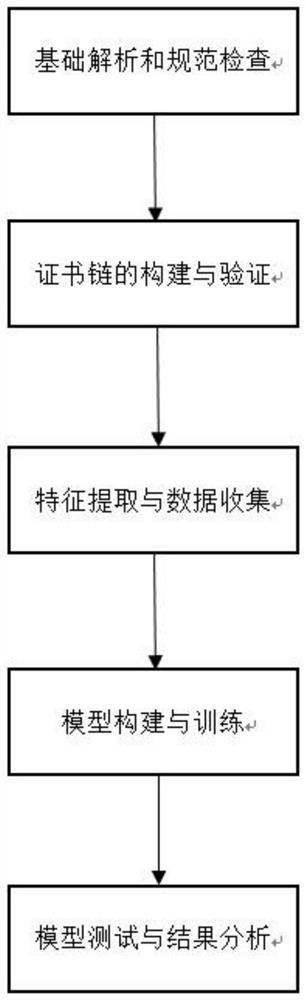
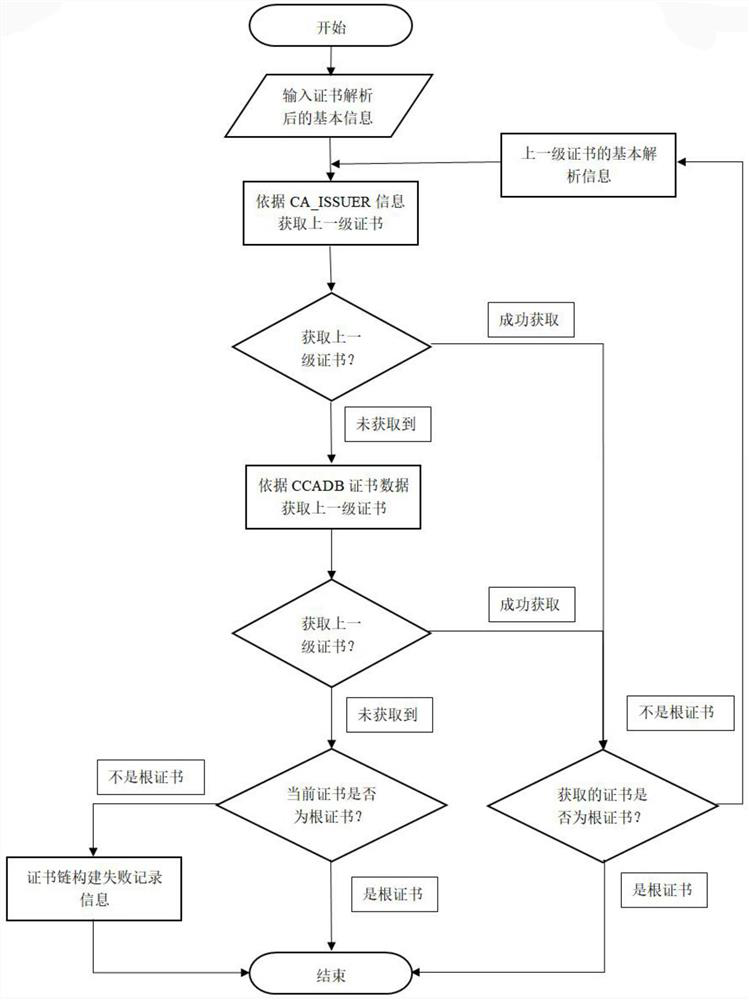
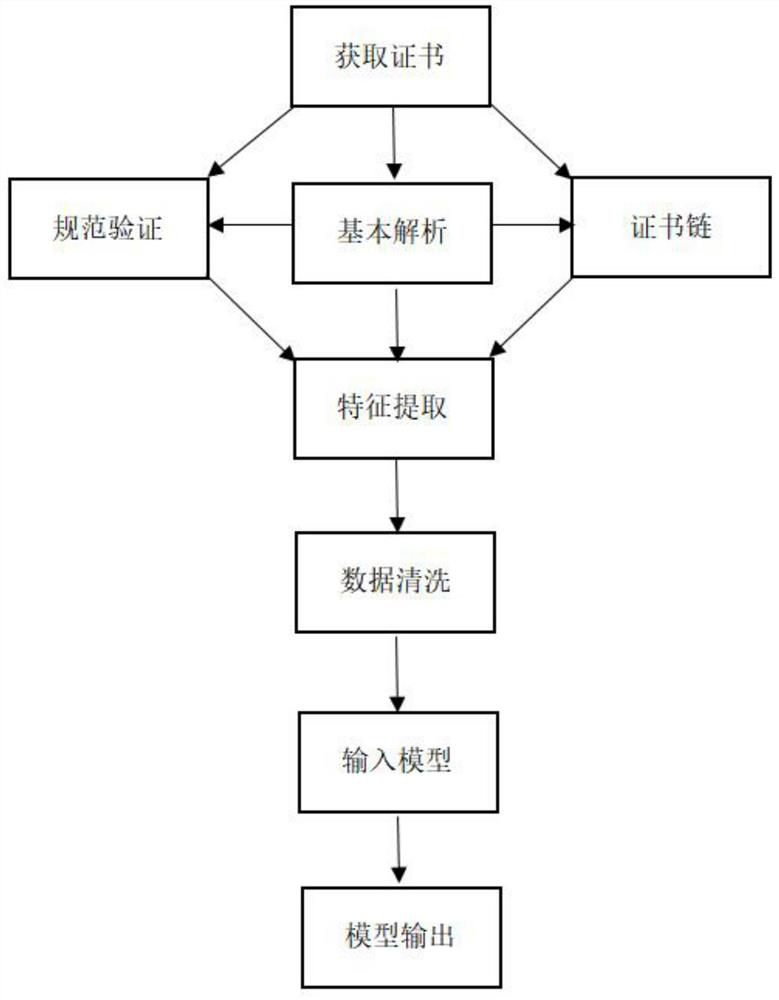
[0042] Embodiment 1: as Figure 1-3 As shown in the figure, they are respectively the working flow chart of the model of the present invention, the building flow chart of the certificate chain and the flow chart of the certificate verification data.
[0043] The present invention first conducts basic content analysis and normative inspection on the certificate based on Cryptography and RFC 5280, initially obtains the basic information of the certificate and judges whether it conforms to some norms and constraints of RFC 5280, and records relevant information. This process mainly includes the following steps:
[0044] Step (1): Import, convert and store the certificates in pem and cer formats that may be entered.
[0045] Step (2): Obtain the basic information and possible extended information of the X.509 certificate according to Cryptography.
[0046] Step (3): Based on RFC 5280, check some normative constraints involved in the document and record related check information....
Embodiment 2
[0068] In the process of basic parsing and verification of the input X.509 certificate, in addition to extracting some basic information about the certificate subject, certificate issuer, certificate extension and public key usage stored in the certificate itself. Innovatively use some restrictions in RFC 5280, such as decipher_only and encipher_only in the use of the certificate public key are only allowed to be set in the use of the public key when the key_agreement is set to true, and whether the serial_number is represented by no more than 20 bytes The largest positive integer of , and so on. Carefully integrate and check the restrictions on canonical certificates in the RFC 5280 document, and record relevant information. This completes the basic parsing and information checking of the certificate.
Embodiment 3
[0070] The certificate chain is a complete list of certificates from the end certificate to the root certificate. The signatures of all certificates except the root certificate in the list can be verified by the public key of the upper-level certificate. In addition to the basic signature verification, the verification of the certificate chain also includes whether the purpose of the certificate matches, whether the certificate policy matches, whether it meets the name constraints of the certificate, and whether it meets the policy constraints of the certificate, etc. This information needs to be detected during the verification process of the certificate chain, and this also generates some related information. Doing this process for each certificate in the certificate chain can check whether there are some problems with the intermediate certificates.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com