Malicious software family classifier generation method and device based on weak coupling SGAN and readable storage medium
A malware and classifier technology, applied in computer security devices, instruments, computer parts, etc., can solve the problems of poor malware effect, large delay and cost, and achieve the improvement of feature extraction efficiency, accuracy and reliability. The effect of the scope of application
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments. It should be understood that the specific implementations described here are only used to explain the present invention, not to limit the present invention.
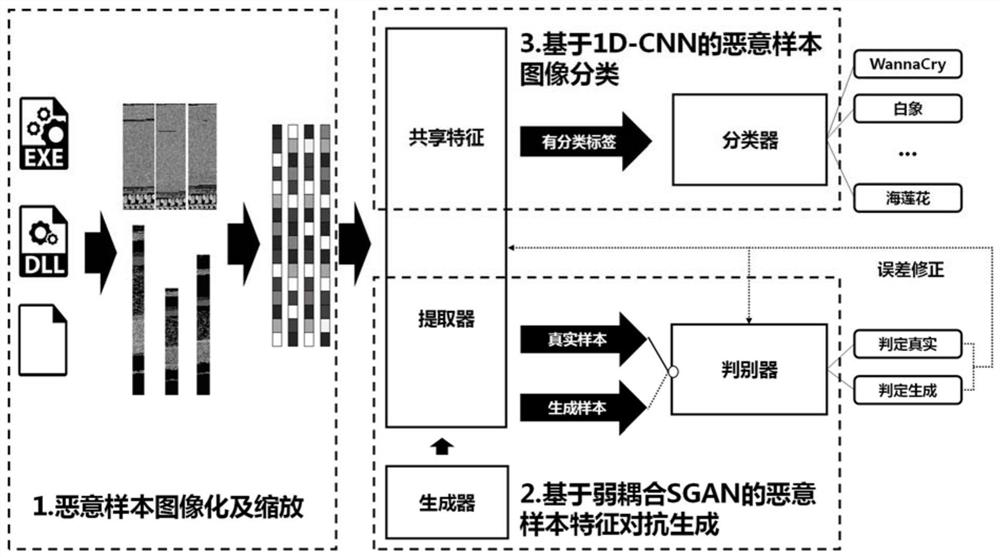
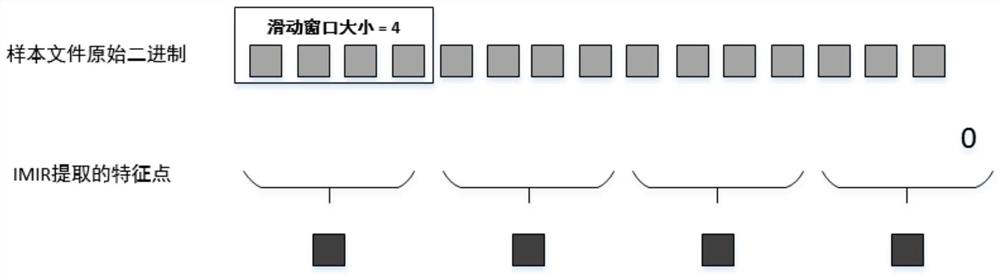
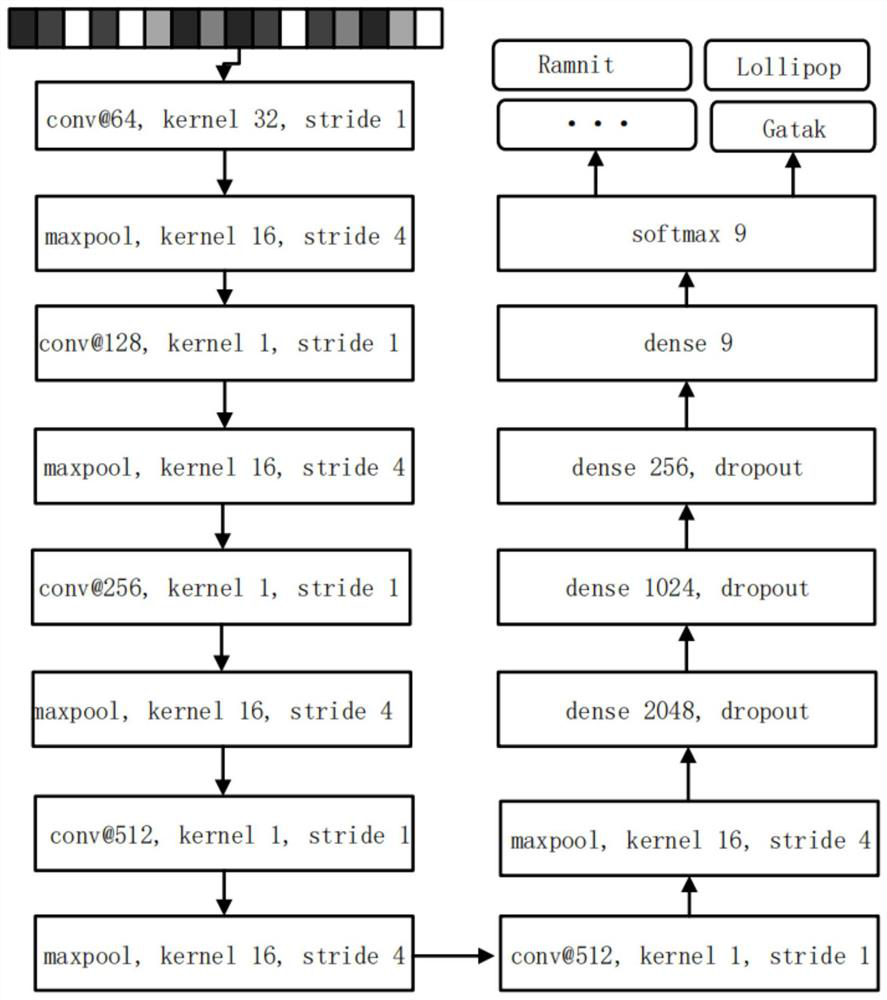
[0035] Existing feature extraction technologies, especially dynamic behavioral features, will generate relatively large delays and costs, and the goal of using deep learning technology is to quickly classify malware families through the classifiers generated by training. Therefore, the present invention employs malware image scaling techniques that directly convert malware binaries into images. Because the traditional image scaling technology directly compresses and stacks the 1-dimensional files generated by the binary files into 2-dimensional image files according to the fixed width, this met...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com