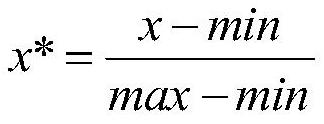Intrusion detection method based on partial deep learning theory
A technology of deep learning and intrusion detection, applied in neural learning methods, computer systems based on knowledge-based models, branch and bound, etc., can solve problems such as poor real-time model performance and no specific evaluation of model prediction time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] In order to make the technical solution of the present invention clearer, the present invention will be further elaborated below in conjunction with the accompanying drawings.
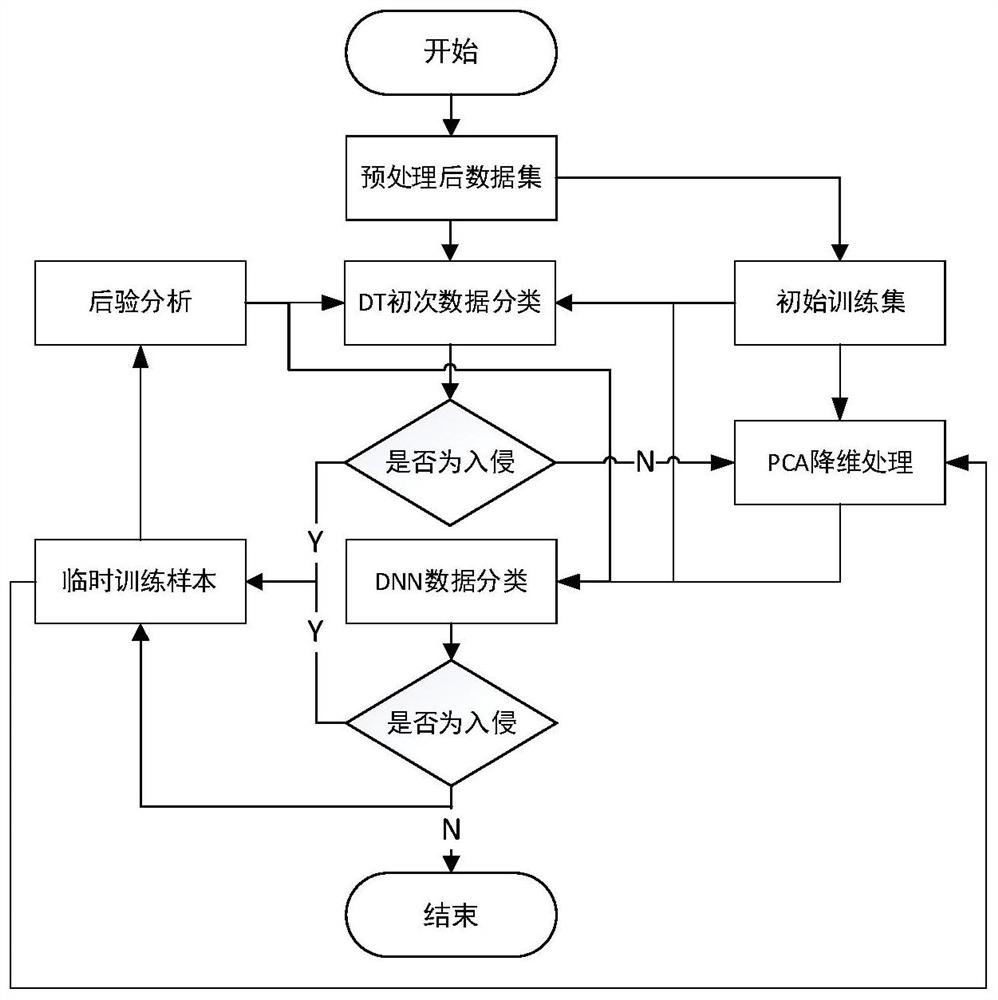
[0021] The invention provides an intrusion detection method for detecting network data by using part of deep learning theory. The specific implementation steps are as follows:
[0022] The first step is to prepare the dataset:
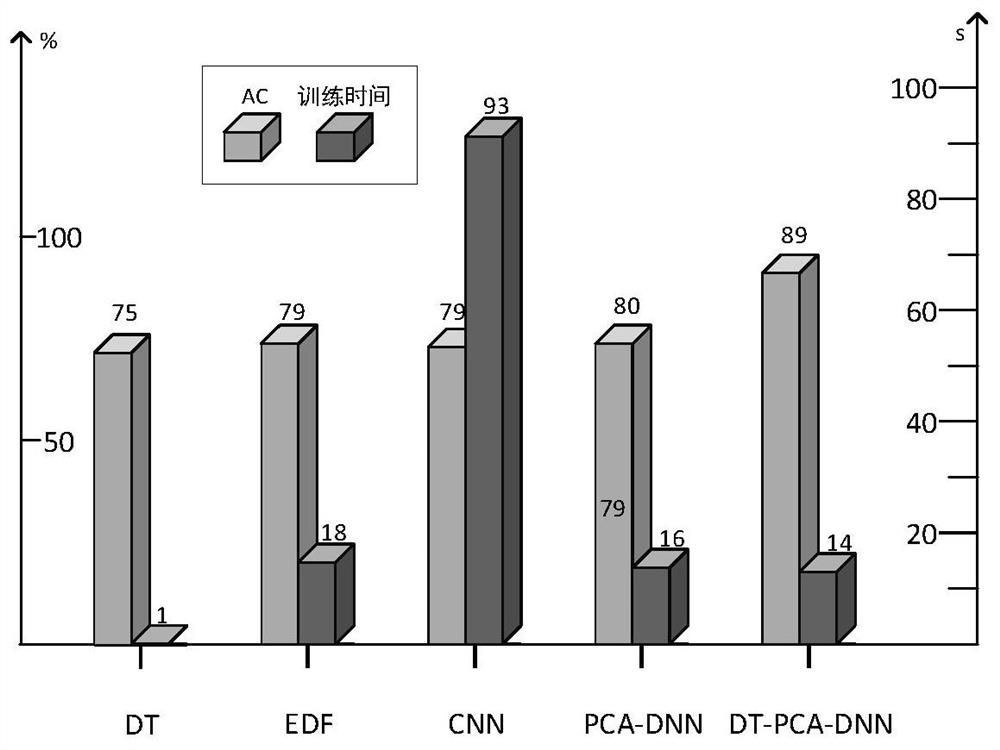
[0023] (1) Prepare the data required for training and testing. The data set used in the present invention is an NSL-KDD data set used for intrusion detection without preprocessing. The data set has a total of 125,937 pieces of data in the training set and 22,544 pieces of data in the test set. There are 41 types of features, which are divided into four major feature categories: basic features of TCP connections, operating features on hosts, time-based network traffic statistics features, and host-based network traffic statistics features. Firstly, it is calibrated as...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com