Method and system for protecting software source codes based on Linux kernel calling
A software source and file system technology, applied in digital data protection, platform integrity maintenance, instruments, etc., can solve problems such as leakage, unpacking APK file leakage, core code logic leakage, etc., and achieve high security performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
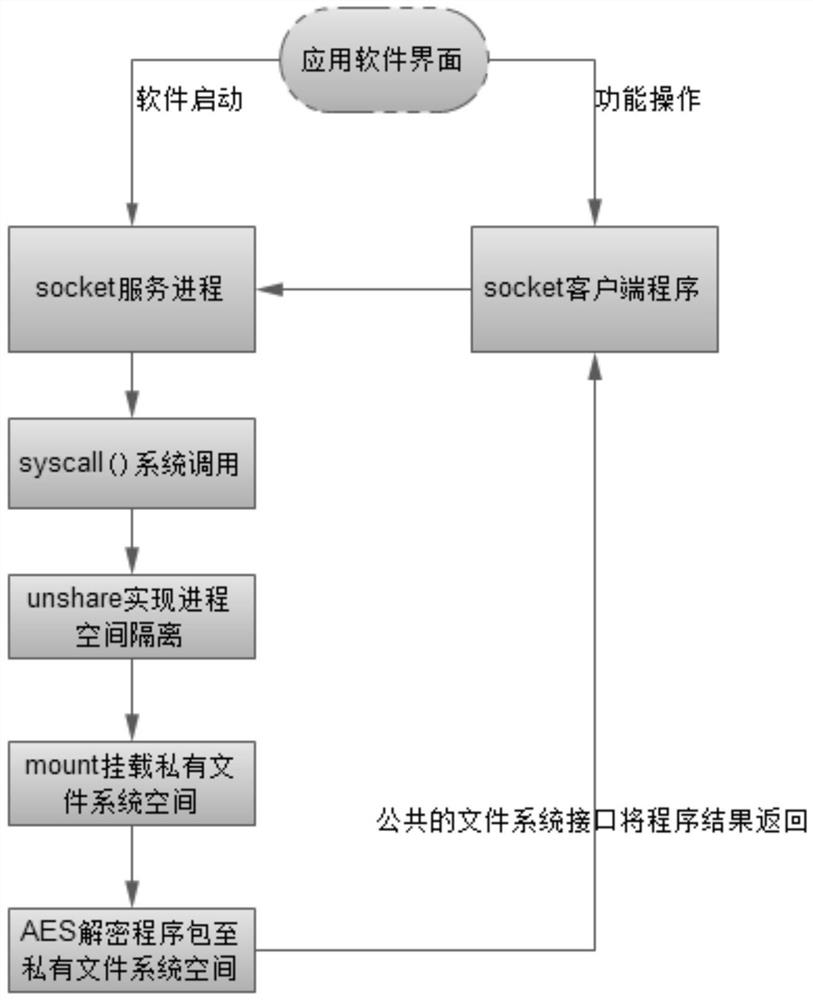
[0025] Please refer to Figure 1-Figure 2 , the protection method that realizes software source code based on Linux kernel calling comprises the following steps:
[0026] S1: Add a system call interface in the Linux kernel to provide resource protection that the Android application layer program can directly call to implement the process, such as: SYSCALL_DEFINE3(unshare_test, const char__user*, filename, char__user*, mount_point, char__user*, password), the System calls implement the following functions:
[0027] Obtain the file system mount point passed by the application layer, the AES encrypted file path, and the system call to verify the random password through copy_from_user();
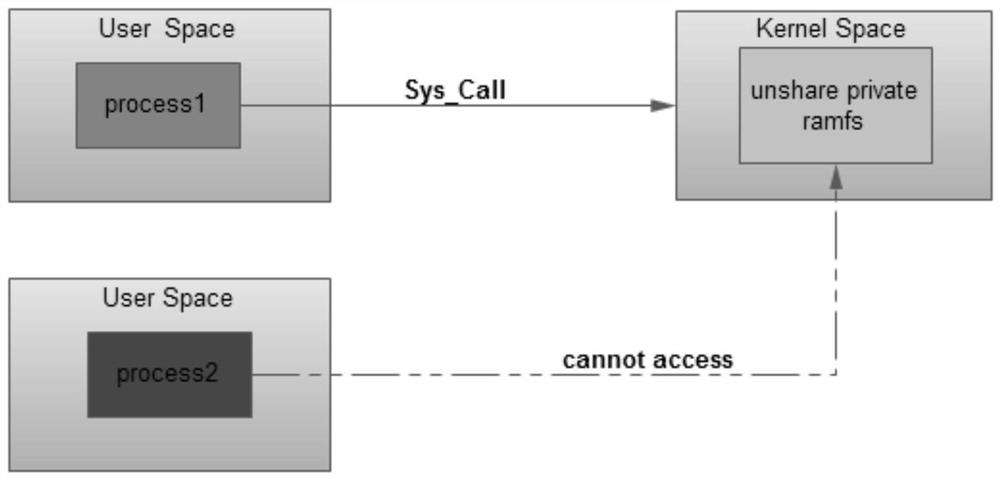
[0028] Enable process isolation by calling the unshare kernel interface to realize the isolation of process space and its file system space;
[0029] Create a process ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com