Attack countering method and system based on RDP disk mapping
A technology of disk mapping and control method, which is applied in the field of network security, can solve the problems of high cost, uncontrollable effect, and no specific technology for countering attackers, and achieve low-cost effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
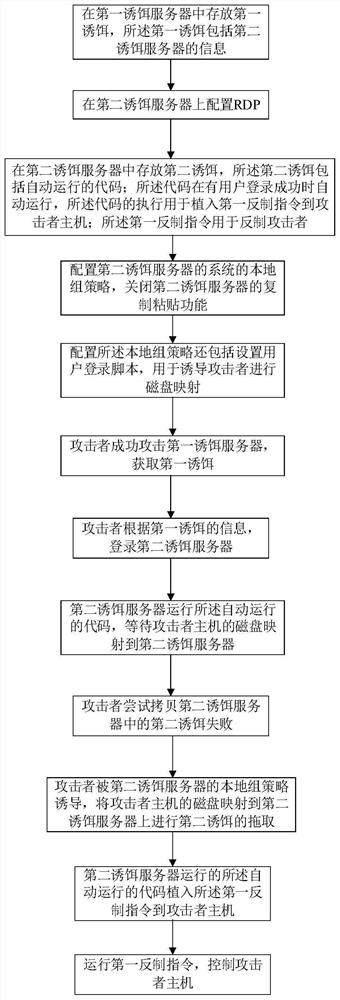
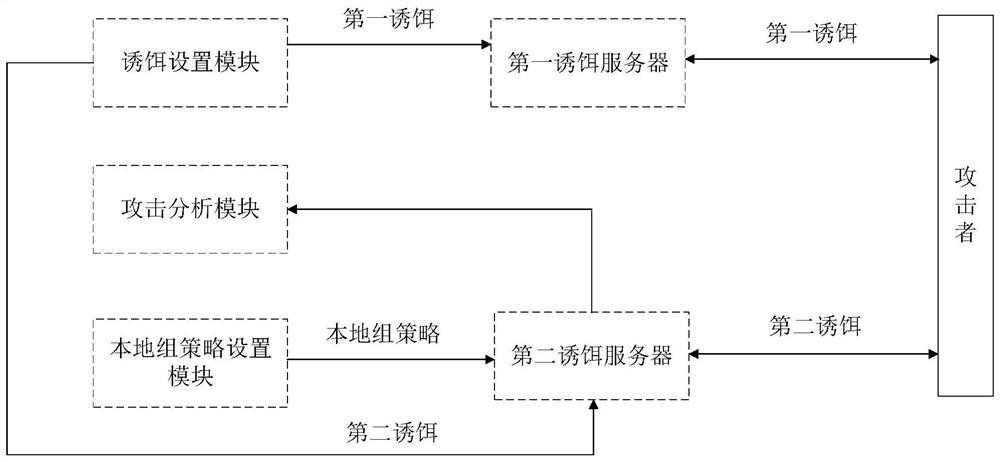
[0101] Refer to attached Figure 1-2 , according to a specific embodiment of the present invention, the method for obtaining the password hash of the windows system account provided by the present invention is described in detail.
[0102] The present invention provides a kind of attack countermeasure method based on RDP disk mapping, comprises the following steps:
[0103] The first decoy server build step,
[0104] storing the first decoy in the first decoy server, the first decoy including the information of the second decoy server;
[0105] The information of the second decoy server includes credentials for logging into the second decoy server; the information of the second decoy server stored in the first decoy server includes: the IP address, login account and login password of the second decoy server.
[0106] Attackers are usually interested in login credential information. The first decoy stores information including the second decoy server, and the information of t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com