Quantum key distribution method and system for authentication based on post-quantum cryptography algorithm
A technology of quantum key distribution and quantum cryptography, which is applied in the field of quantum communication network systems, can solve the problems of labor costs, high travel and transportation costs, inability to obtain guarantees, time-consuming and labor-intensive problems, and improve convenience and feasibility. Increase interoperability and enhance the effect of security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
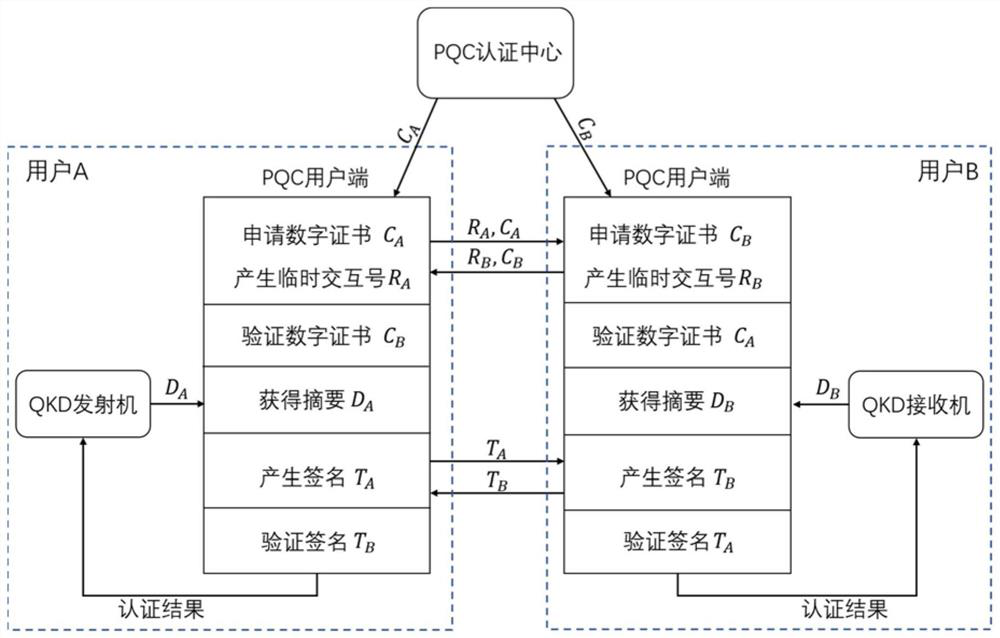
[0041] Embodiment 1: A point-to-point quantum key distribution method for authentication based on the PQC algorithm
[0042] A quantum key distribution method and system for authentication based on the PQC algorithm according to the present invention, such as figure 1 As shown, this embodiment includes the following steps:
[0043] User A and user B act as the transmitter and receiver of QKD respectively. The PQC clients of both parties respectively generate public-private key pairs based on the PQC algorithm (S A ,P A ) and (S B ,P B ), the two parties send their identity information and the generated public key to the PQC certification center CA, and apply for a digital certificate from the CA. After verifying the identities of the two, the CA sends the digital certificate signed by the CA to user A and user B respectively. C A and C B , the digital certificate contains the identity information and public key information of the user authenticated by the CA. CAs are r...
Embodiment 2
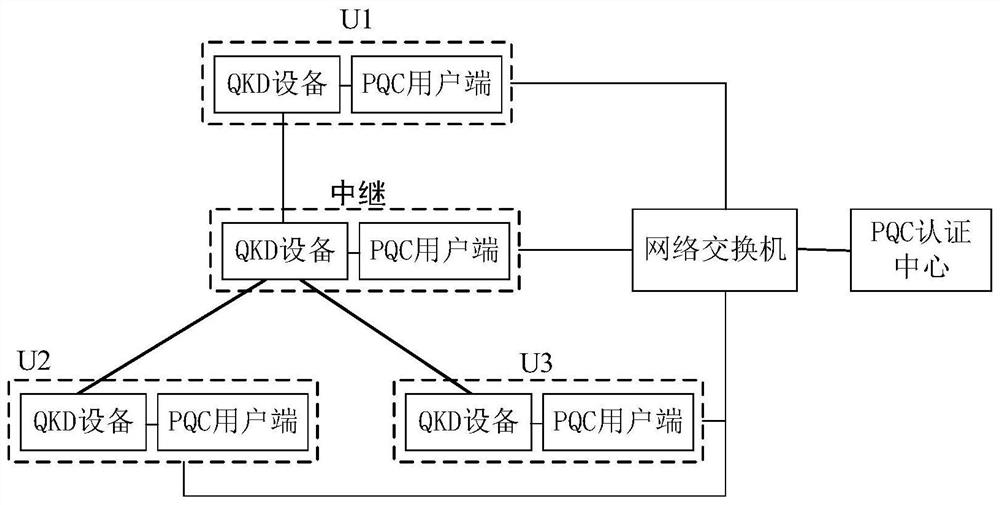
[0049] Embodiment 2: QKD star relay network for authentication based on PQC algorithm
[0050] What the embodiment of the present invention described is a star QKD relay network for authentication based on the PQC algorithm, such as figure 2 As shown in the figure, 3 users and 1 trusted relay are taken as an example, all other embodiments obtained by those skilled in the art without creative work, such as changing the number of users or increasing the number of relays, Or change the network topology, which all belong to the protection scope of the present invention. This embodiment includes the following steps:
[0051] U1, U2 and U3 represent 3 users. Each user and relay has one or more sets of QKD equipment and PQC user end equipment. QKD equipment can be a transmitter or a receiver, or a transmitter-receiver integrated machine. The QKD device is connected with the PQC client and can transmit the summary and authentication results. The PQC client can be set independent...
Embodiment 3
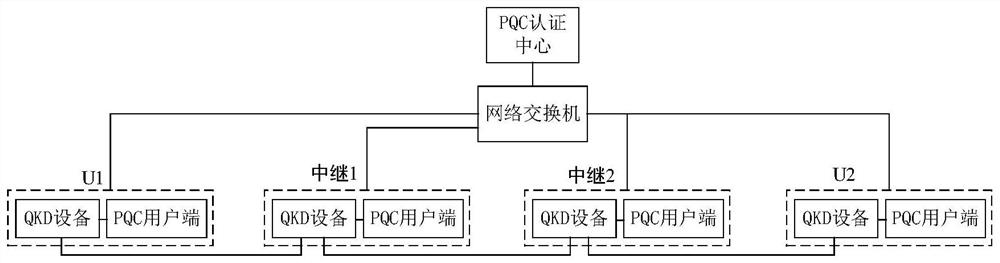
[0056] Embodiment 3: QKD chain relay network for authentication based on PQC algorithm
[0057] Described in the embodiment of the present invention is a chain-type QKD relay network for authentication based on the PQC algorithm, such as image 3 As shown in the figure, 2 users and 2 trusted relays are taken as an example, all other embodiments obtained by those skilled in the art without creative work, such as changing the number of users or increasing the number of relays, Or change the network topology, which all belong to the protection scope of the present invention. This embodiment includes the following steps:
[0058] U1 and U2 represent two users, and relay 1 and relay 2 represent two trusted relays. Each user and relay has one or more sets of QKD equipment and PQC user end equipment. QKD equipment can be a transmitter or a receiver, or a transmitter-receiver integrated machine. The QKD device is connected with the PQC client and can transmit the summary and authe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com