Block replacement generation type information hiding and recovering method, equipment and medium
An information hiding and generative technology, which is applied in the intersection of information security and information hiding without carrier, can solve the problems of low embedding capacity of single carrier, expensive retrieval and maintenance, and limited expression ability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0141]It should be noted that the terms "comprising" and "having" in the description and claims of the present invention and the above drawings, as well as any variations thereof, are intended to cover a non-exclusive inclusion, for example, including a series of steps or units A process, method, system, product or device is not necessarily limited to those steps or elements explicitly listed, but may include other steps or elements not explicitly listed or inherent to the process, method, product or device.
[0142] The present invention is described in further detail below in conjunction with accompanying drawing:
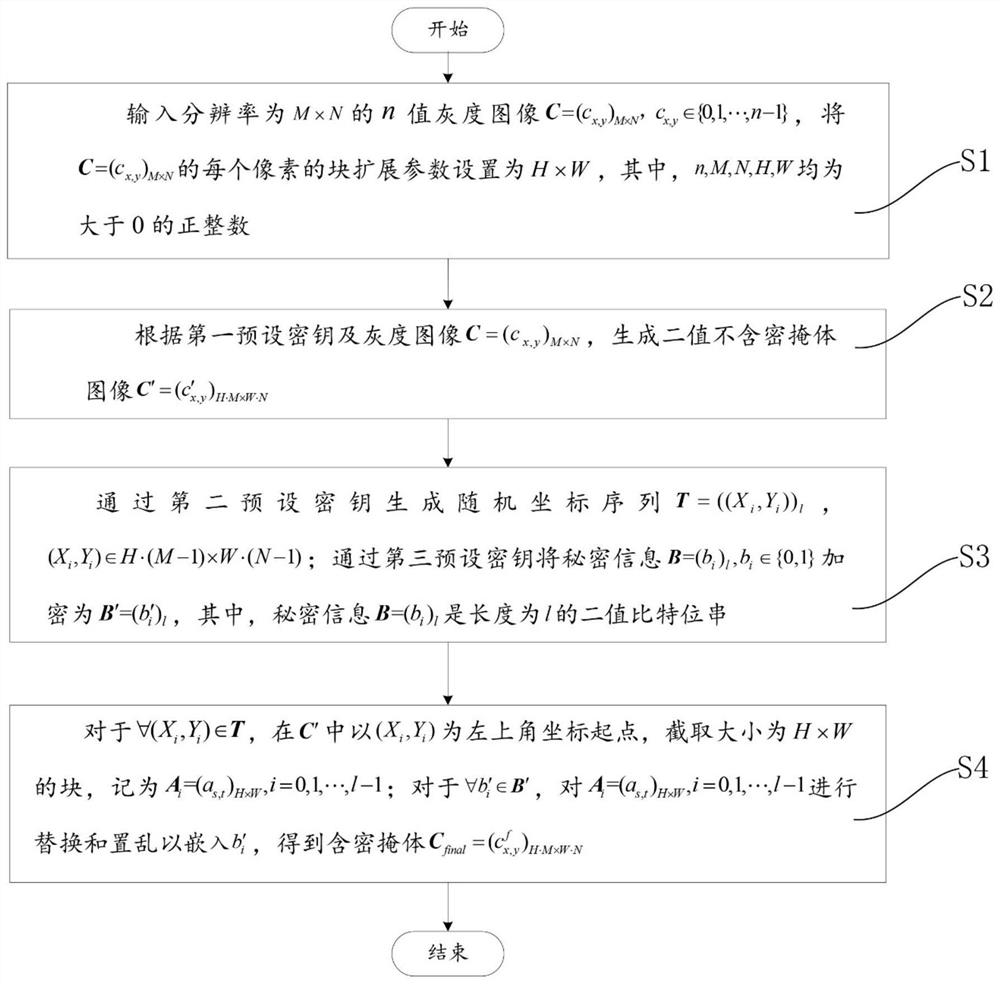
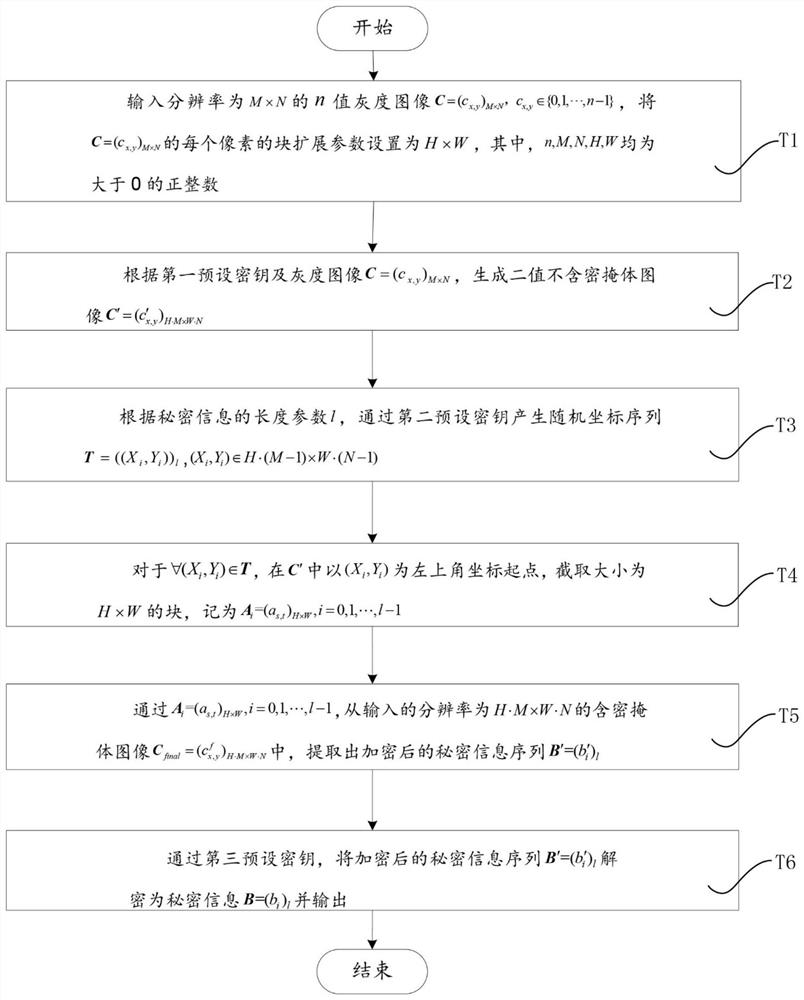
[0143] The following takes JAVA jdk1.8.0_65 as the implementation environment of the case, and describes the implementation of the present invention in detail in conjunction with the accompanying drawings, but is not limited to this implementation case, see figure 1 , in one embodiment of the present invention, a block replacement generative information hiding me...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com