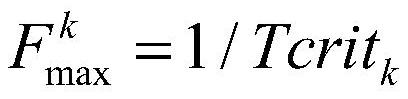Integrated circuit hardware Trojan horse detection method based on multi-parameter bypass analysis
A hardware Trojan detection and integrated circuit technology, which is applied to computer components, internal/peripheral computer component protection, instruments, etc., to achieve the effects of reducing impact, high detection accuracy, and overcoming single feature selection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
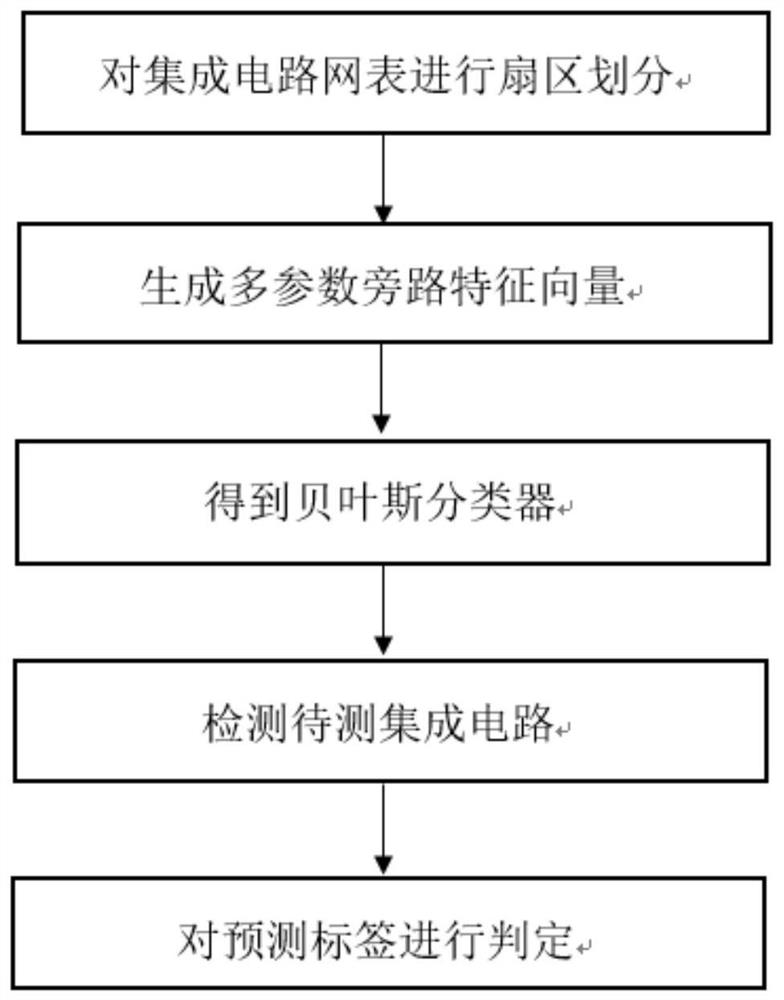
[0031] Attached below figure 1 , to further describe in detail the specific steps for realizing the present invention.
[0032] Step 1, sectorize the IC netlist.
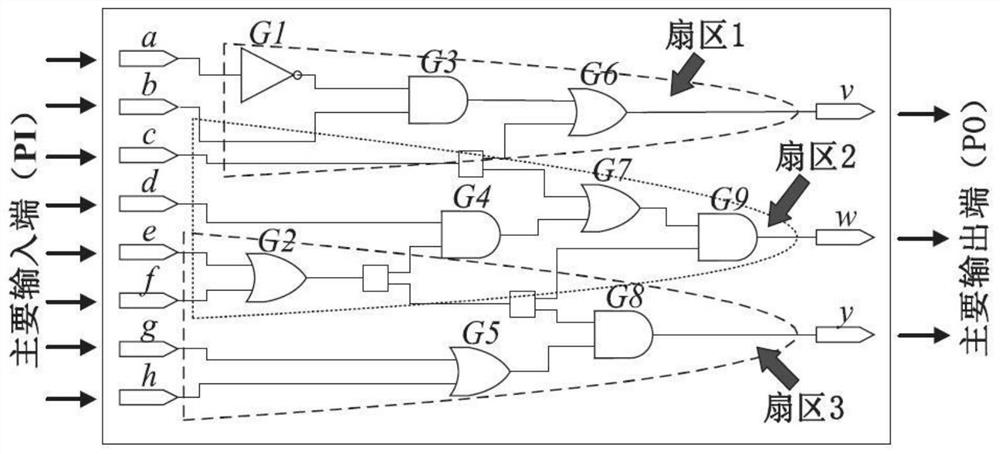
[0033] Select 1 integrated circuit (Integrated Circuit, IC) netlist without Trojan horse and 2 integrated circuit netlists with Trojan horse, start with each main output end of the integrated circuit netlist, and gate along the main output end The connection between the circuits is reversely searched, and it stops when it reaches the main input terminal corresponding to the main output terminal, and all the gate circuits found and the connection between them are divided into a sector, and the integrated circuit netlist is finally divided The number of sectors is the same as the number of main output terminals of the integrated circuit netlist.
[0034] The path with the longest path delay in each sector is selected as the critical path.
[0035] Combine below figure 2 Further describe the sector division.
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com