Intelligent contract execution method supporting trusted execution environment
A smart contract and execution environment technology, applied in the blockchain field, can solve problems such as poor computing efficiency, inability to make full use of smart contract scalability, and poor smart contract scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
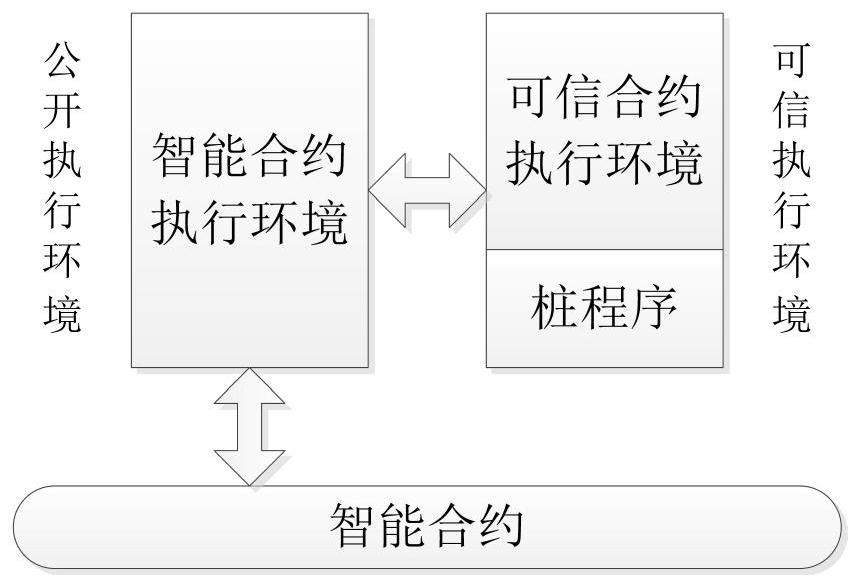
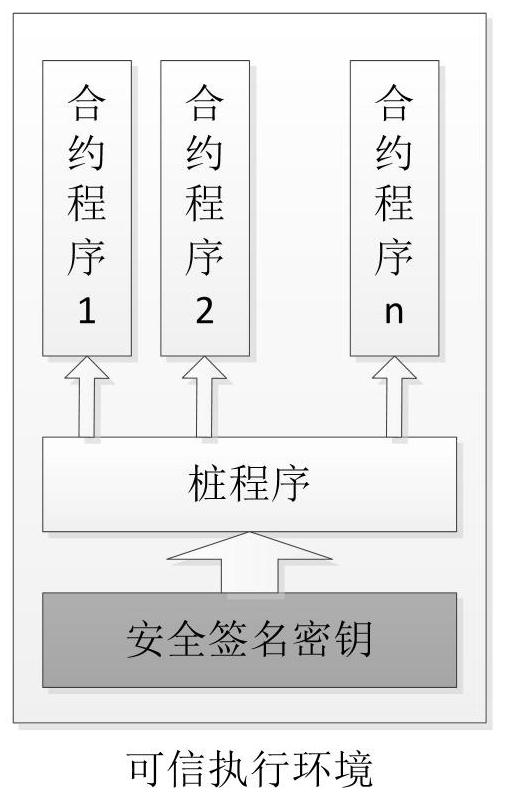
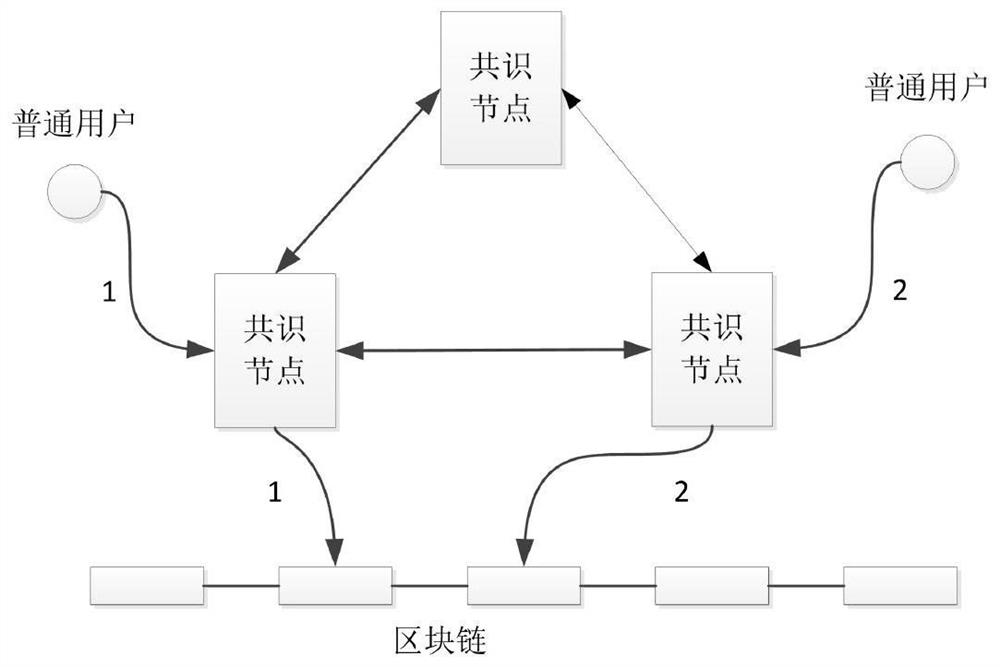
[0032] Such as Figure 1-4 As shown, the present invention provides a smart contract execution method that supports a trusted execution environment. The blockchain consensus node monitors and collects transaction requests, and obtains smart contracts deployed on the blockchain. Smart contracts include common execution codes and trusted Execute the code, the ordinary execution code in the smart contract is executed by the smart contract virtual machine, the trusted execution code is loaded in the trusted execution environment to complete the execution, and the trusted execution environment deploys a trusted stub program and its matching signature private key , the security of the stub program is guaranteed by the remote authentication mechanism. The stub program loads the trusted execution code in the smart contract and completes its integrity check, and signs the execution result and code integrity; it includes the following four main links:
[0033] S1. Pile program loading ...
comparative approach 1
[0047] Intelligent contract operation method, device, equipment and storage medium-----CN202010683529.3
[0048]The comparative invention is based on the target transaction request initiated by the target smart contract, the target transaction request includes the target contract method to be called in the target smart contract, and the target transaction request is processed in the trusted execution environment by invoking the target contract method based on the shared link library. In the comparative invention, the smart smart contract is compiled in a trusted execution environment, and a shared link library linked with a trusted execution environment is generated. In the present invention, the smart contract logic on the chain will be split, and the trusted part of the contract will be executed through the stub program. Therefore, the implementation methods adopted are different.
comparative approach 2
[0050] Internet of Things access control method with privacy protection based on blockchain -----CN202010461829.7
[0051] The comparative invention uses a zero-knowledge proof algorithm to encrypt transactions, generate proofs, and utilize a trusted execution environment to ensure the security of smart contracts and related data. The present invention does not use unconventional encryption schemes such as zero-knowledge proof, and through the splitting of smart contracts, the privacy-related business logic is executed in the security domain of the trusted execution environment, which has better versatility.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com