Privacy protection-based authentication method, apparatus and device
A privacy protection and authentication method technology, applied to devices and equipment, in the field of privacy protection-based authentication methods, which can solve problems such as information leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
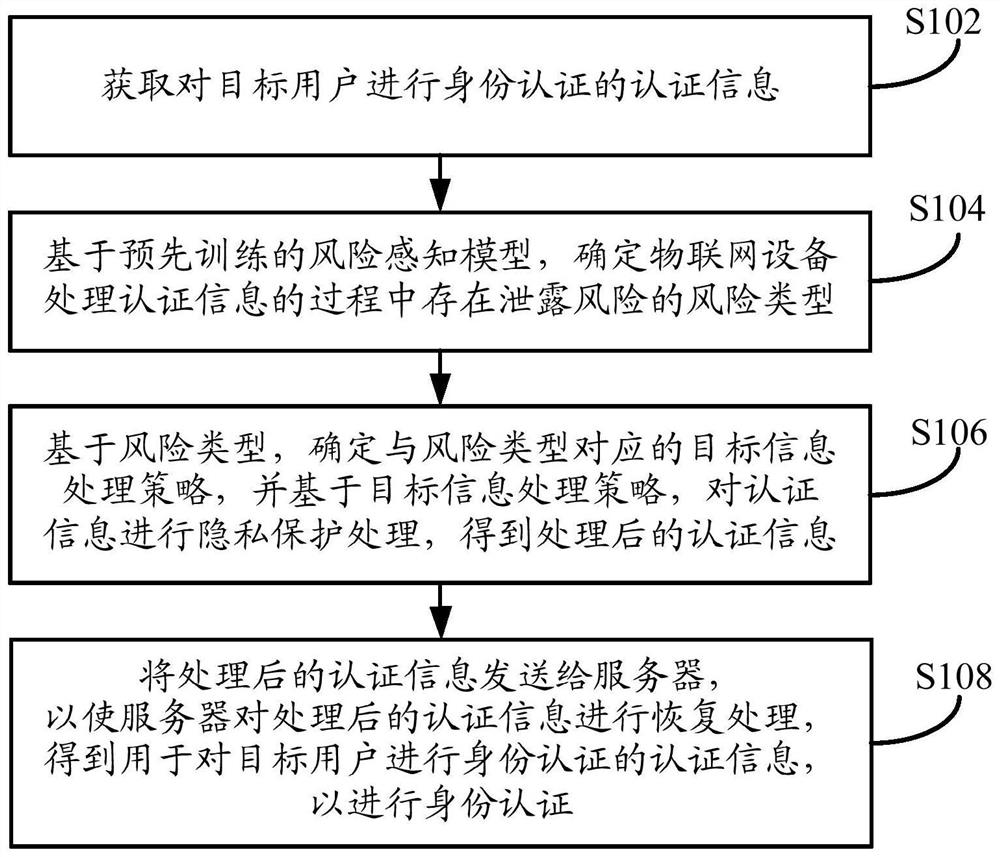
[0027] Such as figure 1 As shown, the embodiment of this specification provides an authentication method based on privacy protection. The execution subject of the method may be an Internet of Things (The Internet of Things, IoT) device, and the Internet of Things device may be any object configured with a biometric system. A networked device, such as an Internet of Things device, can be an automatic vending device equipped with an image acquisition device, or an access control device equipped with a fingerprint acquisition device, etc. The method specifically may include the following steps:
[0028] In S102, the authentication information for authenticating the identity of the target user is acquired.
[0029] Among them, the target user can be any one or more users who use the IoT device to perform specified operations (such as payment operations, start operations, etc.), and the authentication information can include the biometric information of the target user. For exampl...
Embodiment 2
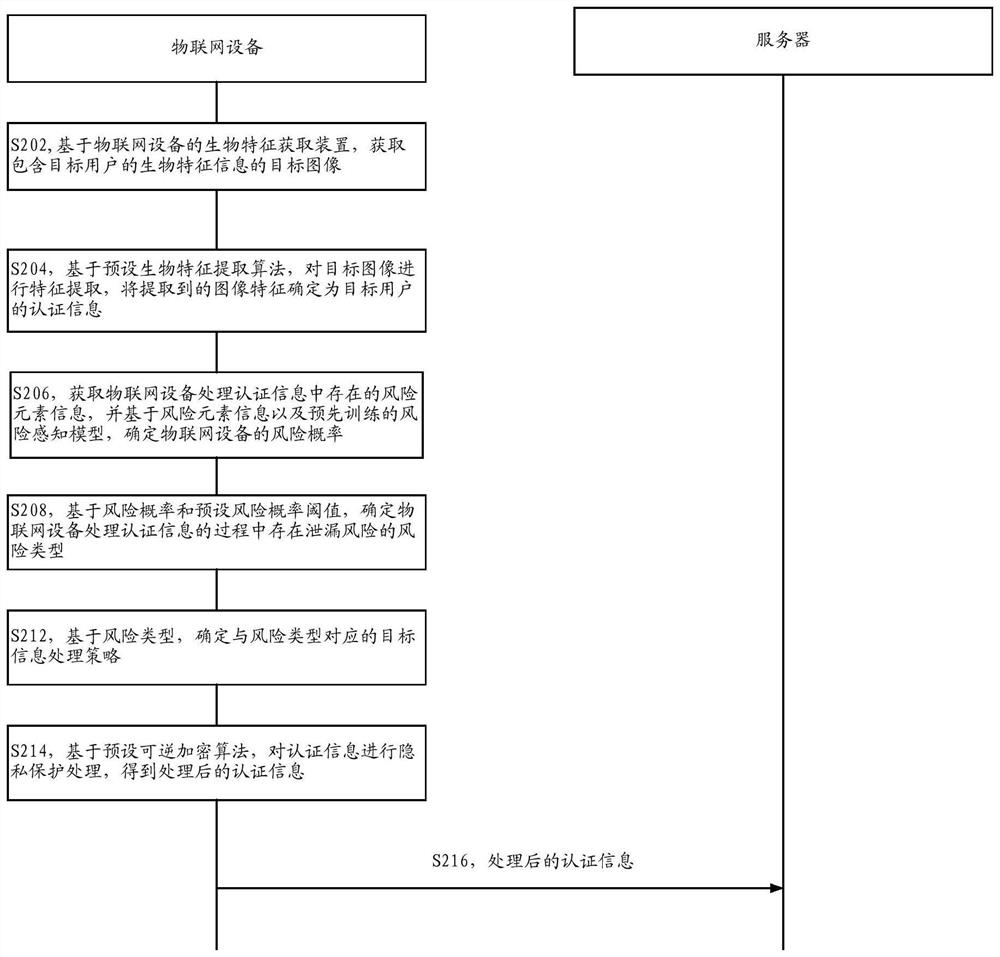
[0049] As shown in Figure 2, the embodiment of this specification provides an authentication method based on privacy protection, the execution subject of the method may be an Internet of Things (The Internet of Things, IOT) device, and the Internet of Things device may be configured with a biometric identification system Any Internet of Things device, such as an Internet of Things device can be a vending device equipped with an image acquisition device, or an access control device equipped with a fingerprint acquisition device. The method specifically may include the following steps:
[0050] In S202, based on the biological feature acquisition device of the Internet of Things device, the target image including the target user's biological feature information is acquired.
[0051] Wherein, the target image may include an image of one or more biological feature information such as the target user's face, iris, and fingerprint.
[0052] In S204, feature extraction is performed ...
Embodiment 3
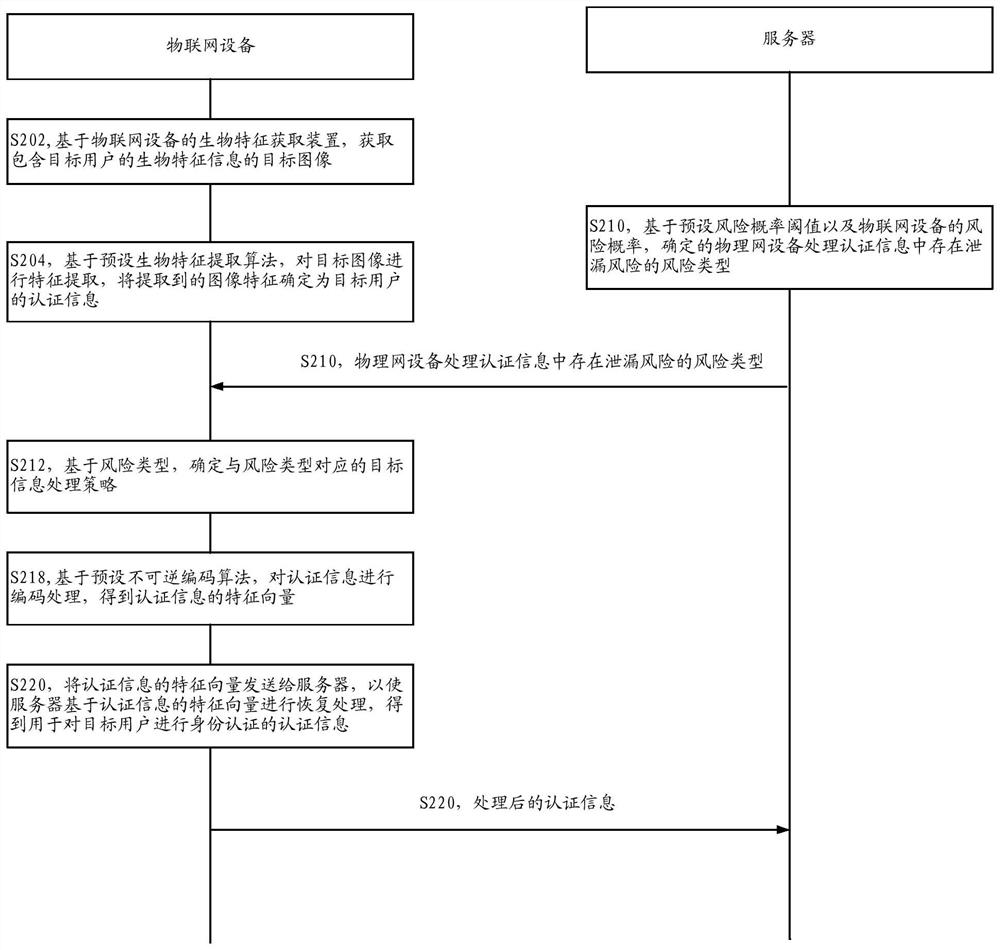
[0083] Such as image 3 As shown, the embodiment of this specification provides an authentication method based on privacy protection. The method may be a server, and the server may be an independent server or a server cluster composed of multiple servers. The method specifically may include the following steps:
[0084] In S302, the target authentication information of the target user sent by the IoT device is acquired.
[0085] Wherein, the target authentication information may be the information obtained by the Internet of Things device based on the target information processing strategy for the privacy protection processing of the target user's authentication information, and the target information processing strategy may be an information processing strategy corresponding to the risk type of the IoT device. The risk type of the Internet-connected device can be a risk type based on a pre-trained risk perception model, which determines that there is a risk of leakage in the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com