Trusted startup method for BMC firmware system security
A technology of system security and file system, applied in the field of trusted startup oriented to BMC firmware system security, can solve problems such as difficult application, lack of trusted password module, and reliability cannot be guaranteed, and achieve the effect of cost saving
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The trusted startup scheme of BMC firmware system among the present invention relates to three processes:
[0038] Process 1: System Construction Initialization Process
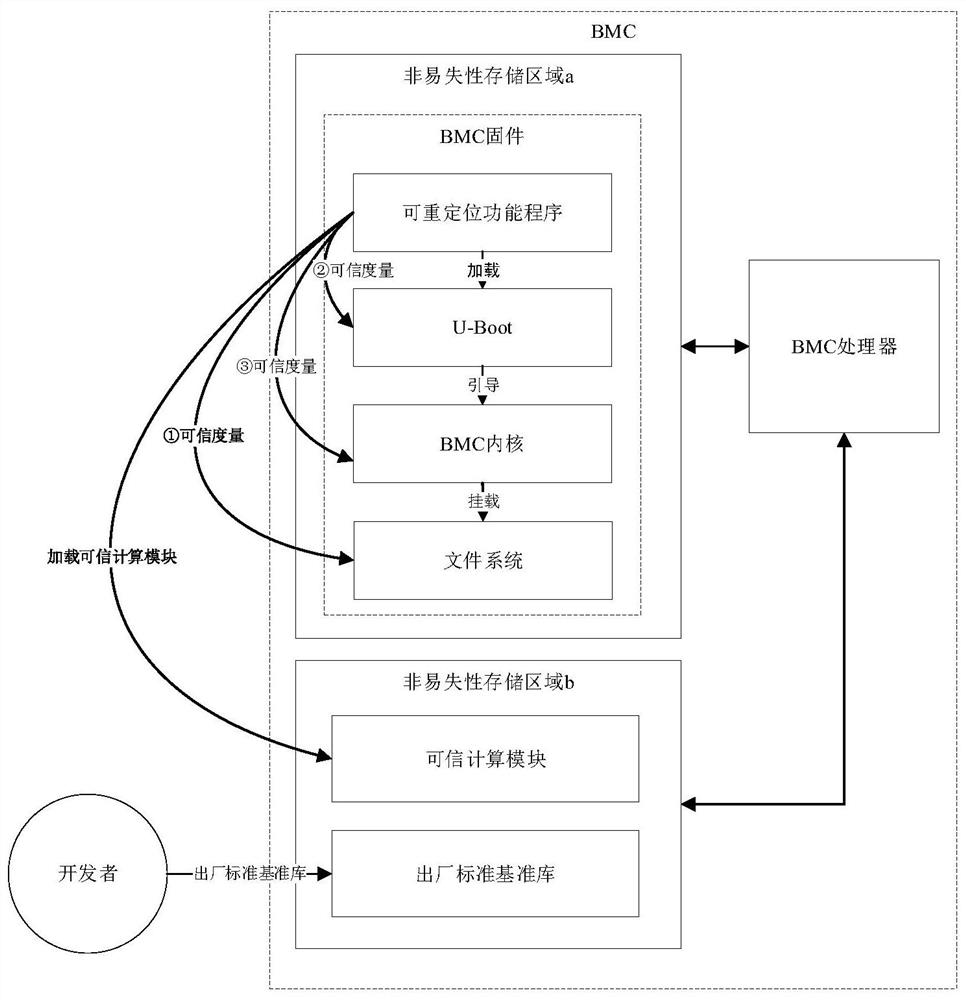
[0039] The initialization process of this system mainly involves two objects: BMC manufacturer and BMC. The BMC needs to have a BMC processor, a non-volatile storage area a for storing BMC firmware, and a non-volatile storage area b for storing trusted computing modules and factory standard reference libraries.
[0040] Step 1: BMC manufacturers add a relocatable function program before U-Boot in the BMC development stage, responsible for loading trusted computing modules and measuring the integrity of each boot module;
[0041] Step 2: BMC manufacturers initialize the BMC firmware into non-volatile storage area a, and the trusted computing module and factory standard reference library are initialized into non-volatile storage area b during the BMC delivery stage.
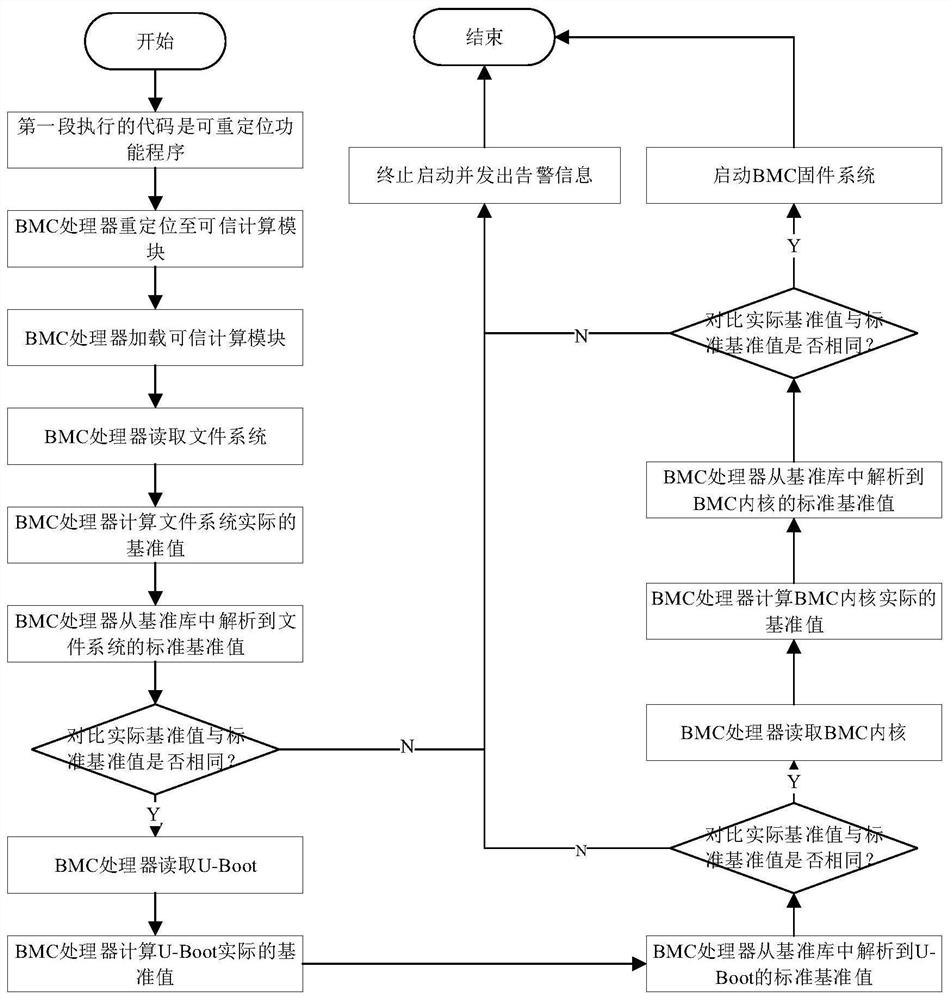
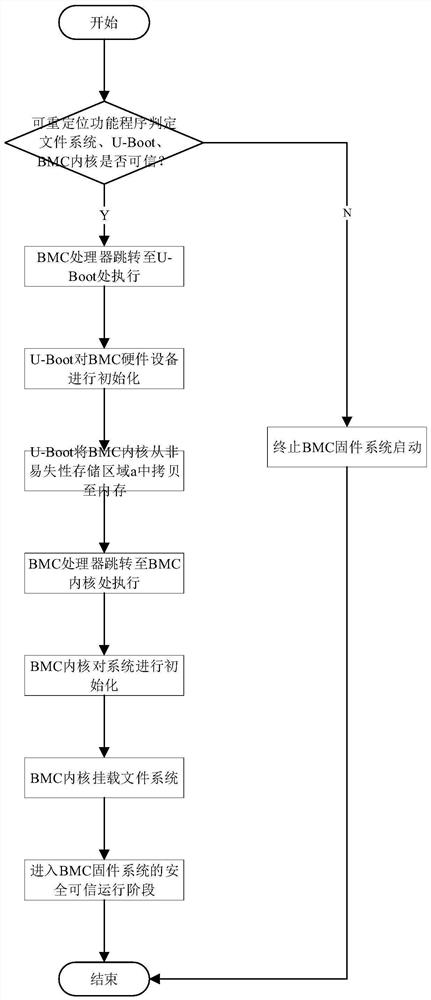
[0042] Process 2: BMC firmware sys...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com