Anti-attack detection method and system based on network node topological structure
A topology and attack detection technology, applied in character and pattern recognition, instrument, platform integrity maintenance, etc., can solve problems such as low practicability and poor universality, and achieve wide detection range, high detection accuracy, more realized effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0061] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings.
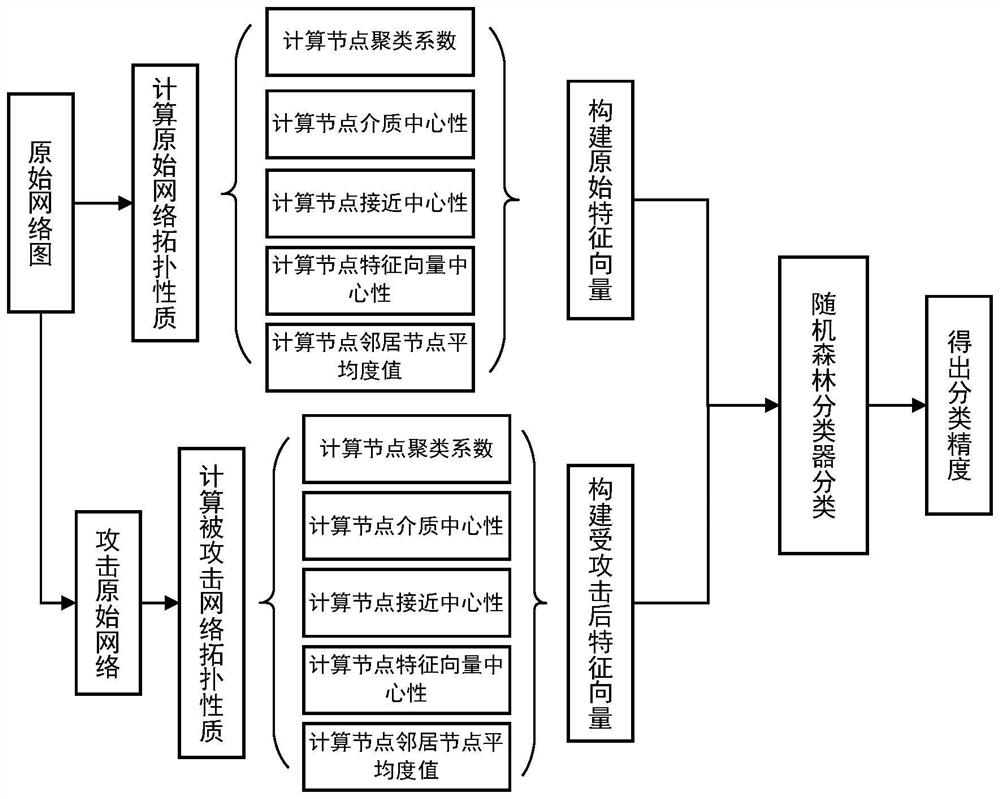
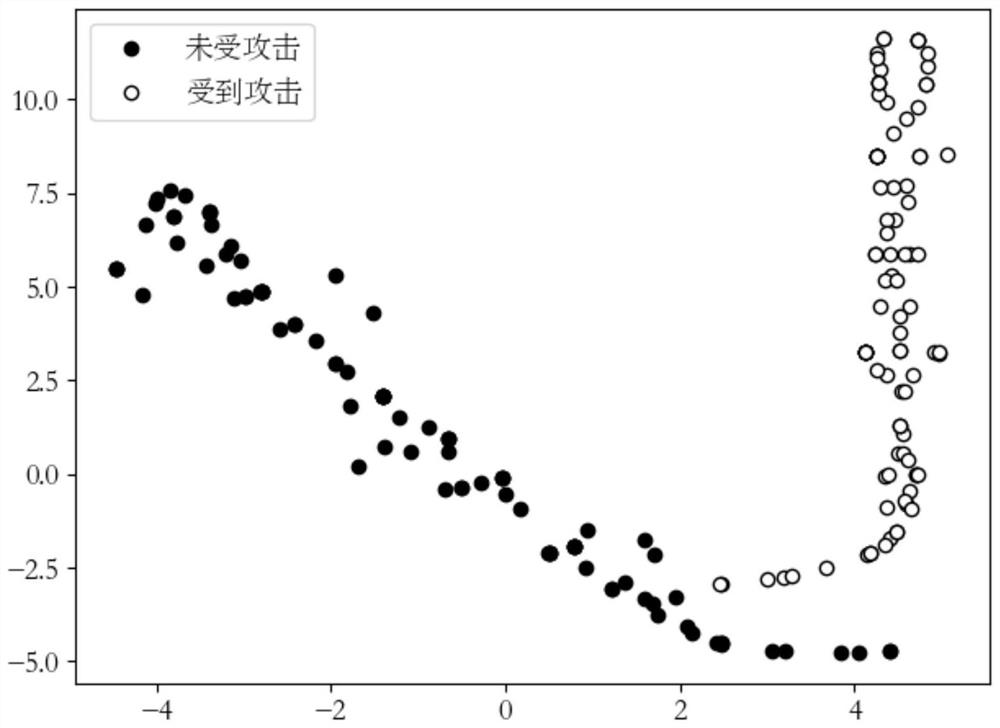
[0062] refer to figure 1 , an adversarial attack detection method based on the topology of network nodes. The present invention takes the incremental attack method Nettack as an example, wherein the object to be attacked is the node classification task of the GCN model in the Cora citation network.
[0063] The present invention is divided into following several steps:
[0064] S1: Import network G=(V, E), where V represents the set of nodes in the network, and E represents the set of edges in the network. In this example we import a Cora citation network. There are 2708 nodes and 5429 links in the Cora network, each of which represents a paper, and if there is a citation relationship between two papers, it is considered that there is a link between them. We randomly select several nodes as the objects to be attacked....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com