False face video tampering detection method and system based on time domain self-attention mechanism
A tampering detection and attention technology, applied in the field of fake face video tampering detection, can solve the problems of decreased accuracy, insufficient generalization ability, and no use of the timing information of the frames before and after the fake face video, and achieves high accuracy and good The effect of versatility and good compatibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
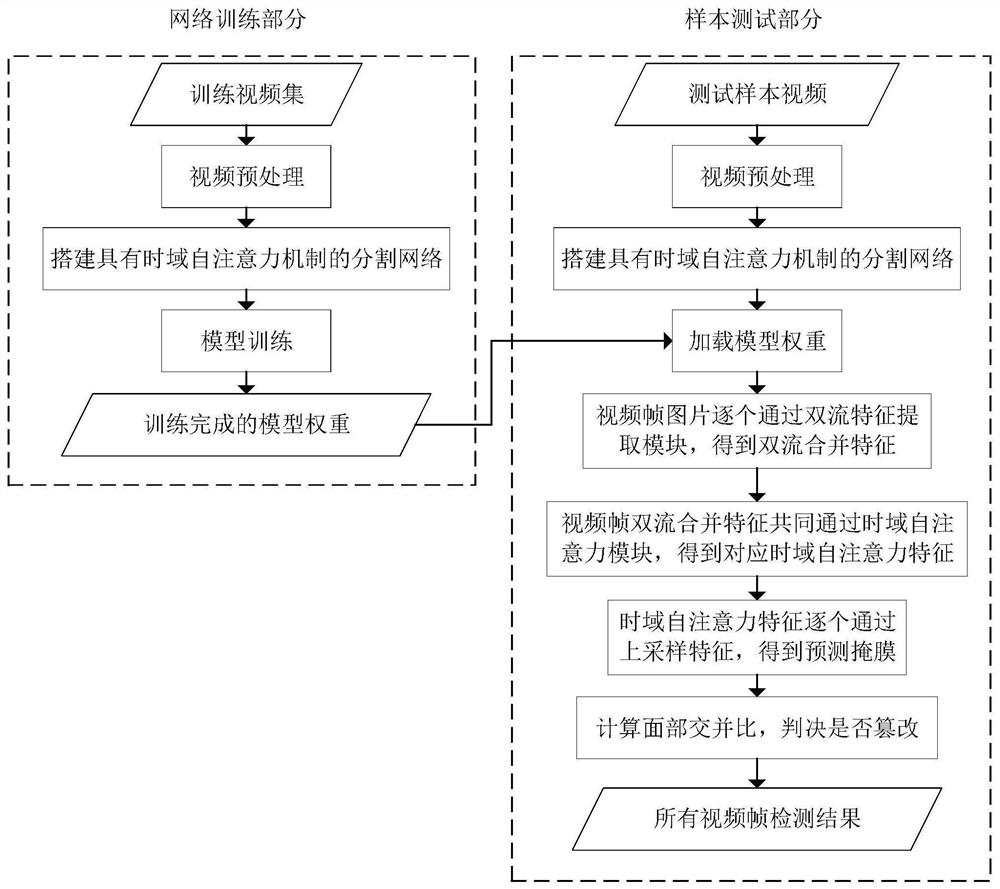
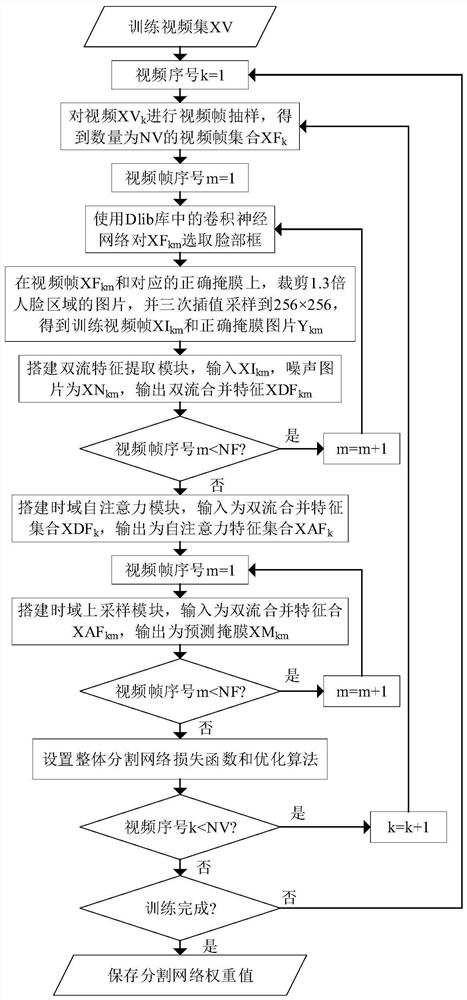
[0100] Such as figure 1 As shown, this embodiment provides a fake face video tampering detection method based on the time-domain self-attention mechanism. The dual-stream feature extraction module is used to extract the color features and noise features of the image space domain and then merge them, and then use the time-domain self-attention module. After extracting the time domain information of the front and back frames, and accurately predicting the tampered area, the facial intersection ratio under the calculation trust mechanism of the predicted tampered area is used to judge the true and false faces, including the network training part and the sample test part;
[0101] This embodiment takes training on the FaceForensics++ (FF++) (C0&C23) database, in-database testing on the FF++ (C0&C23) database, and cross-database testing on the TIMIT database as examples, and introduces the implementation process of this example in detail. The experiment is carried out on the Ubuntu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com