Method for Realizing User Data Security Migration Based on Voice Channel
A technology of user data and voice channel, which is applied in the direction of public key for secure communication, secure communication device, user identity/authority verification, etc., can solve the problems of long-distance transmission, unusable security, and extremely high security requirements, and achieve Occupies less resources, improves security, and reduces the effect of deciphering
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] In order to express the present invention more clearly, the present invention will be further described below in conjunction with the accompanying drawings and embodiments.
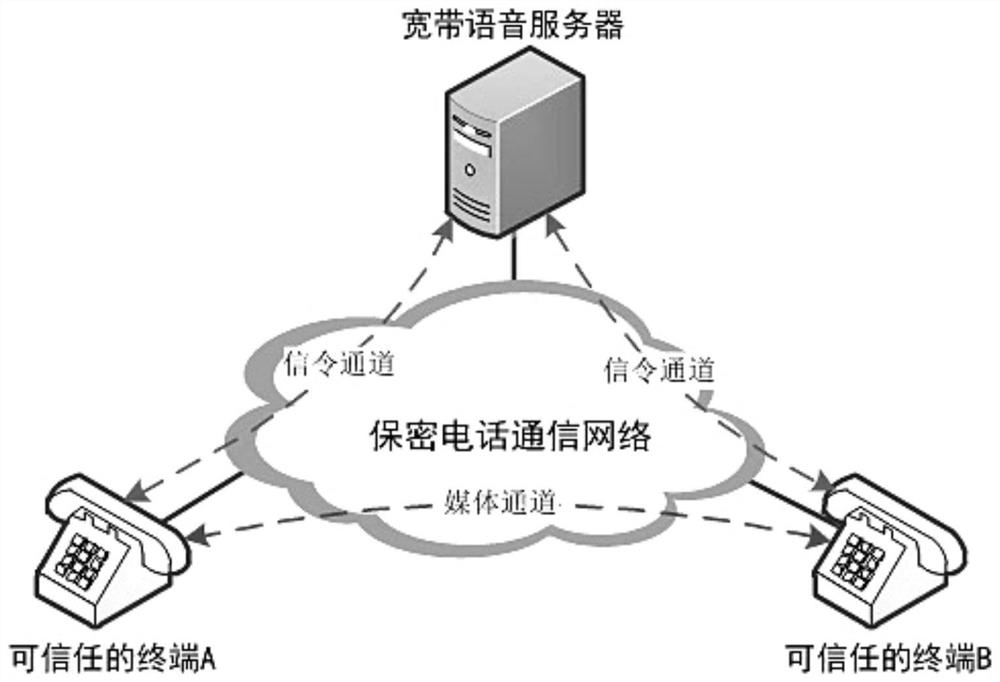
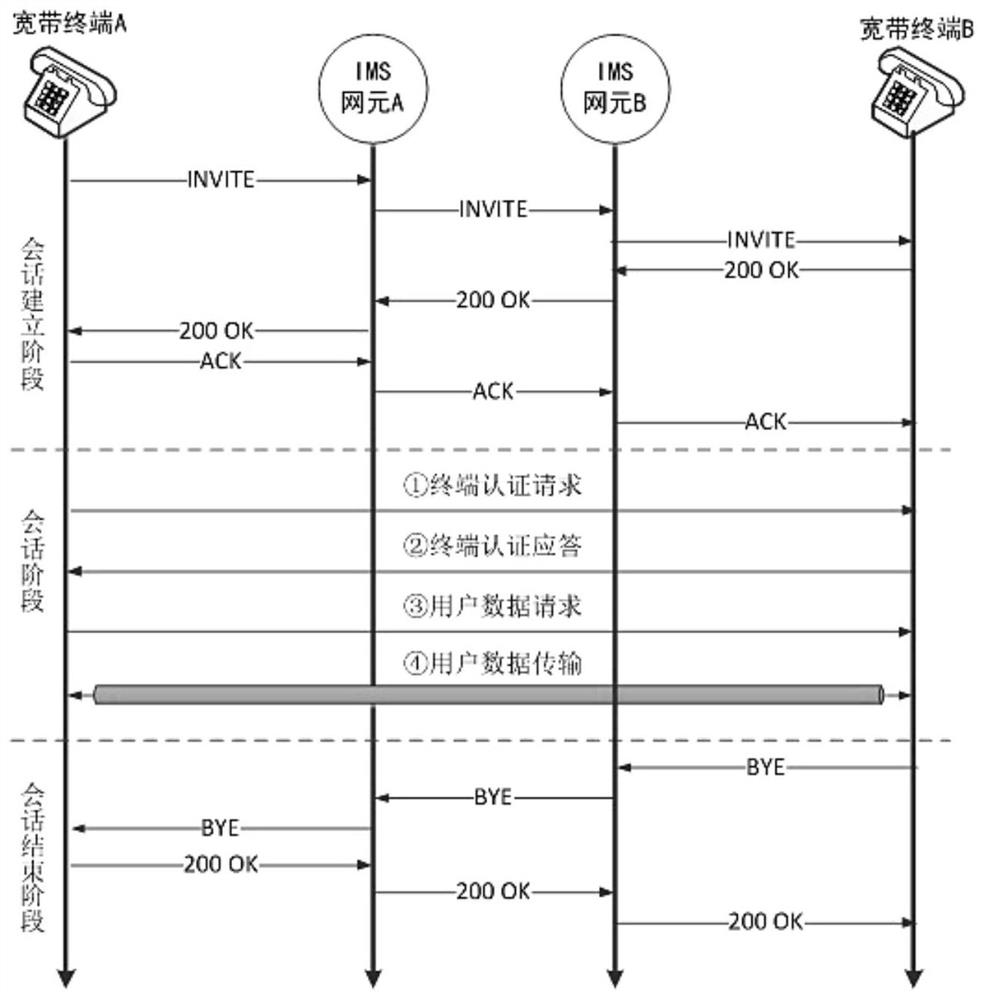
[0042] see Figure 1 to Figure 3 A method for implementing secure migration of user data based on a voice channel is applied to data transfer between two device terminals, including a request terminal, a transfer terminal and a broadband voice server, and includes the following steps:
[0043] Establish a connection: the requesting terminal and the transfer terminal use the signaling channel with the broadband voice server to establish a call connection;
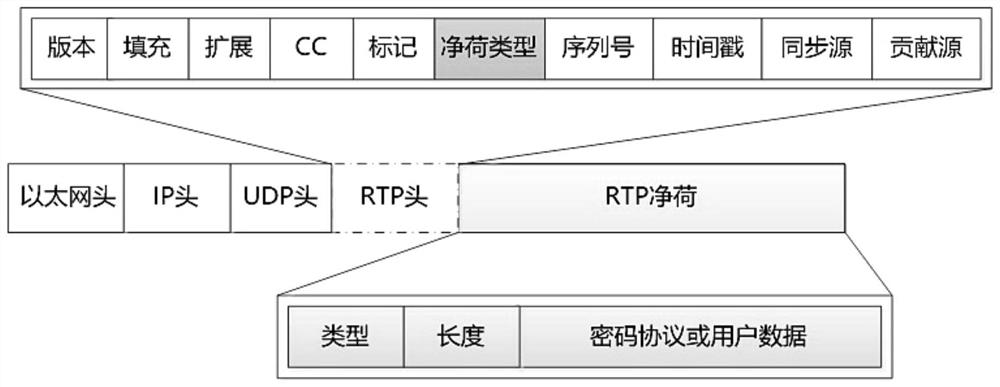
[0044]Identity authentication request and verification: the requesting terminal uses the media channel in the call connection to send an identity authentication request to the transfer terminal, and the transfer terminal verifies the identity authentication request to realize the identity authentication and authentication of both parties;
[004...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com