A radio signal forgery method for combating deep learning
A technology of radio signal and deep learning, applied in neural learning methods, interference to communication, secure communication, etc., can solve problems such as easy detection, large visual difference of fake signal signal, inability to directly transfer signal field, etc., to reduce accuracy Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
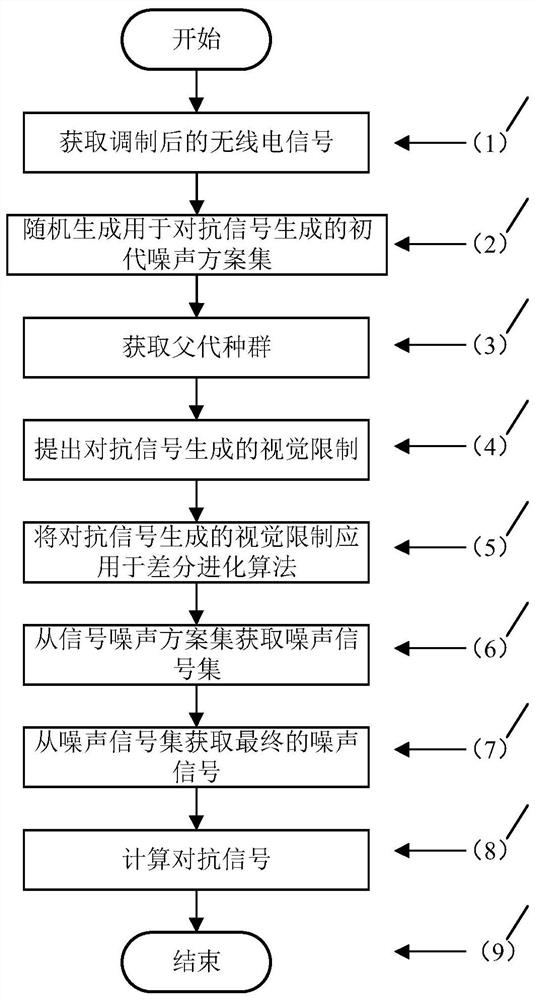
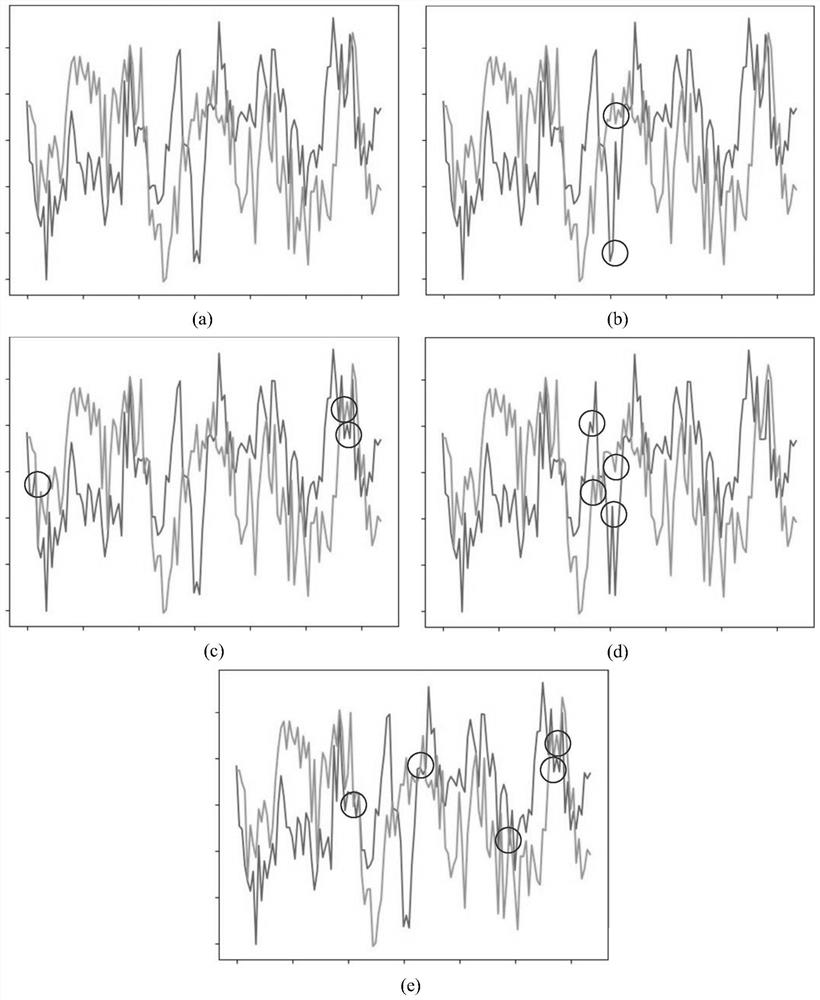
[0028] In electronic countermeasures, with the continuous improvement of the accuracy of the signal classifier based on deep learning, the classification accuracy of the radio signal modulation method by the enemy is getting higher and higher, and the communication security is threatened, and the existing data forgery methods against deep learning , mainly used to counter the image classifier in the field of computer vision. When it is used for forging signals, there will be a significant visual difference between the forged signal and the original radio signal. The enemy can recognize the existence of the forged signal with the naked eye, which reduces the deception of the forged signal. properties, therefore, cannot be directly transferred for adversarial radio signal classifiers. From the perspective of eliminating the visual difference between the forged signal and the original radio signal, the present invention studies a radio signal forgery method for combating deep lear...
Embodiment 2
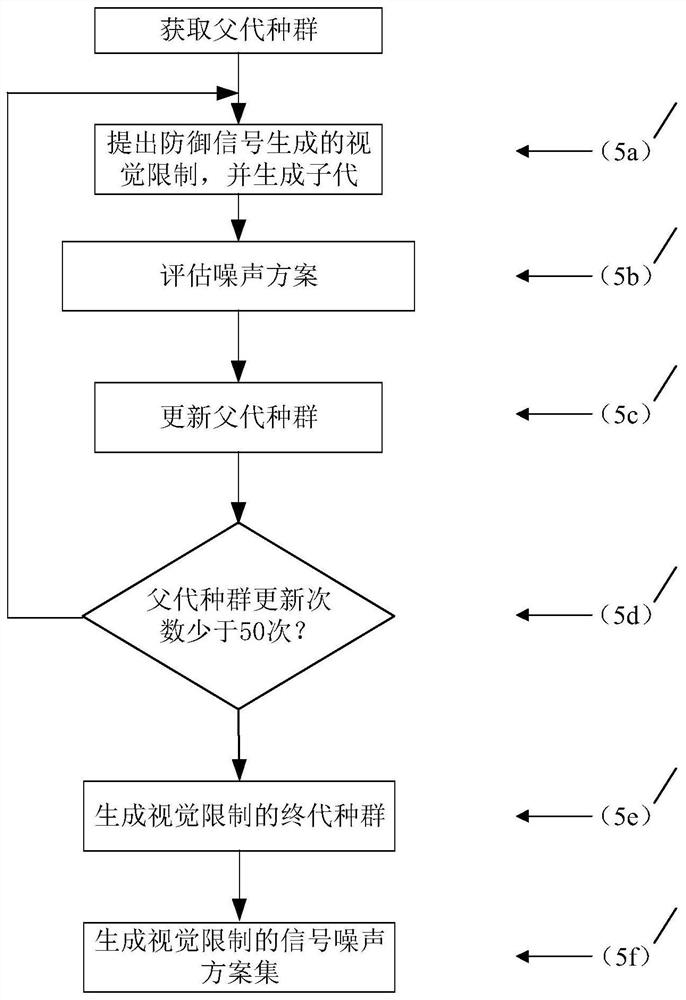
[0054]The overall technical scheme of the radio signal forgery method for combating deep learning is the same as that of Embodiment 1. The visual restriction of the countermeasure signal generation described in step (5) is applied to the differential evolution algorithm, and the signal noise scheme set N' is obtained. The visual constraints of adversarial signal generation, and the visual constraints are used in the differential evolution algorithm, by adopting a deep learning-based signal classifier M to evaluate the noise scheme, and finally generate a final generation population T' representing the set of signal-noise schemes, see figure 2 , the specific implementation steps are:
[0055] (5a) Generating offspring populations with visual constraints Applying the proposed visual constraints of adversarial signal generation to a differential evolution algorithm to generate offspring populations Generate the daughter population of the differential evolution algorithm for t...
Embodiment 3
[0071] The overall technical scheme of the radio signal forgery method for combating deep learning is the same as that in Embodiment 1-2. The evaluation noise scheme described in step (5b) is to use a deep learning-based signal classifier M to calculate T and The evaluation score of the medium noise scheme, the implementation steps include:
[0072] (5b1) Convert the interference scheme into candidate adversarial signals: convert the current parent population T and the offspring population The jamming scheme in is transformed into a candidate adversarial signal set X'=[x 1 ',...,x k ',...,x 800 '], where 1≤k≤800, is the kth candidate adversarial signal, The conversion rules are:
[0073]
[0074]
[0075] (5b2) Obtaining the evaluation score: Input each candidate adversarial signal in the candidate fake signal set into the deep learning-based signal classifier M to be confronted, as the evaluation score of the corresponding interference scheme:
[0076] Score ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com