Wireless sensor network system and method based on CPK
A wireless sensor and network technology, applied in the field of sensor networks, can solve the problems of instability, denial of service attacks, communication protocols are vulnerable to various attacks, etc., to improve stability and reliability, ensure reliability, and ensure security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
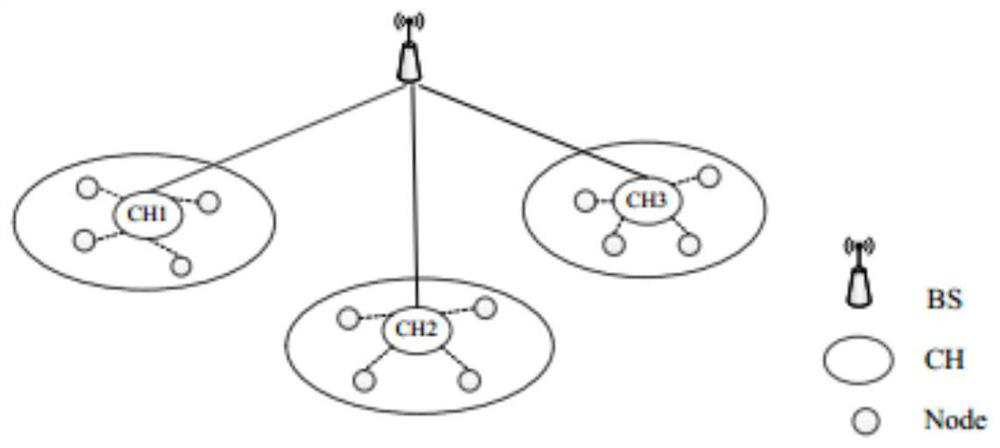
[0092] Such as figure 1 As shown, the CPK-based wireless sensor network system in this embodiment is mainly composed of three types of equipment: base station, cluster head node, and intra-cluster node. The main function of the base station BS (Bass Station) is to manage the entire wireless sensor network, including identification management, public and private key management, data summary processing and sending to observers, etc. The cluster head node CH (ClusterHead) is equivalent to a router, and its main function is to realize message reception, processing, forwarding between nodes in the sensor network, and direct communication with the base station. Sensor node (Node) is the largest type of equipment in the network. It undertakes different tasks according to the functions of its sensors, and collects, processes, and sends relevant data of sensing objects cooperatively and autonomously.
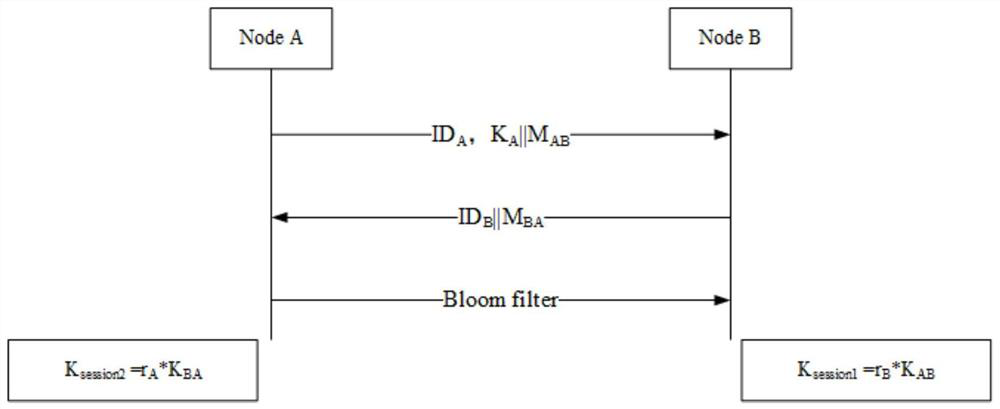
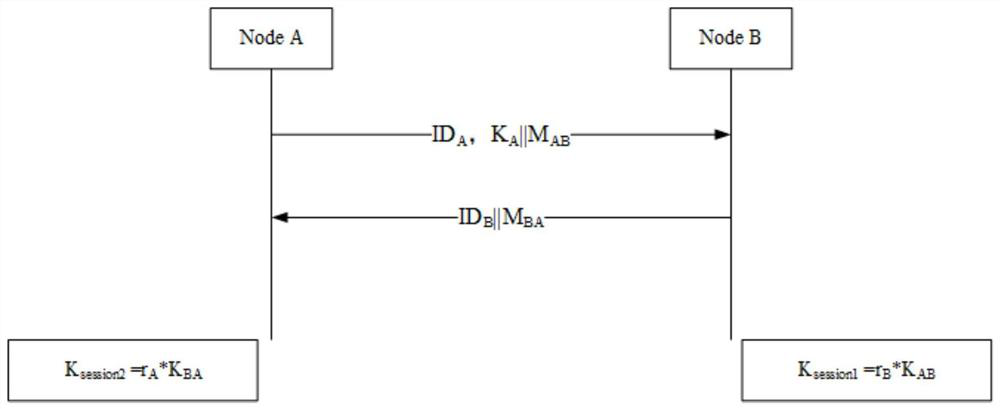
[0093] The CPK-based wireless sensor network method disclosed in this embodiment in...
Embodiment 2
[0199] The difference between this embodiment and Embodiment 1 is that, in this embodiment, the clustering step and the intra-cluster communication step also include a node position detection step before performing node identity verification, and detect nodes to be verified through nodes in the cluster that have passed the authentication According to the signal strength information, the position of the node to be verified is calculated according to the signal strength information, and compared with the position of the node in the historical record, it is judged whether the position of the node to be verified has changed. If so, the verification fails and the connection is terminated. If so, the verification passes , to proceed with node authentication.
[0200] In this embodiment, the signal strength of the node to be verified is detected through the authenticated nodes in the cluster, and the location is detected and verified based on the signal strength. In this embodiment, s...
Embodiment 3
[0202] The difference between this embodiment and Embodiment 2 is that in this embodiment, if it is detected that the position of the node to be verified has changed, the server is requested to determine whether there is a maintenance change record, if so, the verification is passed, and the node identity verification is continued, otherwise, the connection is terminated .
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com