Data stealing identification system applied to wireless local area network and use method thereof
A wireless local area network and identification system technology, applied in the field of data security design, can solve the problems of inability to effectively detect ARP spoofing, and the detection terminal cannot obtain spoofing information, etc., to achieve the effect of improving network security, convenient application, and improving service life.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
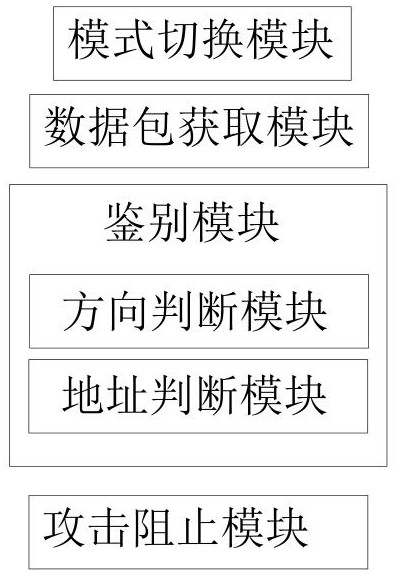
[0038] Example 1, such as figure 1 As shown, the data theft identification system applied in the wireless local area network and its application method. Wireless AP (Access Point) is a very broad name. It can also be called a wireless access node, a session point or an access bridge. It not only includes a simple wireless access point, but also a wireless router or a wireless gateway. A general term for devices such as wireless bridges. In this example, the following and figure 1 Each module mentioned in , exists in the form of software, specifically, it can be code written in C language, and exists in the driver program of the wireless AP.
[0039] First, the wireless AP exists in a certain wireless network, enter S01, the mode switching step. At this time, the mode switching module sets the wireless AP to a promiscuous mode. Promiscuous mode is a network configuration mode of wireless AP. In this mode, wireless AP monitors all network data packets in the network, but doe...
Embodiment 2
[0053] Embodiment 2, different from Embodiment 1, in step S05, in addition to disconnecting the attacker, the attack prevention module will also send an update ARP cache command to each terminal in the network in the form of broadcast, so that each terminal clears the The attacker's address information in the ARP cache, and update the group temporary key GTK in the network. Updating GTK further increases the technical difficulty for attackers to try to use other technical means in the future.
[0054] Based on the above technical solution, firstly, limited identification and detection can be performed on data spoofing in the wireless local area network, especially ARP data spoofing. Secondly, the main body of the detection is the wireless AP itself, no need to add an additional independent network terminal, and the application is convenient. Third, this type of identification can effectively identify whether ARP spoofing is broadcast mode or point-to-point transmission mode, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com