Crowd portrait storage and orientation system and method under big data high concurrency
A directional system and big data technology, applied in database indexing, database updating, structured data retrieval, etc., can solve problems such as inability to make full use of multi-core servers, inability to retain historical data, main server service interruption, etc., and achieve flexible loading and release. memory space, achieve fast and accurate, application reduction effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
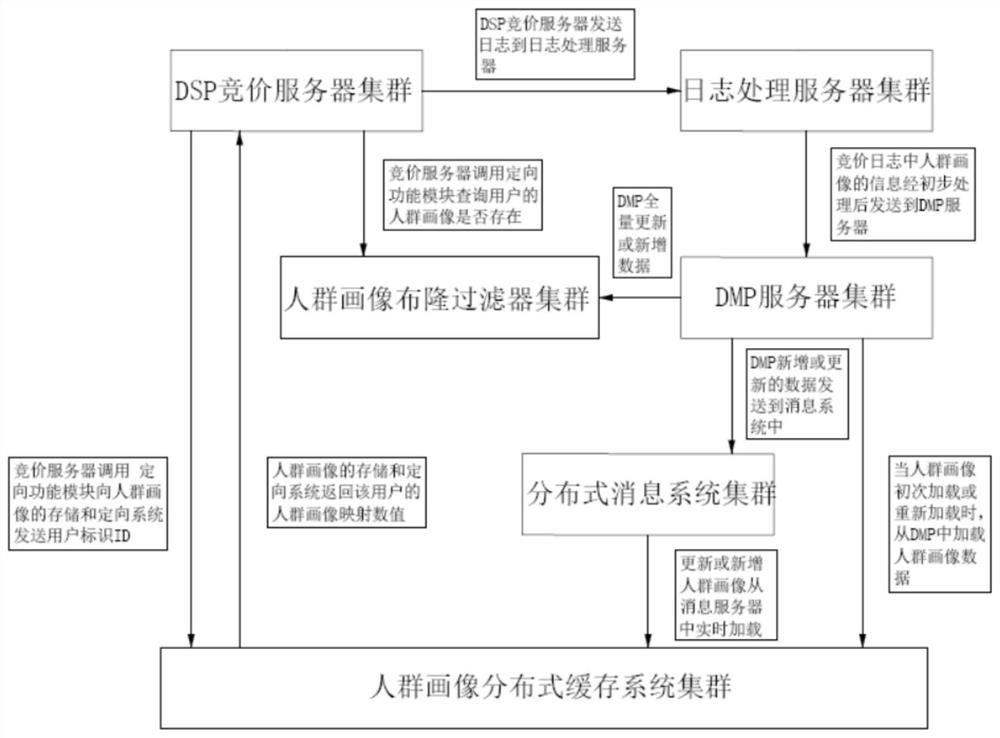
[0025] like figure 1 As shown, the crowd portrait storage and orientation system under high concurrency of big data, the output end of the crowd portrait storage and orientation system is connected to the DSP bidding server, and the input end is respectively connected to the DSP bidding server, the distributed message system server and the DMP server. The storage and orientation system includes a crowd portrait cache system, a reading system, a compression writing system, and a message processing management system.
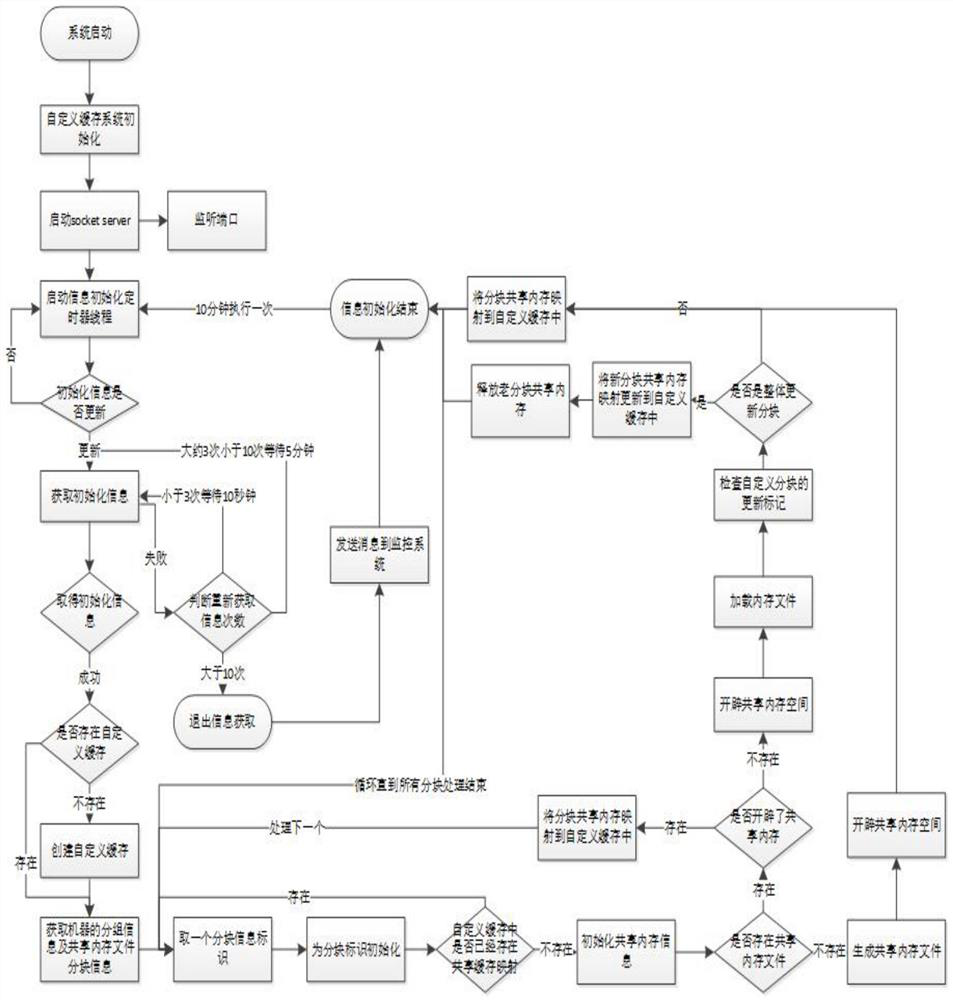
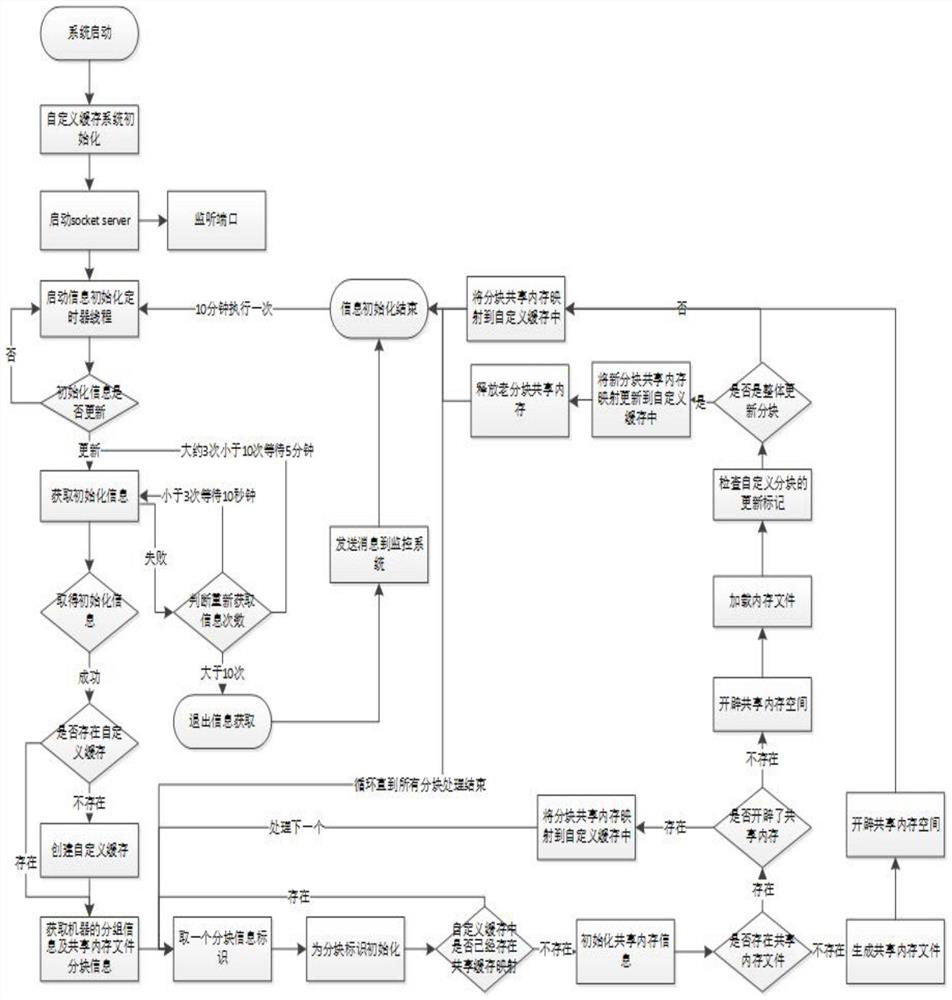
[0026] The method of crowd portrait storage and orientation under the high concurrency of big data, through the segmentation of the crowd portrait data, block identification formed by block calculation, load or create shared memory files, create file-based shared memory, and generate custom cache , to map the shared memory into the cache. The self-defined cache starts timer automatic management, checks the update status by blocks at regular intervals, if the upda...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com