Data authority control module, data access system and data access method
A data access and data authority technology, applied in digital data protection, electronic digital data processing, instruments, etc., can solve the problem that data authority cannot provide unified management, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0043] The invention provides a data authority control module, which is configured at the data access request receiving place of the data entry system. The data entry system is used to provide a unified interface for the database and the application system, and the data access request includes tokens, user information and data access statements .
[0044] The data authority control module includes a rule configuration module, a token verification module, an authority assembly module, and an interface module. The rule configuration module interacts with operation and maintenance users through the rule configuration interface to support operation and maintenance users to configure authority rules and obtain authority configuration information; The token verification module is used to verify the authenticity of the token; the permission assembly module is used to assemble the permission control statement according to the permission configuration information and user information, o...
Embodiment 2
[0073] The data access system of the present invention includes a database, an application system, and a data entry system that provides a unified interface for the database and the application system. The data access request receiving part of the data entry system is configured with a data authority control module as disclosed in Embodiment 1, and the data authority The configuration module is used to support operation and maintenance users to configure permission rules and obtain permission configuration information; it is used to verify the authenticity of tokens, to assemble permission control statements according to permission configuration information and user information, to obtain initial permission assembly access statements, and to use Assemble the access control statement according to the data access statement and the corresponding initial permission assembly access statement to obtain the final permission assembly access statement; it is used to submit the final perm...
Embodiment 3
[0075] A data access method of the present invention, through the data access control module disclosed in embodiment 1, realizes the access control of data between the application system and the database, and the method includes the following steps:
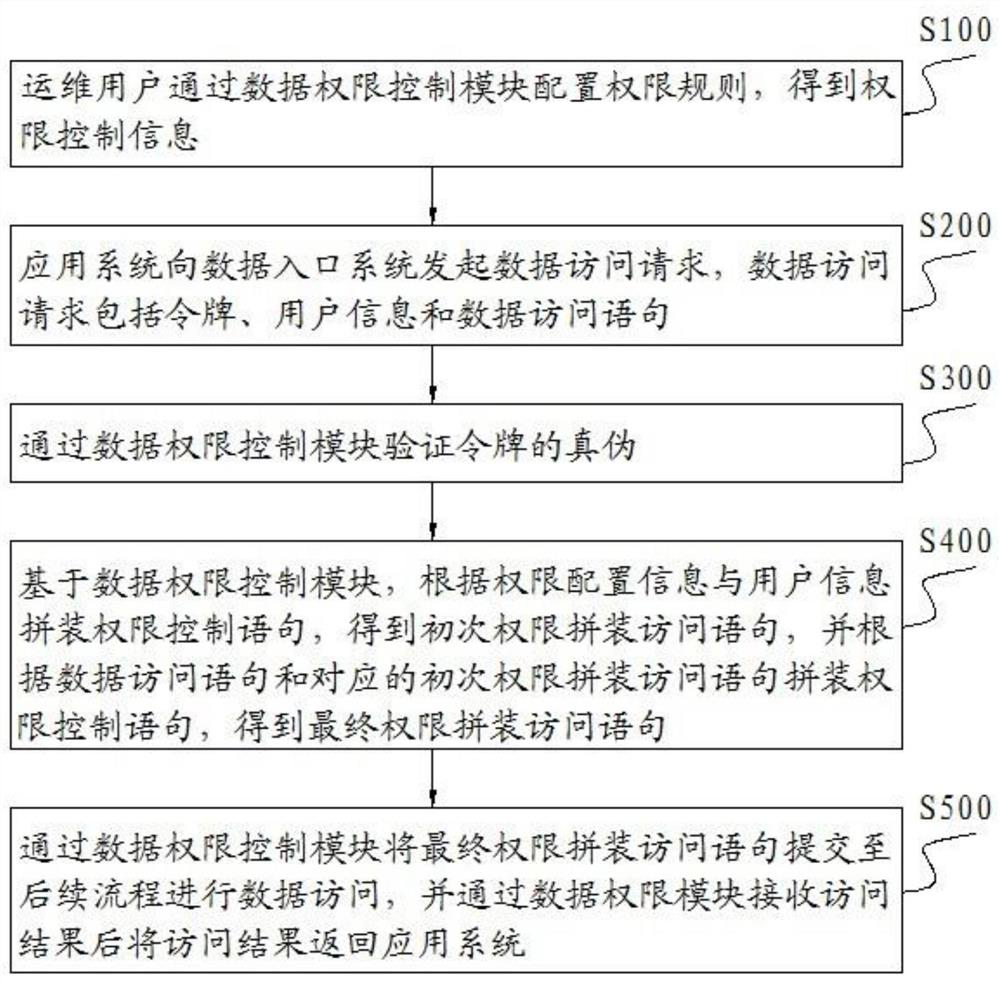
[0076] S100. The operation and maintenance user configures permission rules through the data permission control module to obtain permission control information;
[0077] S200. The application system initiates a data access request to the data entry system, where the data access request includes a token, user information, and a data access statement;
[0078] S300. Verify the authenticity of the token through the data authority control module;
[0079] S400. Based on the data authority control module, assemble the authority control statement according to the authority configuration information and user information, obtain the initial authority assembled access statement, and assemble the access statement according to the data acce...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com