Sending mail encryption method based on quantum security key
A technology for sending emails and security keys, applied in the field of email sending based on quantum keys, can solve problems such as increasing labor costs, and achieve the effects of enhancing security, improving network security capabilities, and reducing transformation costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0089] Embodiment 1 An encryption method for sending mail based on quantum security keys, which is applied to mail sending equipment
[0090] This embodiment discloses an encryption method for sending mail based on a quantum security key, which is applied to a mail sending device.
[0091] The mail sending device is used for sending mail, and has a built-in or external quantum security chip.
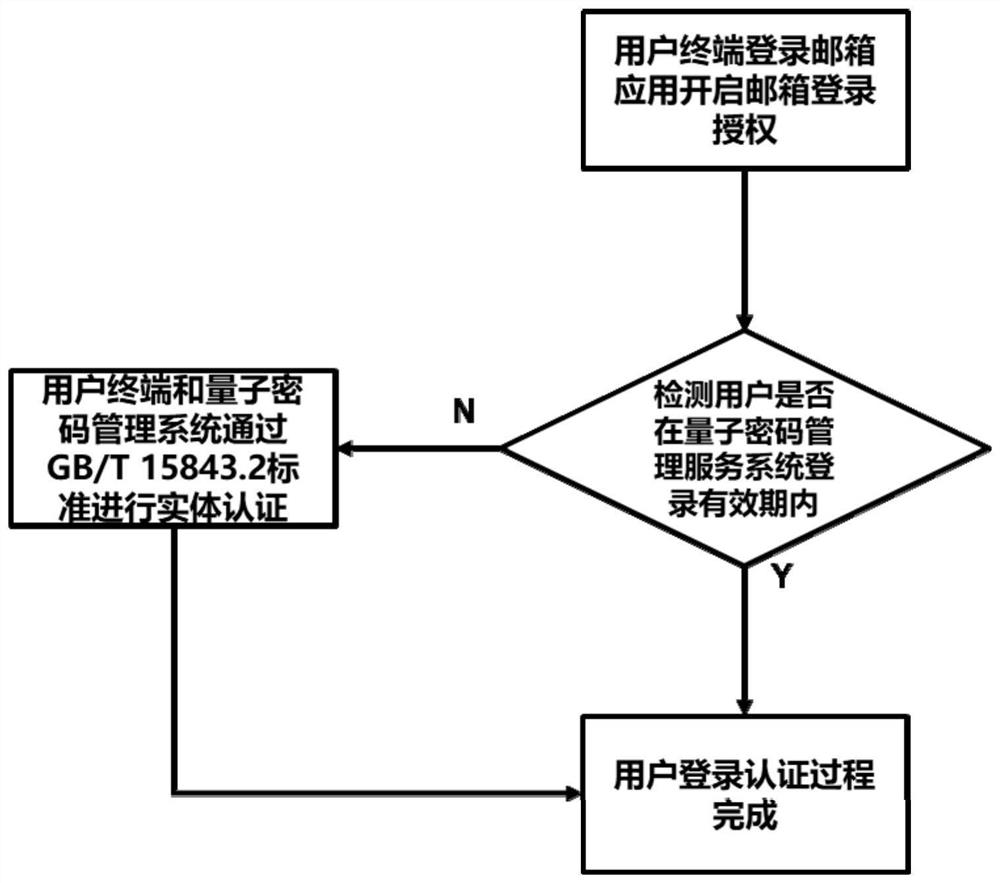
[0092] The quantum security chip stores the quantum security key. The security key in the quantum security chip undergoes symmetric entity authentication through the network and the quantum password management service system. The quantum security chip can be in the form of a SIM card or a U disk. The security in the quantum security chip The key is pre-built, and the quantum security chip is filled in advance through the quantum key filling machine when the card is issued. The quantum security chip used has a preset quantum cryptography, that is, the principle is: the quantum security ch...
Embodiment 2
[0125] Embodiment 2 Mail transmission method based on quantum security key
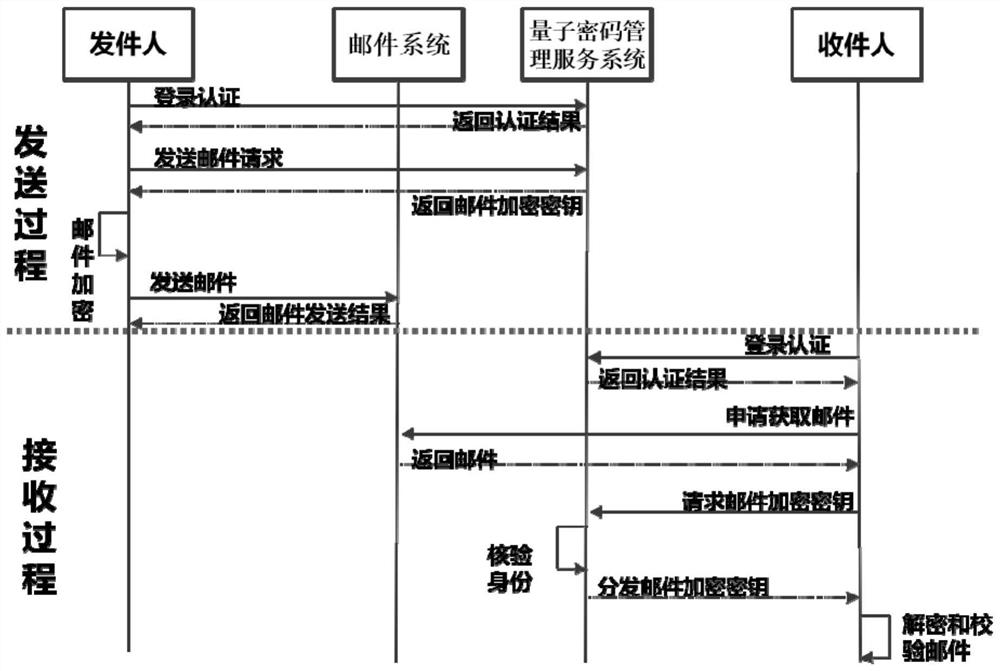
[0126] This embodiment is an email sending and receiving method using the encryption method for sending emails in Embodiment 1, including sending and receiving processes.
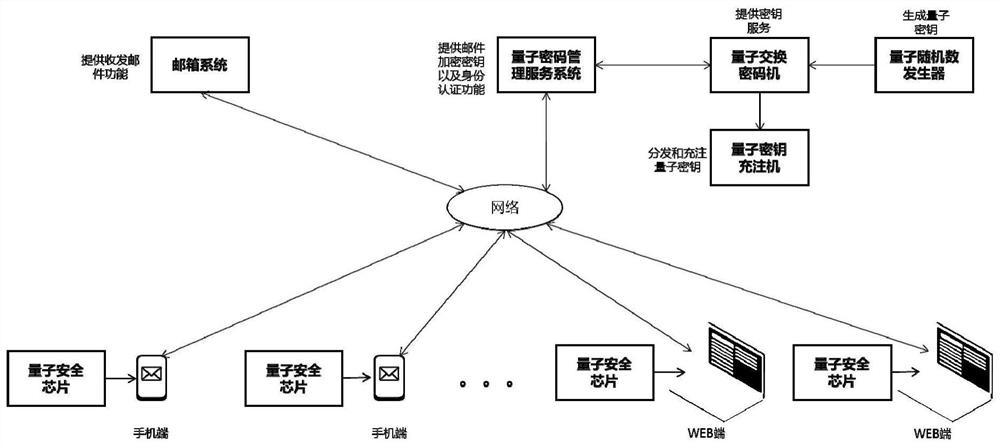
[0127] Such as figure 1 As shown, this embodiment discloses a method for transmitting mail based on quantum security keys, using a transmission system for mail based on quantum security keys, the system includes:
[0128] Mailbox system, used to provide the function of sending and receiving emails;
[0129] A quantum random number generator for generating quantum keys;
[0130] The quantum exchange cipher machine receives the quantum key issued by the quantum random number generator to provide key services. The quantum exchange cipher machine has a key pre-stored in it, which is the key pre-generated by the quantum random number generator. And stored in the quantum exchange cipher machine, and the key in the quantum security chi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com