Isolation defense system for website security access
A security access and defense system technology, applied in the field of website security access, can solve problems such as data loss, attack bypass, and hanging horses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
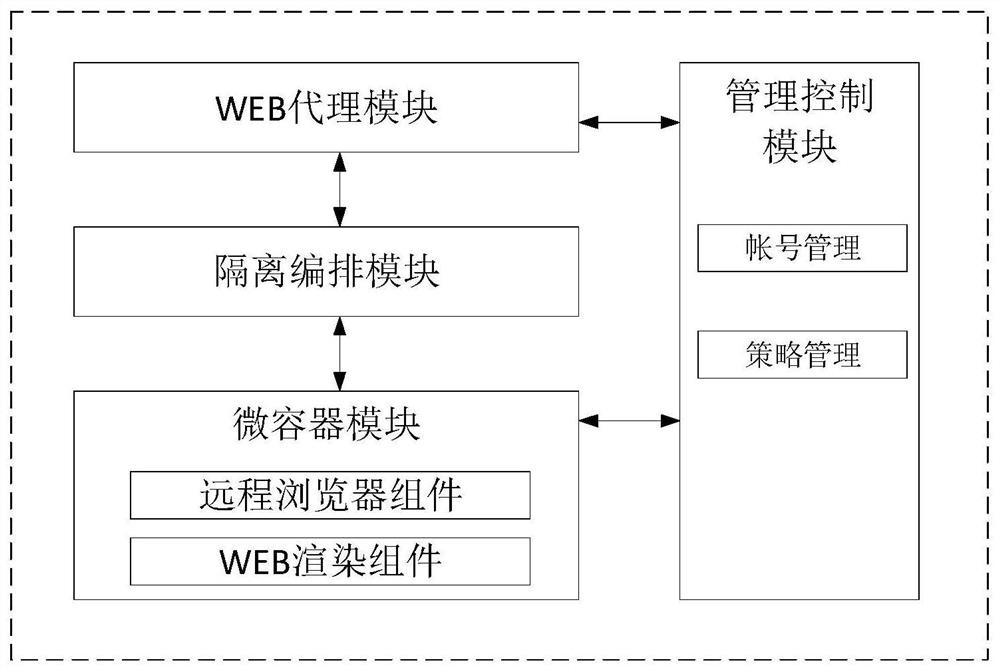
[0024] Basic as attached figure 1 And attached figure 2 As shown, an isolation defense system for secure access to websites includes a management control module, a Web proxy module, an isolation orchestration module, and a micro-container module. The management control module includes account management components and policy management components, and the micro-container module includes Web rendering component and remote browser component.
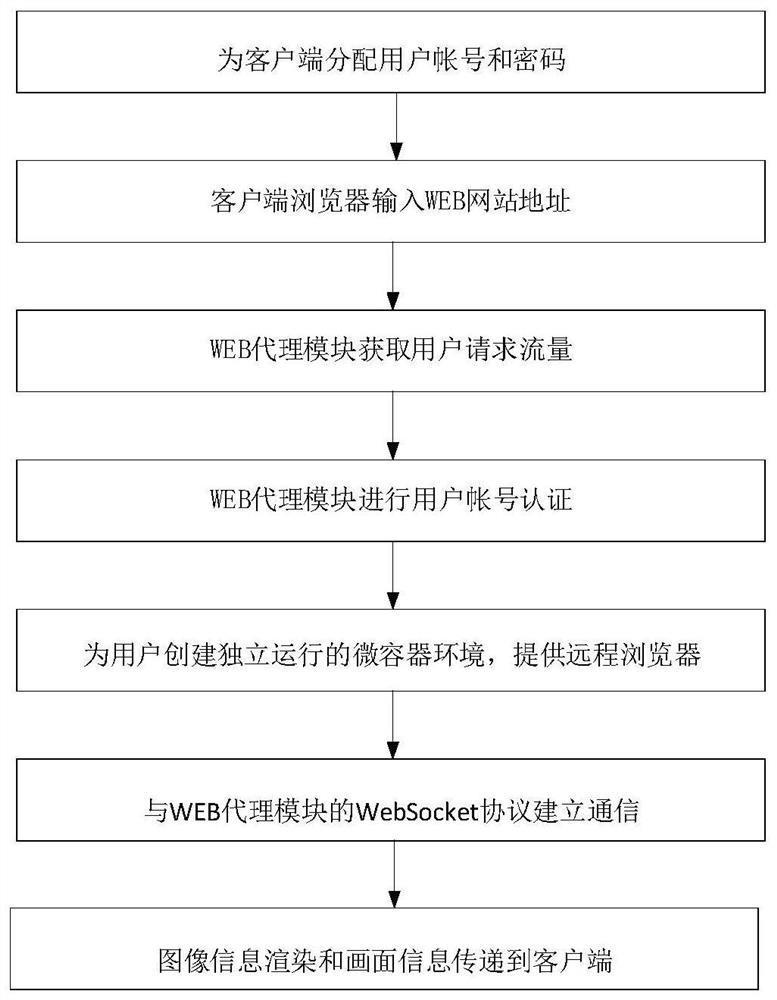
[0025] The account management component pre-allocates the corresponding account and password for each client, and establishes the association between the account and the remote browser type, and the remote browser type is associated with the micro container; the policy management component is used for the client to control the access to the Web site Policies, such as whitelist, blacklist, clipboard permissions, and file download; provide system administrator access and configuration interfaces based on B / S architecture, and are protected...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com