Method for secure data transmission and legal node authentication in wireless sensing network
A secure data and wireless sensing technology, applied in digital transmission systems, security devices, transmission systems, etc., can solve problems such as security failure, cracking, and measurement matrix leakage, so as to avoid replay attacks, achieve confidentiality, and reduce additional The effect of spending
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] In order to better understand the technical solution, the method of the present invention will be described in detail below in conjunction with the accompanying drawings.
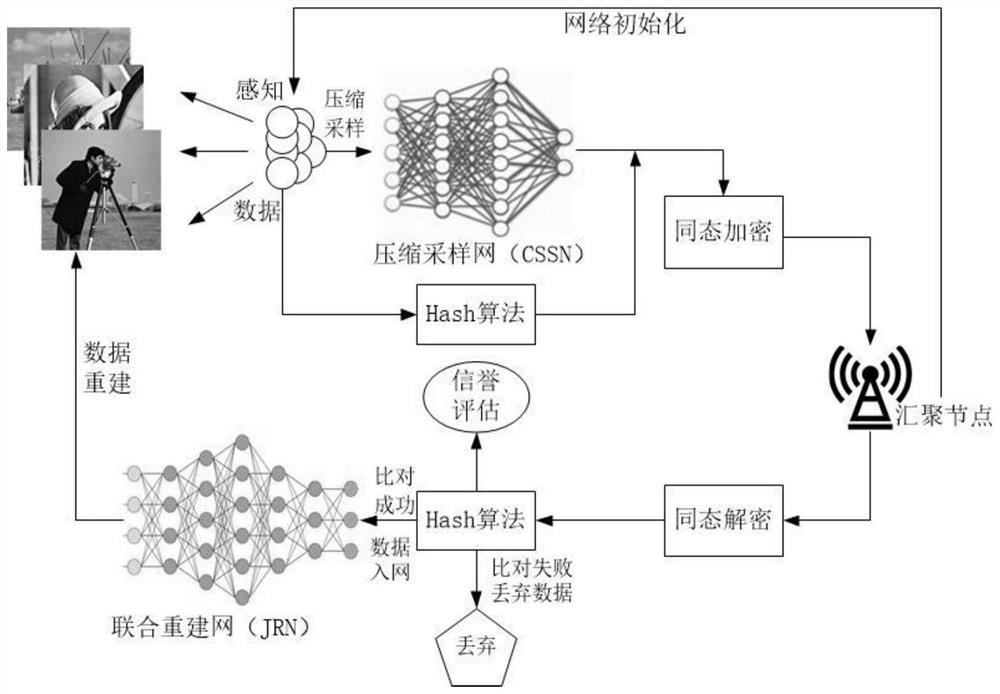
[0042] The present invention provides a method for secure data transmission and legal node authentication in a wireless sensory network. The overall process is shown in the attached figure 1 shown, including the following steps:
[0043] S1. Perform a network initialization process;
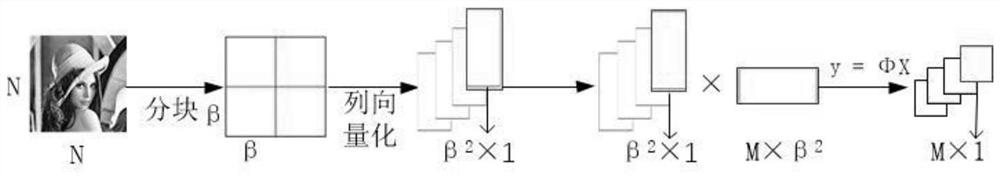
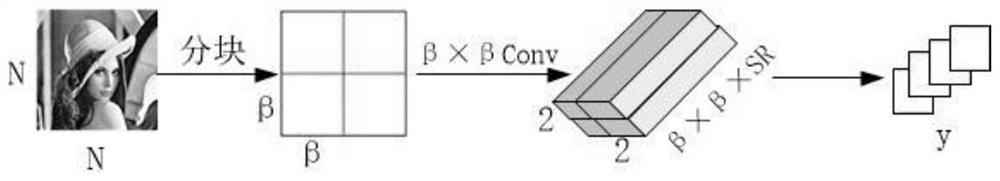
[0044] S2. At the perception node side, first sample and compress the data with the Compressed Sampling Network (CSSN), and then process the data with the light-weight Hash algorithm set in advance. The processed data is added to the sampled and compressed data and applied to Paillier addition. Homomorphic encryption, transmitted to the sink node;
[0045] S3. At the converging node, decrypt first, perform Hash comparison, and decide whether to keep the data. If the comparison is successful, send the data to the Joint...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com