Out-of-band security BIOS password management method and device, terminal and storage medium
A security management and password technology, applied in the field of BIOS password management, can solve problems such as poor security, and achieve the effects of easy maintenance, low operating cost, good versatility and adaptability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
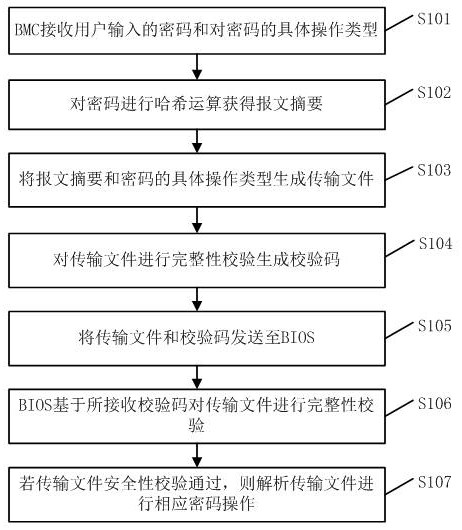
[0061] Embodiment 1 provides a method for out-of-band security management of BIOS passwords, the out-of-band password management has a verification mechanism and encrypted transmission function, and effectively improves the serviceability and security of BIOS password management.
[0062] Such as figure 1 Shown is a schematic flowchart of a method for out-of-band security management of BIOS passwords provided by Embodiment 1, which includes the following steps.
[0063] S101. The BMC receives a password input by a user and a specific operation type for the password.
[0064] The password entered by the user and the specific operation type on the password are received by the BMC. Wherein, the specific operation type on the password refers to operations such as setting, modifying or deleting the password.
[0065] S102. Perform a hash operation on the password to obtain a message digest.
[0066] S103, generating a transmission file for the specific operation type of the mess...
Embodiment 2
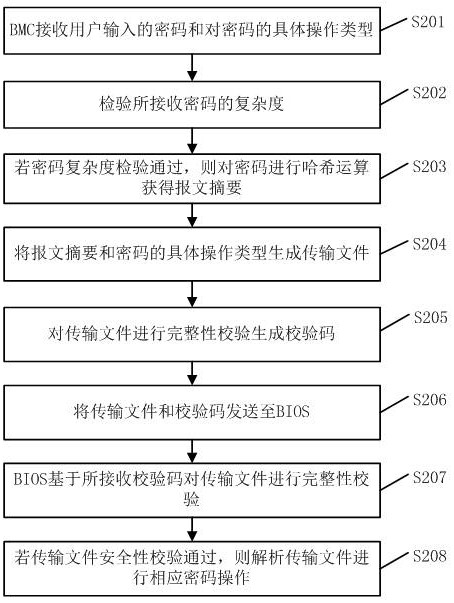
[0079] In order to further improve security, the second embodiment provides a method for out-of-band security management of BIOS passwords, adding password complexity checks to ensure that the passwords have sufficient complexity and increase the difficulty of deciphering.
[0080] Such as figure 2 Shown is a schematic flowchart of a method for out-of-band security management of BIOS passwords provided by Embodiment 2, including the following steps.
[0081] S201. The BMC receives a password input by a user and a specific operation type for the password.
[0082] S202. Check the complexity of the received password.
[0083] S203. If the password complexity check passes, perform a hash operation on the password to obtain a message digest.
[0084] For example, the complexity of the password needs to meet the following conditions:
[0085] 1> At least 8 characters in length;
[0086] 2> Contain at least one uppercase and lowercase letters, numbers and special characters;
...
Embodiment 3
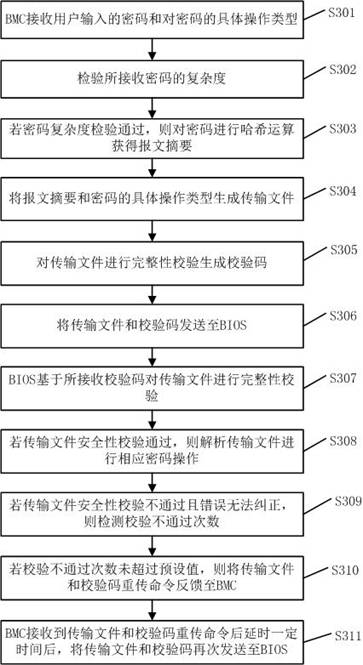
[0098] In order to improve work efficiency, a method for out-of-band security management BIOS password provided by the third embodiment, after the BIOS fails to verify the integrity of the transmitted file and cannot correct the error, automatically requires the BMC to retransmit and perform the integrity verification again. test.
[0099] Such as image 3 Shown is a schematic flowchart of a method for out-of-band security management of BIOS passwords provided by the third embodiment, including the following steps.
[0100] S301. The BMC receives a password input by a user and a specific operation type for the password.
[0101] S302. Check the complexity of the received password.
[0102] S303. If the password complexity check passes, perform a hash operation on the password to obtain a message digest.
[0103] Password complexity verification increases the difficulty of deciphering passwords, making it difficult for the server to be invaded by network attacks such as viru...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com