Quantum encryption communication system based on power distribution terminal equipment, and use method thereof
A power distribution terminal and quantum encryption technology, applied in key distribution, can solve problems such as increasing additional use costs, information theft, and difficulty in measuring security performance, and achieve the effects of increasing the difficulty of cracking, improving security, and increasing the frequency of supplementation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0070] Example 1: When image data is included in the transmission data:
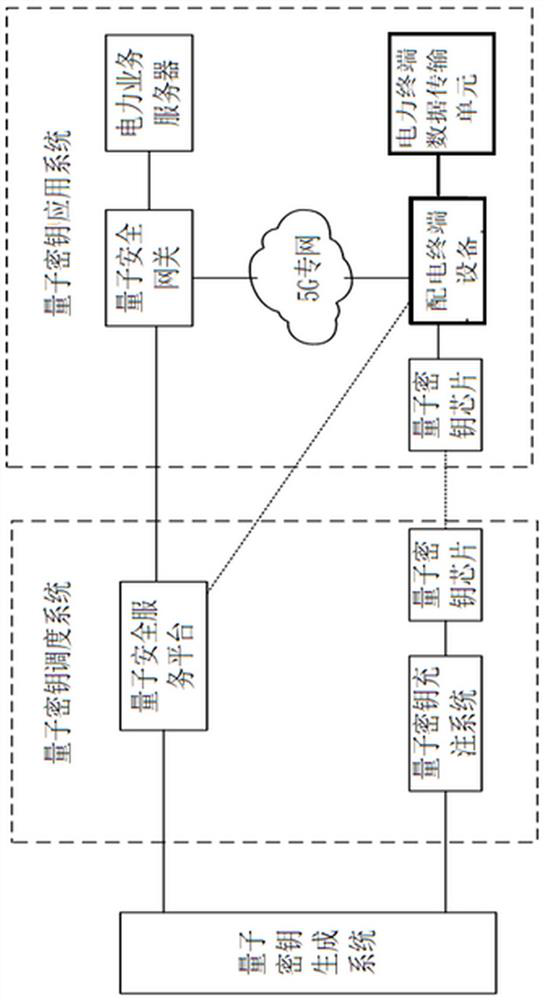
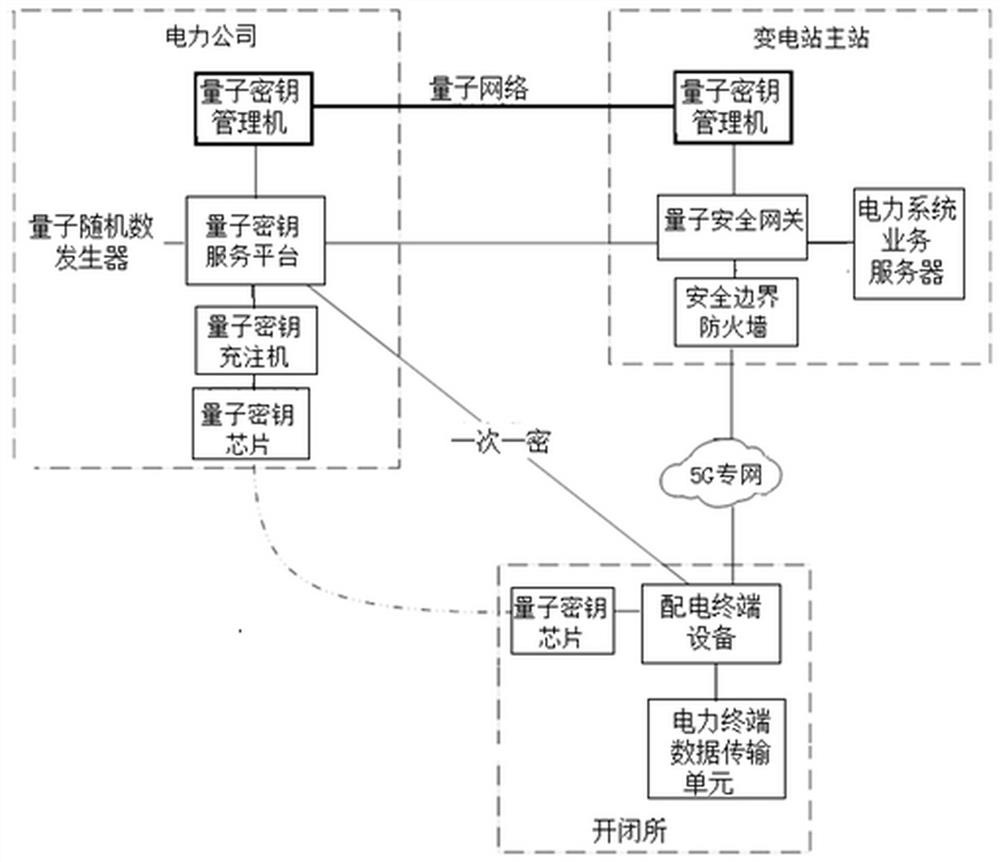
[0071]An encrypted communication system for power distribution terminals based on quantum encryption. Both the quantum key generation system and the quantum key scheduling system are installed in the power company building, and the quantum key generation system uses a quantum random number generator. The system serves Quantum Encryption of Communications between a Switchboard and Substation Master.
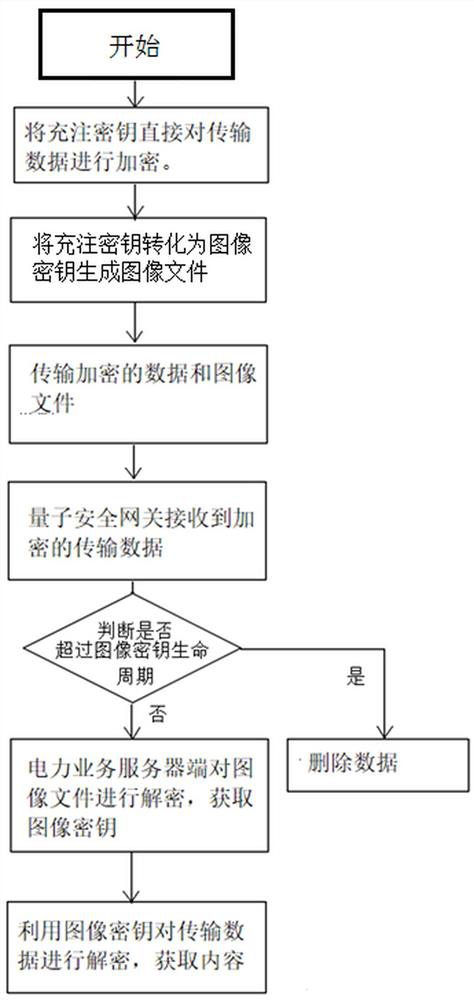
[0072] In order to ensure the security of the main station of the substation, a security boundary firewall is also installed on the side of the quantum security gateway. The power distribution terminal equipment on the switching station side first loads the charging key through the U-shield. The transmission data includes the power maintenance aerial pictures of the iron tower taken by the drone, such as figure 2 , image 3 As shown, it includes the step of obtaining the filling key by the power distribu...
Embodiment 2
[0089] Embodiment 2: When the transmission data does not include image data.
[0090] The device configuration and transmission process are the same as those in Embodiment 1, and will not be repeated here. The encryption process is: convert the filling key to generate an image as the image key for encrypting the transmitted data. The specific steps are: record the filling key as a one-dimensional array img, and convert each Convert the number to get the array img1={p 01 ,p 02 ,p 03 ,p 04 ,p 05 ,p 06 ,...,p 21 ,p 22 ,p 23 ,p 24 ,...,p n*24}, where p 01 is the first red component sub-pixel value of the first pixel, p 02 is the first green component sub-pixel value of the first pixel, p 03 is the first blue component sub-pixel value of the first pixel, p 04 is the second red component sub-pixel value of the first pixel, p 05 is the second green component sub-pixel value of the first pixel, …, p 24 is the 8th blue component sub-pixel value of the first pixel, p n*...
Embodiment 3
[0101] Example 3: When transferring larger files.
[0102] Usually when there is a large amount of transmission data, the transmission data is divided into multiple encrypted packages, and each encrypted package needs to be configured with an image key generated by filling the key separately, and the generation time of the encrypted package is earlier than the generation time of the image key and The transmission time of the encrypted package is shorter than the life cycle of the corresponding image key. The image of the image key has a time stamp, and the time stamp includes the generation time of the image key and the life cycle of the image key. The entire data package will self-destruct as soon as it exceeds the lifetime of the image key. In the actual operation process, both the power service server and the quantum security gateway can read the life cycle information of the image key, and compare the generation time of the image key with the time in the device. The actua...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com