Block chain address transformation and identity authentication method and device and storage medium
A technology of identity authentication and blockchain, applied in the direction of instruments, payment systems, payment architecture, etc., can solve problems such as parallel acceleration
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0027] This embodiment provides a method for modifying a blockchain address, which is applicable to a blockchain system client, and the method includes:
[0028] S1. Obtain the address information of the address to be transformed in the blockchain system;
[0029] S2. Generate an identity hash locally, and register the identity hash in the corresponding address to be transformed according to the address information;
[0030] Wherein, the identity hash is obtained by performing N hash operations on the first random character string, identity information and private information, and the number of operations N is set by the user, and the first random character string is obtained from the server end of the blockchain system Obtain and store correspondingly with the address information in the block chain system, the identity information includes one or more of ID number and mobile phone number.
[0031] In the above scheme, firstly, the address of the blockchain system is transfor...
Embodiment 2
[0043] A computer device comprising: one or more processors; memory for storing one or more programs which, when executed by the one or more processors, cause the The one or more processors execute the method as described in Embodiment 1.
[0044] A storage medium storing a computer program, when the program is executed by a processor, implements the method described in Embodiment 1 above.
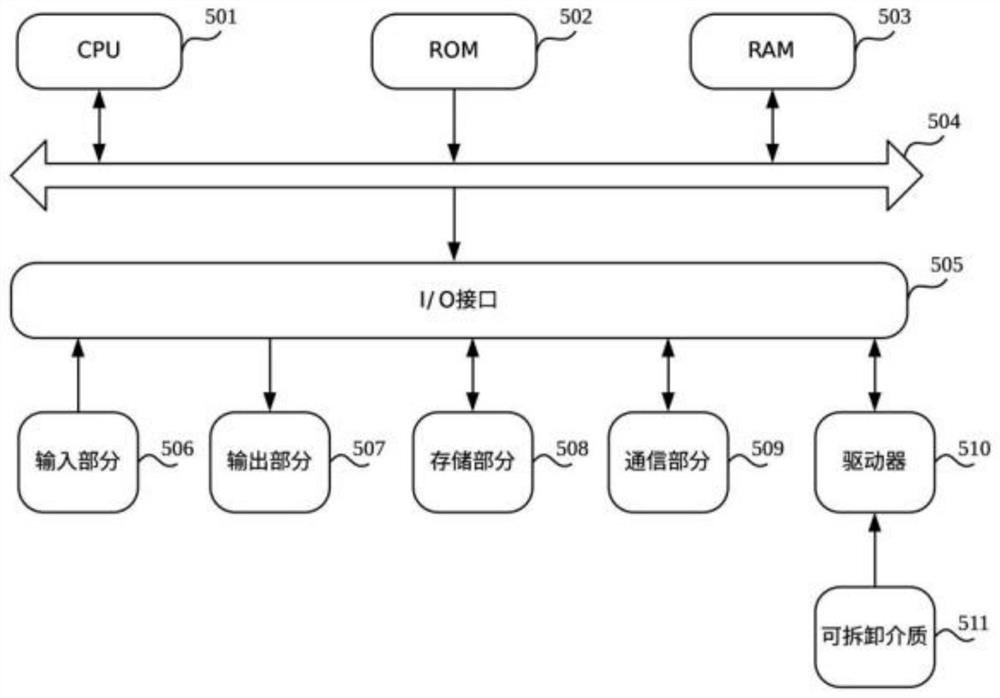
[0045] figure 1 A schematic structural diagram of a device provided in this embodiment.
[0046] like figure 1 As shown, as another aspect, the present application also provides a computer device 500, including one or more central processing units (CPU) 501, which can be The program loaded into the random access memory (RAM) 503 by the part 508 executes various appropriate actions and processes. In the RAM 503, various programs and data necessary for the operation of the device 500 are also stored. The CPU 501 , ROM 502 , and RAM 503 are connected to each other via a bus 504 . An inp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com