Private key distribution method and device, private key decryption method and device, equipment and medium
A technology of private keys and devices, applied in the field of information security, can solve problems such as private key leakage and affect information security, and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
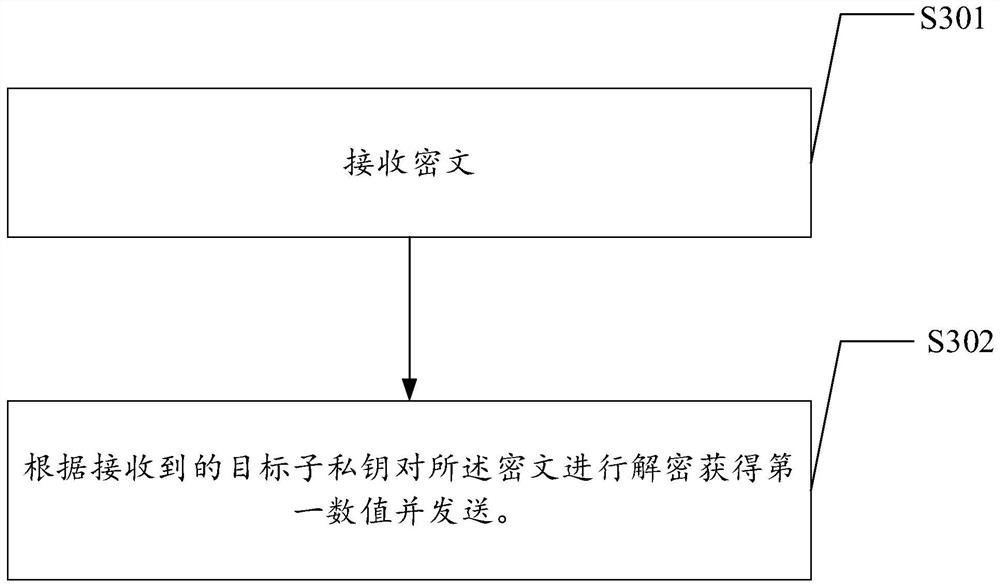
[0040] In order to reduce the risk of private key leakage and protect the security of information, embodiments of the present invention provide a private key distribution and decryption method, apparatus, device and medium.
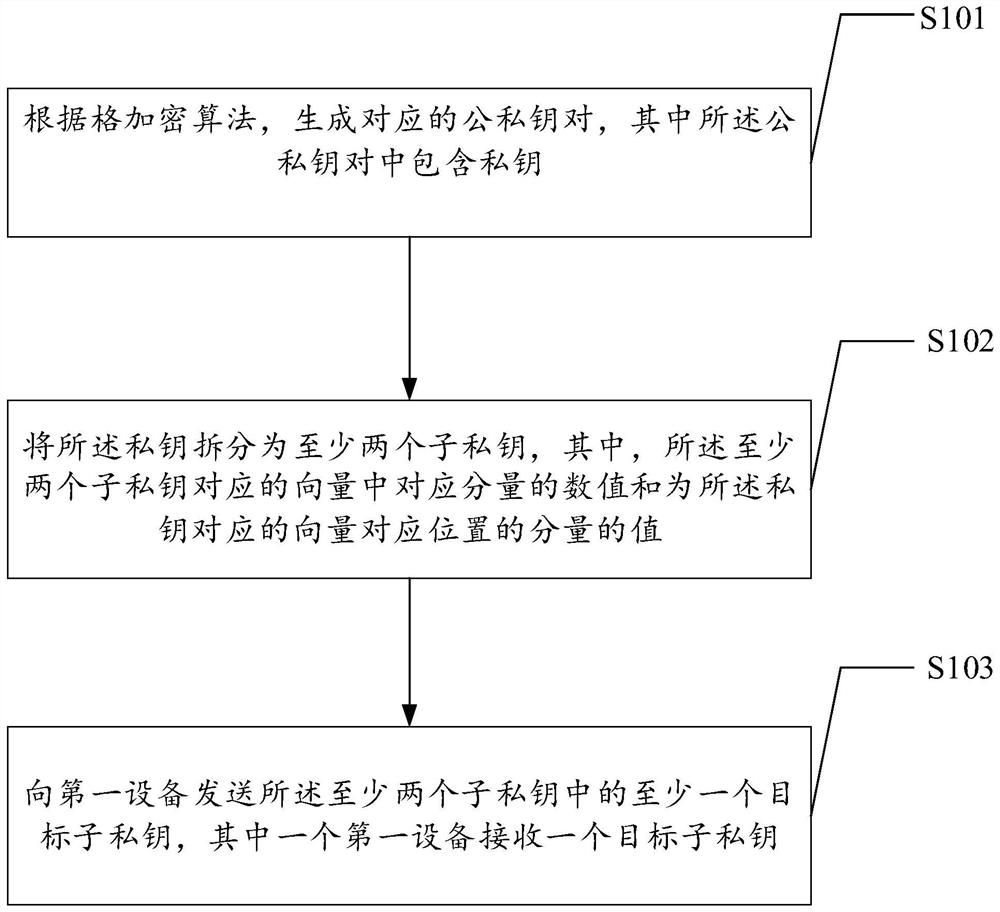
[0041] figure 1 A schematic diagram of a process of a private key distribution method provided by an embodiment of the present invention, the process includes the following steps:
[0042] S101: Generate a corresponding public-private key pair according to a lattice encryption algorithm, wherein the public-private key pair includes a private key.
[0043] The private key distribution method provided by the embodiment of the present invention is applied to an electronic device, and the electronic device may be a device such as an intelligent terminal, a PC, or a server.
[0044] In order to ensure the security of information, the file or information to be transmitted may be encrypted at the sending end based on an encryption algorithm, and the encrypted f...
Embodiment 2
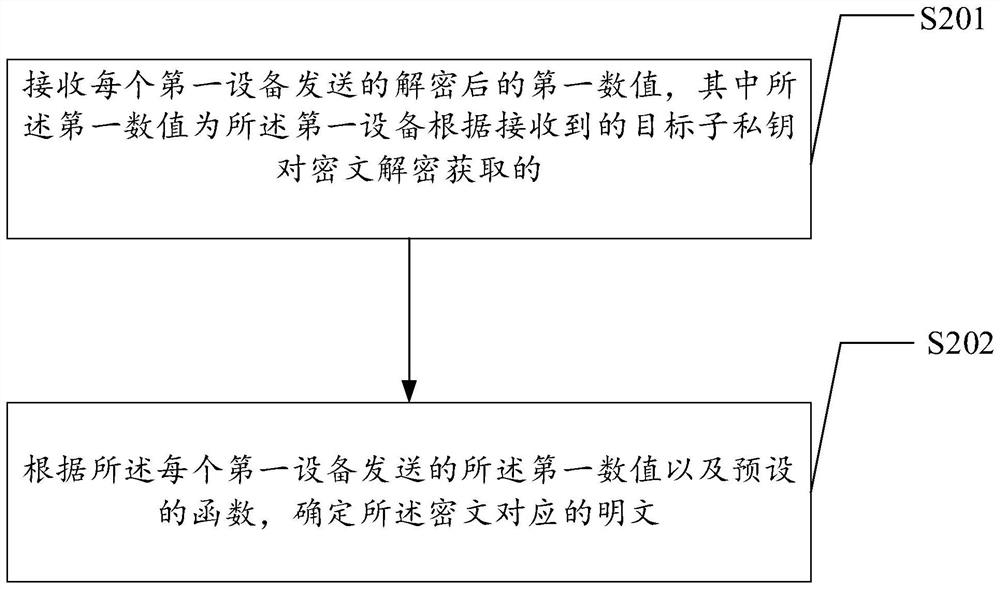
[0059] In order to encrypt the plaintext and generate the corresponding ciphertext, on the basis of the above embodiment, in the embodiment of the present invention, after the corresponding public-private key pair is generated, the method further includes:
[0060] Publish the public key contained in the public-private key pair.
[0061] After the corresponding public-private key pair is generated according to the lattice encryption algorithm, in order to realize that the electronic device where the encryptor is located can encrypt the file or information to be transmitted, that is, in order to realize that the encryptor encrypts the plaintext and generates the corresponding ciphertext , in this embodiment of the present invention, after obtaining the public-private key pair, the electronic device publishes the public key included in the public-private key pair.
Embodiment 3
[0063] In order to realize that the sub-private keys can be stored in different devices and reduce the risk of private key leakage, on the basis of the above embodiments, in this embodiment of the present invention, the at least two sub-private keys are sent to the first device. At least one target sub-private key in the key includes:
[0064] Each of the at least two sub-private keys is determined as a target sub-private key, and the at least two target sub-private keys are respectively sent to the corresponding at least two first devices.
[0065] In order to realize that there is no risk of private key leakage when one device or several devices are hacked, the split sub-private keys can be stored in different devices. In this embodiment of the present invention, the at least two private keys can be Each of the sub-private keys is determined as the target sub-private key, and the at least two target sub-private keys are sent to the corresponding at least two first devices, t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com