Protection against network-initiated attacks
A network interface card, Internet protocol technology, applied in the field of protection from network-initiated attacks, which can solve problems such as unavailability, high computing resources, processor overload, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
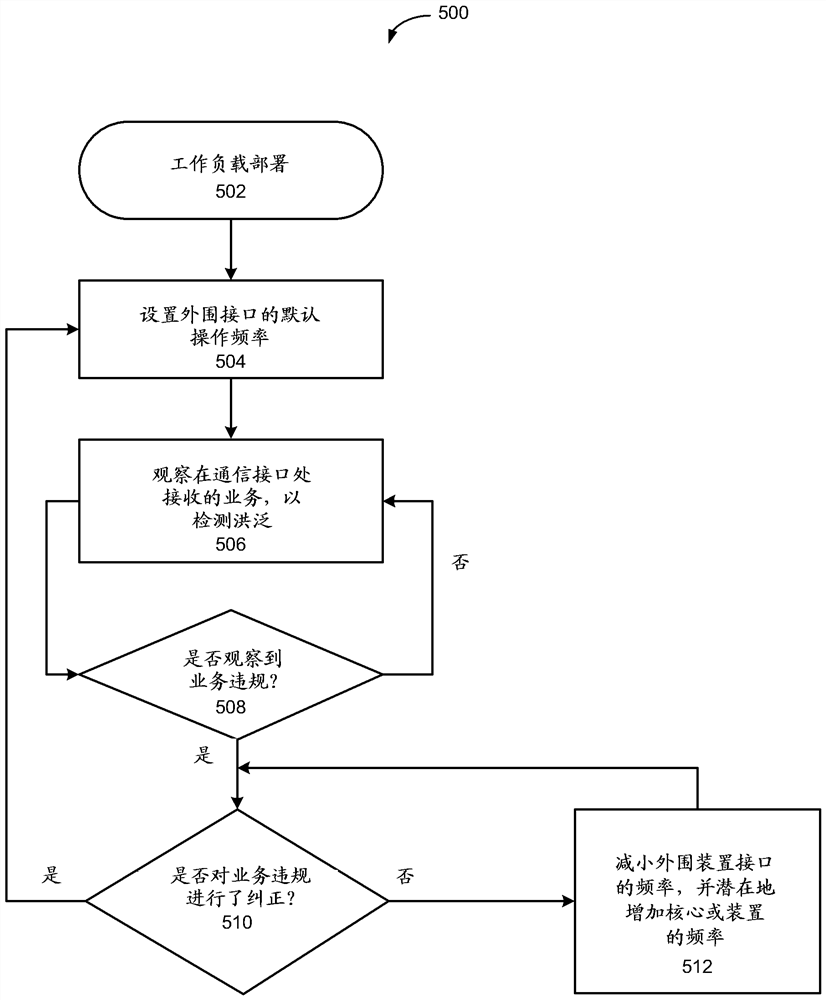
[0120] Example 1 includes a method that includes changing an operating frequency of a peripheral device interface between a network interface card and a processor based on detecting a traffic violation.
example 2
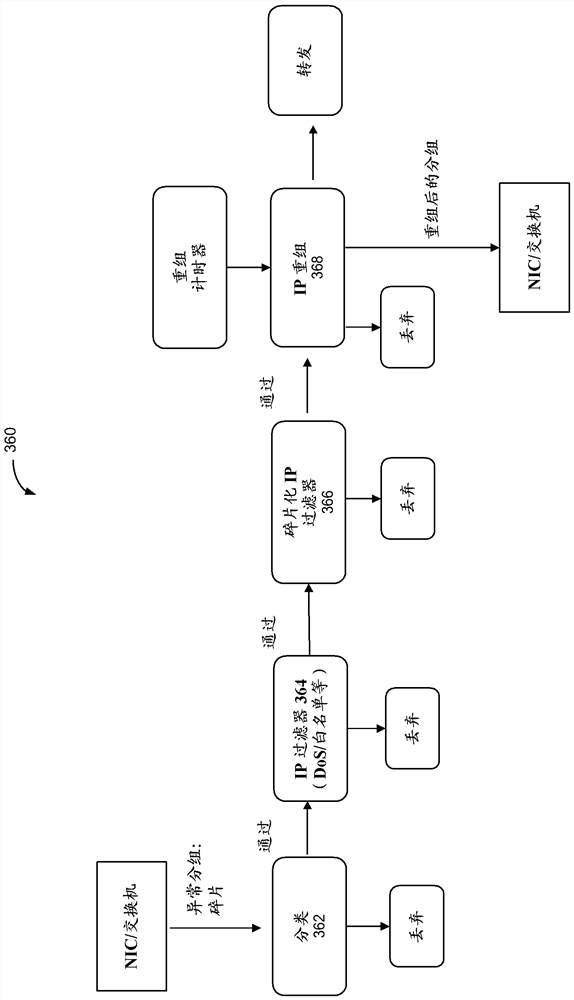
[0121] Example 2 includes any of the examples and includes detecting a traffic violation based on detecting IP packet fragmentation, wherein altering a frequency of operation of a peripheral device interface between the network interface card and the processor based on detecting the traffic violation includes The operating frequency of the peripheral device interface between the network interface card and the processor is reduced.
example 3
[0122] Example 3 includes any examples where IP packet fragmentation includes one or more of the following: IP packet fragmentation that is an incomplete packet, IP packet fragmentation that is too small, IP packet fragmentation that results in excess packets, or a full IP packet fragmentation buffer .
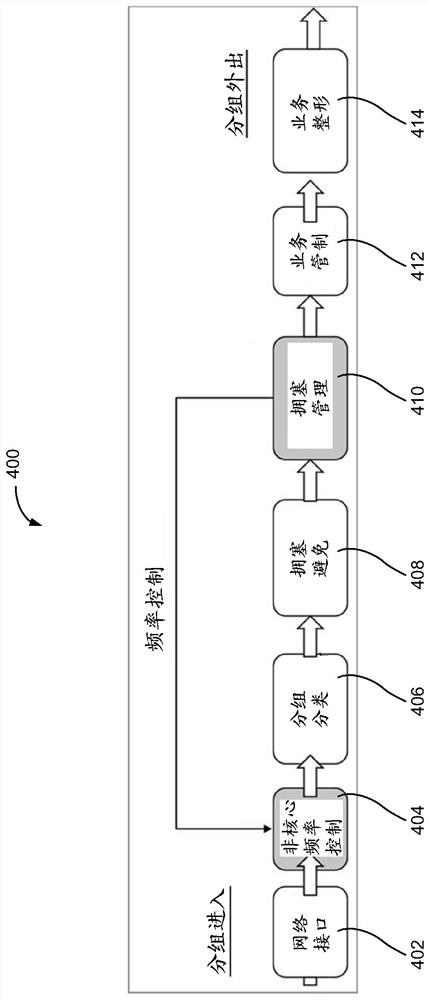
[0123] Example 4 includes any examples wherein detecting a traffic violation based on detecting IP packet fragmentation includes detecting a traffic violation based on detecting IP packet fragmentation at one or more of: a network appliance, a network interface card, a non-core, a system agent, operating system, application, or computing platform.
[0124] Example 5 includes any examples wherein the peripheral device interface includes one or more of: system agent, uncore, bus, peripheral component interconnect express (PCIe) interface, and cache.
[0125] Example 6 includes any examples where the peripheral device interface is part of a system on chip (SoC), and the SoC incl...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap