Virtual machine migration system and method
A virtual machine migration and virtual machine technology, applied in the field of network security, can solve the problems of inability to migrate session information at the same time, virtual firewall policy redundancy, and low policy matching performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
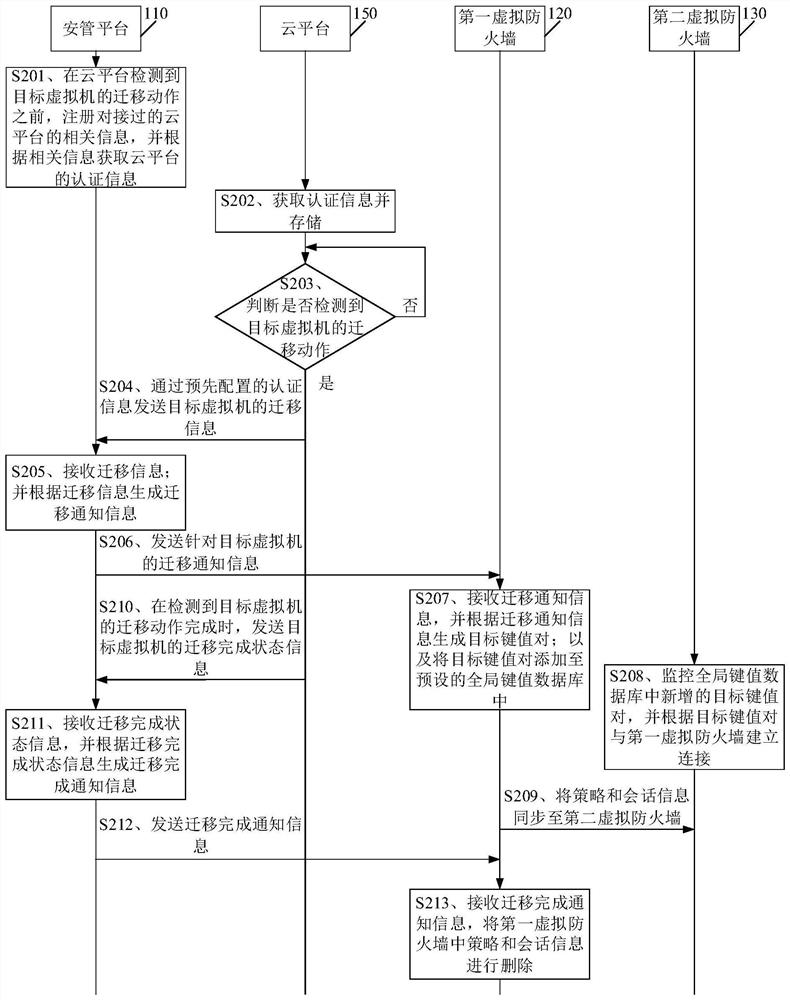
[0054] Please see figure 1 , figure 1 A schematic flowchart of a virtual machine migration system is provided for the embodiment of the present application. Wherein, the virtual machine migration system includes a security management platform 110 , a first virtual firewall 120 , a second virtual firewall 130 , a target virtual machine 140 and a cloud platform 150 .
[0055] S201. Before the cloud platform 150 detects the migration action of the target virtual machine 140, the security management platform 110 registers relevant information of the connected cloud platform 150, and obtains authentication information of the cloud platform 150 according to the relevant information.
[0056] In the embodiment of the present application, the authentication information includes the virtual machine migration notification function and the communication address of the security management platform 110, etc., which is not limited in the embodiment of the present application.
[0057] In ...
Embodiment 2
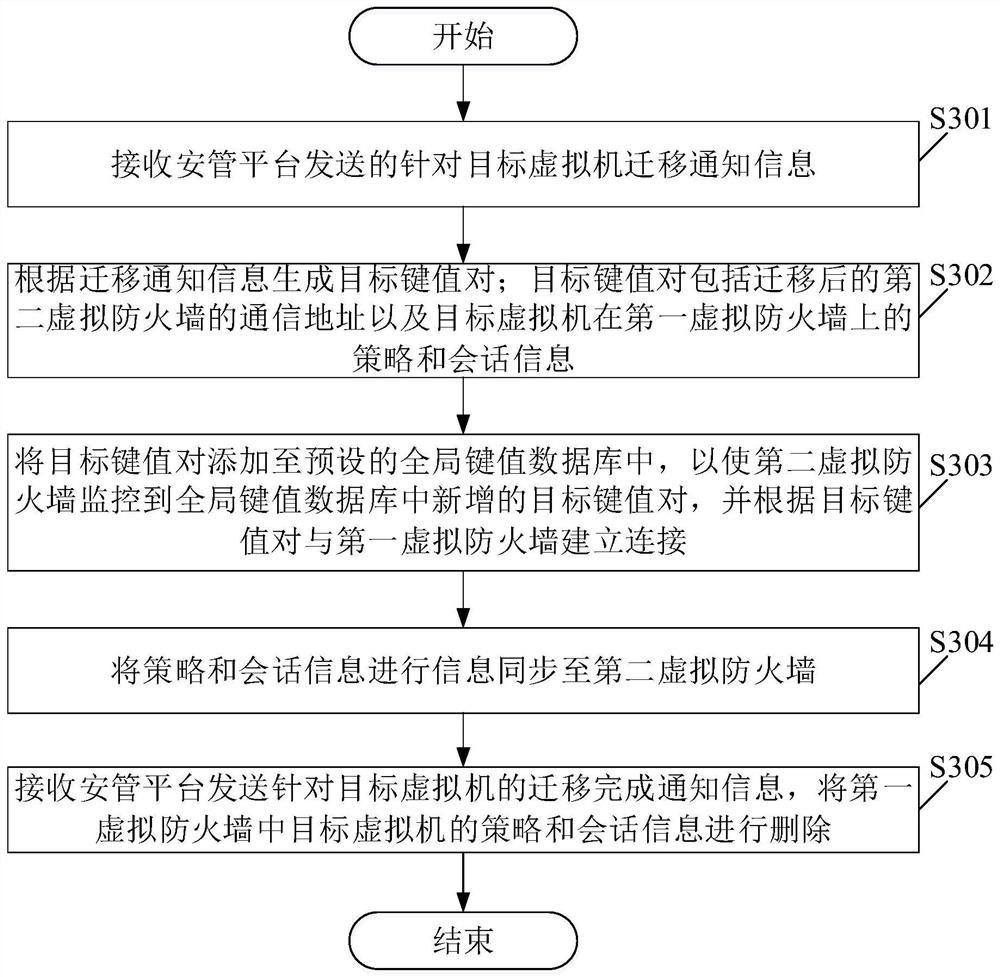
[0112] Please see figure 2 , figure 2 It is a schematic flowchart of another virtual machine migration method provided in the embodiment of the present application. like figure 2 As shown, wherein the virtual machine migration method is applied to the first virtual firewall 120 shown in Embodiment 1, including:
[0113] S301. Receive migration notification information for the target virtual machine 140 sent by the security management platform 110 .
[0114] S302. Generate a target key-value pair according to the migration notification information; the target key-value pair includes the communication address of the migrated second virtual firewall 130 and policy and session information of the target virtual machine 140 on the first virtual firewall 120 .
[0115] S303. Add the target key-value pair to the preset global key-value database, so that the second virtual firewall 130 monitors the newly added target key-value pair in the global key-value database, and according ...
Embodiment 3
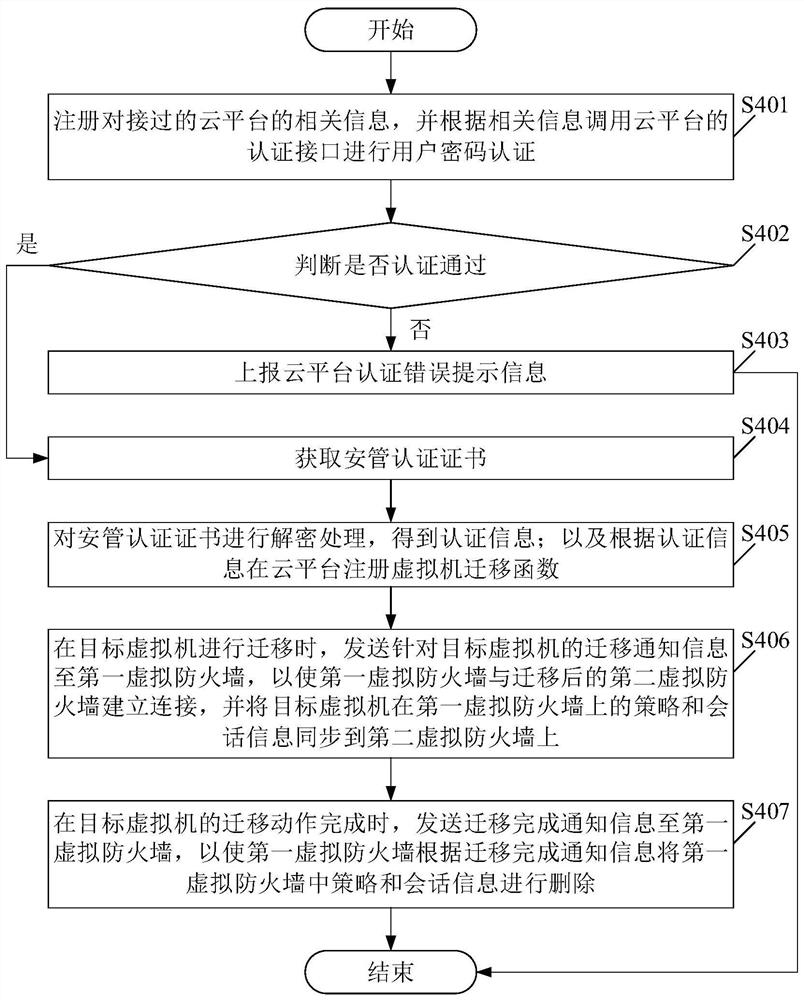
[0121] Please see image 3 , image 3 It is a schematic flowchart of a method for migrating a virtual machine provided in the embodiment of the present application. like image 3 As shown, the virtual machine migration method is applied to the safety management platform 110 of Embodiment 1, including:
[0122] S401. Register relevant information of the connected cloud platform 150, and call an authentication interface of the cloud platform 150 to perform user password authentication according to the relevant information.
[0123] S402. Determine whether the authentication is passed. If yes, perform steps S404 to S407; if not, perform step S403.
[0124] S403. Report the cloud platform 150 authentication error prompt information, and end this process.
[0125] S404. Obtain a safety management certification certificate.
[0126] S405. Decrypt the safety management certification certificate to obtain certification information; and register a virtual machine migration functio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com