Ciphertext-based numerical value security sorting method and system
A sorting method and sorting algorithm technology, applied in the field of information security, can solve problems such as inability to support multi-party data security sorting, sensitive information leakage, threats, etc., and achieve efficient ciphertext sorting, privacy protection, and security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
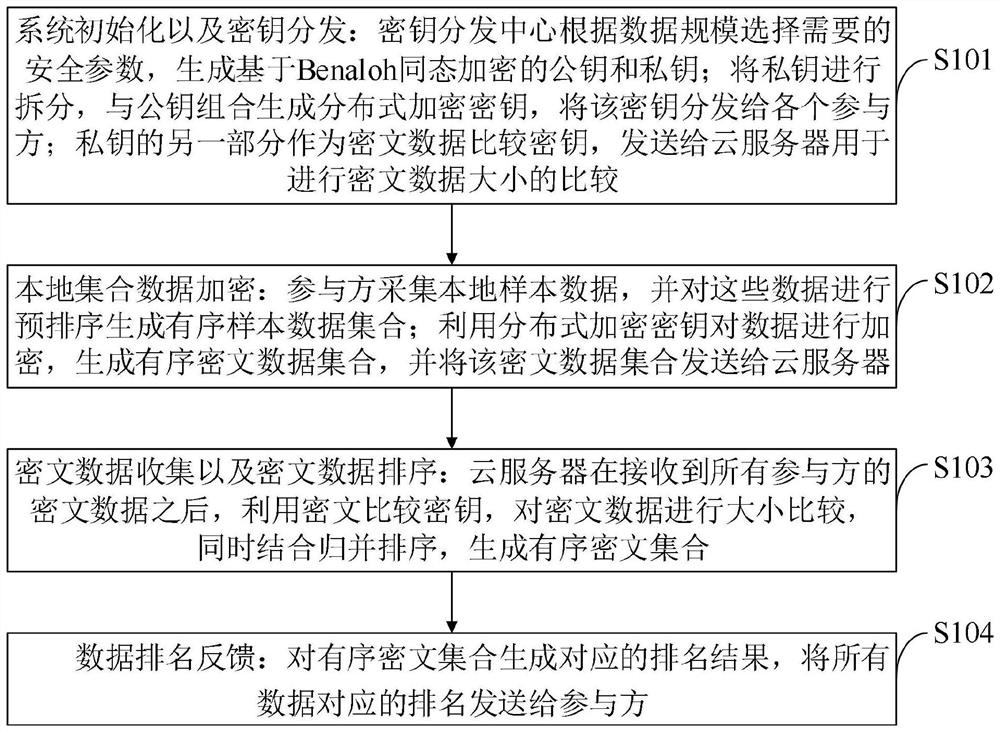
[0098] The purpose of the present invention is to propose a numerical security sorting method based on ciphertext for the deficiencies in data privacy and sorting efficiency of the existing security sorting system. In order to protect the local sensitive data of the participants, the present invention proposes a numerical security sorting method based on ciphertext. The user needs to preprocess and encrypt the data at the very beginning, and hand over the encrypted data to the cloud server for processing. There is no need to perform repeated data sorting operations. The cloud service provider completes the security sorting of ciphertext data, then generates rankings for the sorting results, and finally feeds back the corresponding data rankings to the participants.
[0099] Aiming at the purpose of protecting the privacy of data in the safe multi-party numerical sorting process, the present invention proposes a secure sorting method for ciphertext values based on a data compa...
Embodiment 2
[0105] The ciphertext-based numerical security sorting method provided by the embodiment of the present invention includes the following steps:
[0106] Step 1, system initialization and key distribution.
[0107] (1.1) Suppose the plaintext space is Z r ={0, 1, . . . , r / 2-1}, r is a positive integer.
[0108] (1.2) The key distribution center first selects two large prime numbers p and q, so that p and q satisfy r|(p-1), and gcd(r, q-1)=1, while letting n=pq,
[0109] (1.3) Optional Key Distribution Center Satisfy gcd(s,r)=1 and At the same time randomly select a hash function h( );
[0110] (1.4) Calculated by the key distribution center because gcd(s,r)=1 and The set of contains r-1 distinct values. For any i, if and only if , satisfy the condition 0<i<r / 2;
[0111] (1.5) The key distribution center generates the public key pk=(y, n, h( ), U) according to the above steps, and the private key Then send the public key and a part of the public key s as...
Embodiment 3
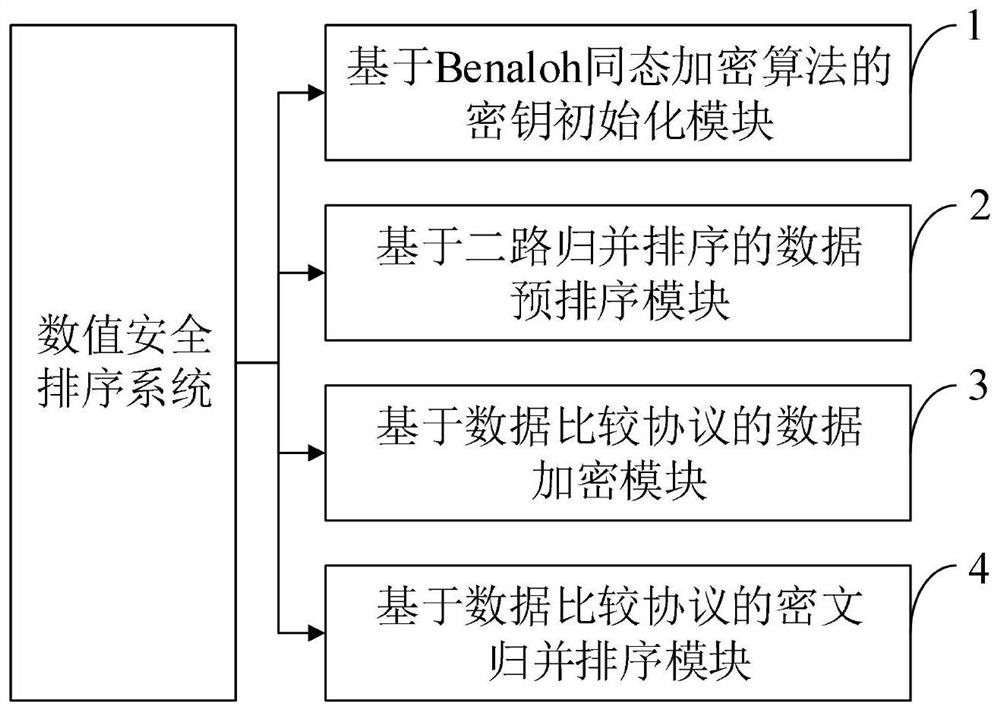
[0135] Another object of the present invention is to provide a ciphertext-based numerical security sorting system implementing the ciphertext-based numerical security sorting method, the ciphertext-based numerical security sorting system comprising:
[0136] Key initialization module based on Benaloh homomorphic encryption algorithm, data pre-sorting module based on two-way merge sorting, data encryption module based on data comparison protocol, ciphertext merge sorting module based on data comparison protocol;
[0137] Key initialization module based on Benaloh homomorphic encryption algorithm, including security parameter selection sub-module, key splitting and distribution sub-module, used for key distribution center to generate distributed encryption key and ciphertext data comparison key in the system initialization phase , and then distribute the distributed encryption key to the participants, and distribute the ciphertext data comparison key to the cloud server;
[0138...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com