AKA authentication method and system for 5G communication
An authentication method and authentication vector technology, applied in the field of 5GAKA authentication methods and systems, can solve the problems of lack of security protection, user data theft, fraudulent use by attackers, etc., to prevent user data leakage, prevent theft of key information, The effect of improving safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0066] Embodiment 1 of the present invention provides an AKA authentication method for 5G communication, which uses quantum keys to encrypt data transmission between 5G core network elements, and quantum keys can use quantum key distribution technology for 5G core network Shared quantum keys are distributed between network elements. Since quantum key distribution is based on quantum mechanics, it cannot be stolen and has true randomness. It can solve the problem of keys being stolen or cracked during the distribution process and improve key security. It can also securely distribute the quantum random number generated by the quantum random number server to network elements, and use it as a shared quantum key with high randomness.
[0067] During the main authentication and key negotiation process between the user equipment UE and the 5G core network, the mutual authentication between the UE and the network will be completed, and the key used between the UE and the serving networ...
Embodiment 2
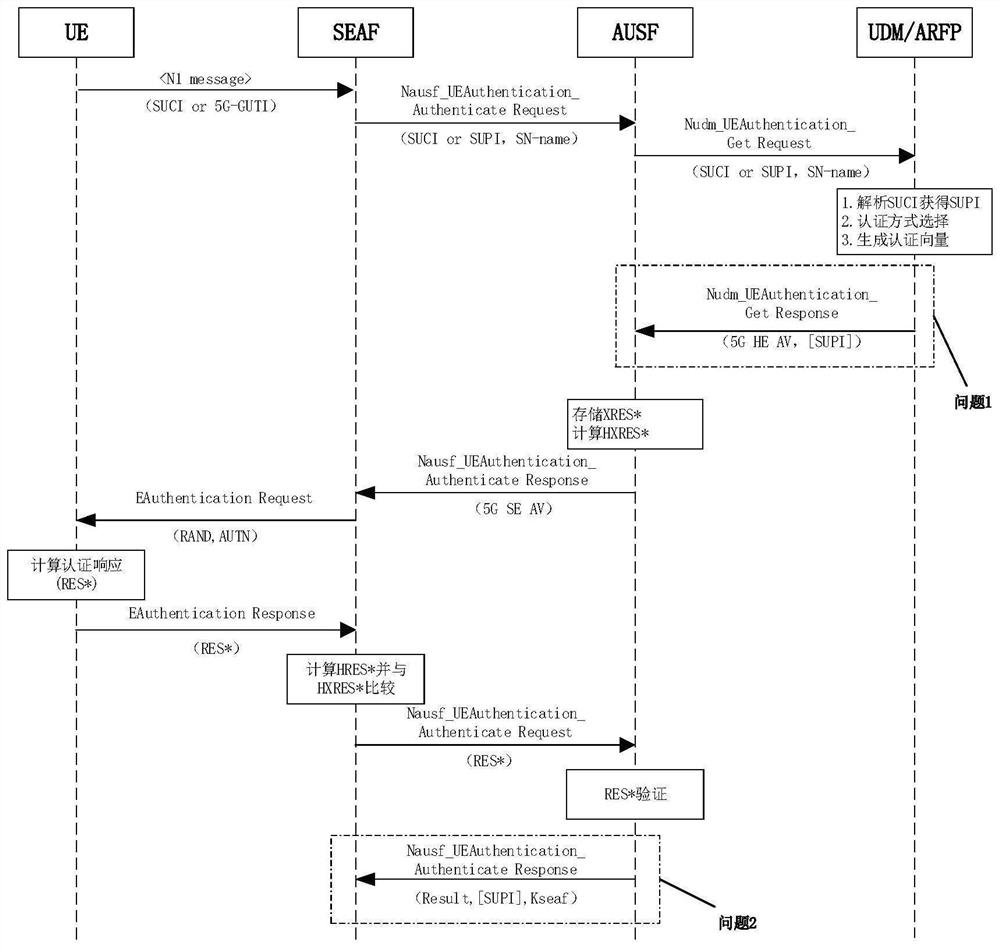
[0103] Embodiment 2 of the present invention provides a 5G AKA authentication system based on a shared key. In the 5G AKA authentication process, the 5G core network elements mainly involved include: SEAF (Security Anchor Function), AUSF (Authentication Server Function), UDM / ARFP (unified data management / authentication credential repository and processing functions).
[0104] Such as Figure 4 As shown, according to the actual deployment of the above three network elements, the corresponding quantum key distribution network is deployed, and the three network elements are connected to the three nodes of the quantum key distribution network to obtain the shared quantum key.
[0105] Among them, node 1 and node 2 of the quantum key distribution network can distribute the shared quantum key through the quantum key distribution technology, and provide the shared quantum key to the network elements SEAF and AUSF respectively in a secure manner, then SEAF A shared quantum key will b...
Embodiment 3
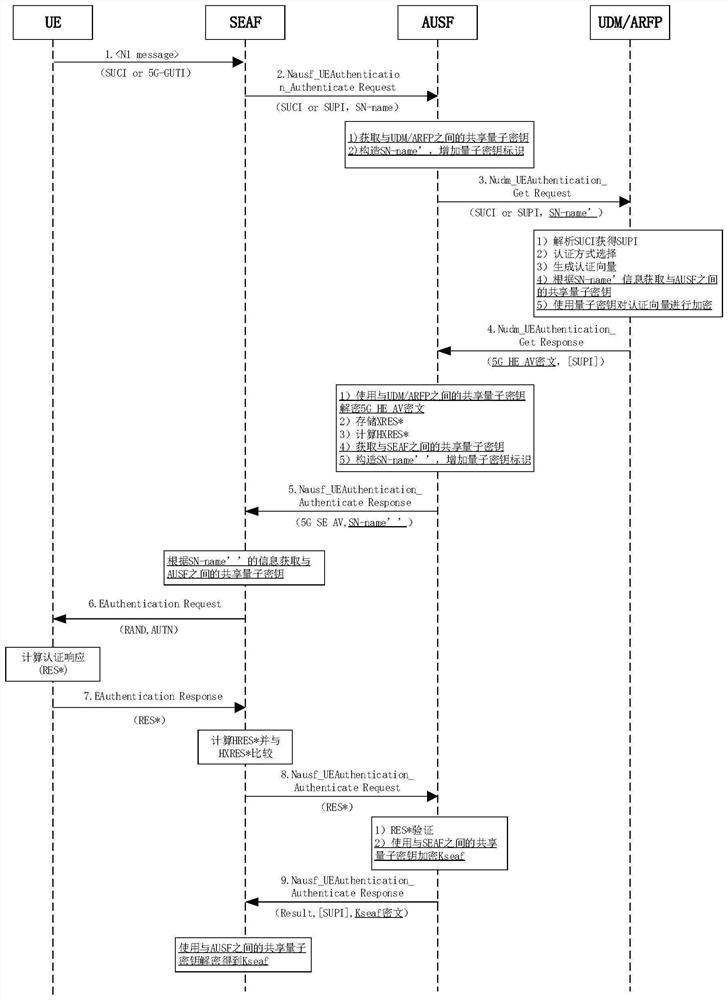
[0108] Embodiment 3 of the present invention provides a 5G AKA authentication system based on a shared key. In the 5G AKA authentication process, the 5G core network elements mainly involved include: SEAF (Security Anchor Function), AUSF (Authentication Server Function), UDM / ARFP (unified data management / authentication credential repository and processing functions).
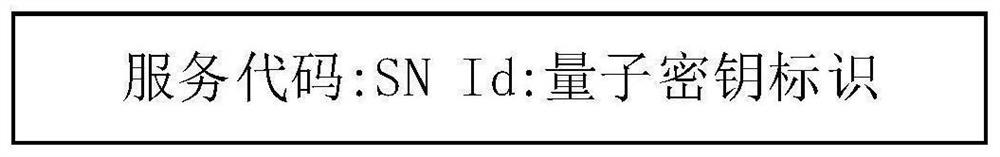
[0109] Connect the three network elements to the quantum random number server, preferably using a device-independent quantum random number server with high security, and obtain the shared quantum random number as an encryption key in a safe way, such as Figure 5 shown.
[0110] The quantum random number server distributes the common random number Rand1 between SEAF and AUSF in a secure way, and distributes the common random number Rand2 between AUSF and UDM / ARFP. The distribution method in the random number distribution process can use quantum key distribution technology The distributed shared quantum key is e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com