Code-free process visualization vulnerability detection method and system
A vulnerability detection and process technology, applied in the field of system security, to achieve the effect of simple and convenient testing and debugging, improving development and debugging efficiency, and reducing development capability requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
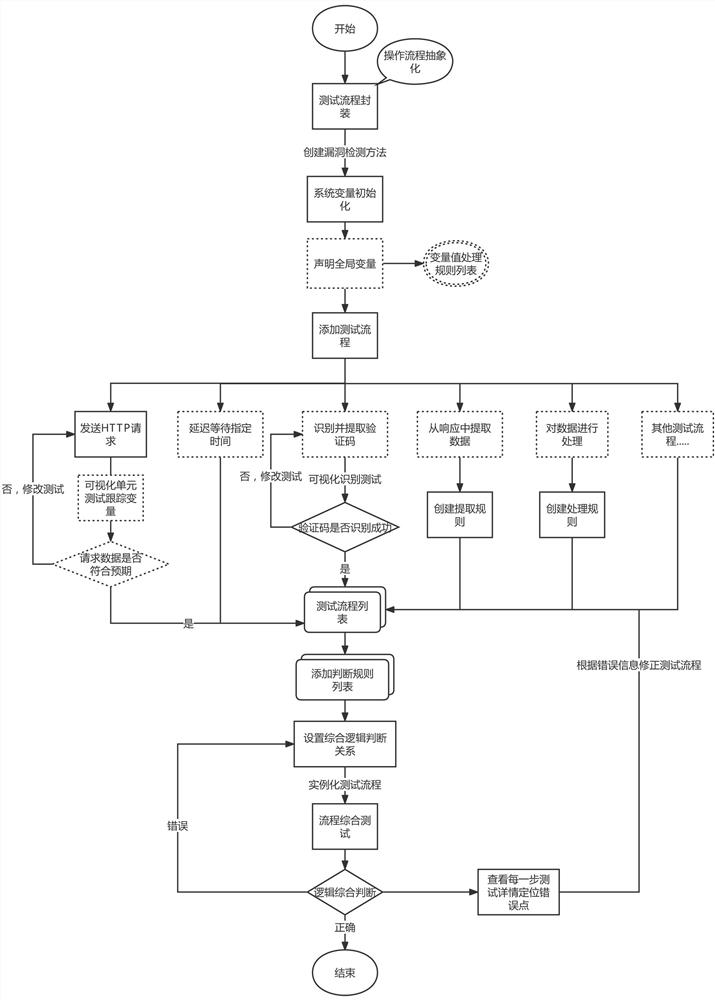
[0047] Such as figure 1 As shown (the dotted line box in the drawing is an unnecessary process), the present invention proposes a code-free process visualization vulnerability detection method, including:
[0048] S1: Firstly, abstract and encapsulate the testing process of various tests in vulnerability scanning into an interface, and build different system variables for different testing processes to bind the result data of the testing process with the next testing process and logical judgment Medium; also includes setting global variables: users create global variables through the visual form, and assign values to global variables, and support adding processing rules to global variables. The processing rules include: prefix, suffix, reverse, interception, encoding string and decoding string. The processing rules take effect before the global variable is referenced.
[0049] The present invention can insert global variables through a visual interface in creating test pro...
Embodiment 2
[0077] Embodiment 2: as figure 1 As shown (the dotted line frame in the accompanying drawing is a non-essential process flow), the specific steps of the present invention include:
[0078] 1. Test process encapsulation: abstract and encapsulate the test process in the vulnerability test process into an interface, and encapsulate vulnerabilities such as sending HTTP requests, delaying waiting for a specified time, identifying and extracting verification codes, extracting data from responses, and processing data, etc. Commonly used test procedures in scanning, and more test procedures can be expanded through the interface.
[0079] 2. System variable design: Most of the test processes will generate corresponding execution results after the execution is completed, so the program encapsulates some system variables such as: binding R-type variables that send HTTP request results, binding identification and extraction verification The Y type variable of the code result, the E type ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com